Method and device for executing data service
A technology of data service and execution method, applied in the field of communication, can solve the problem of unbalanced use of data package traffic, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
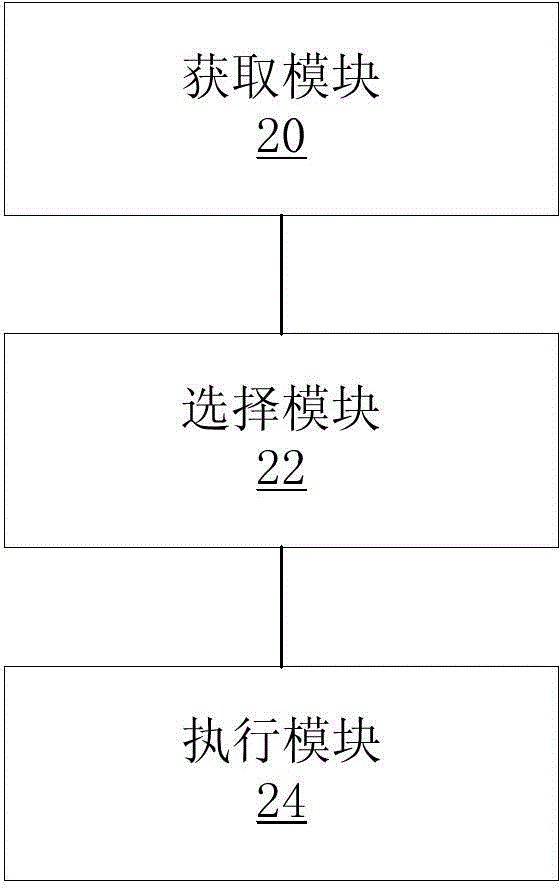
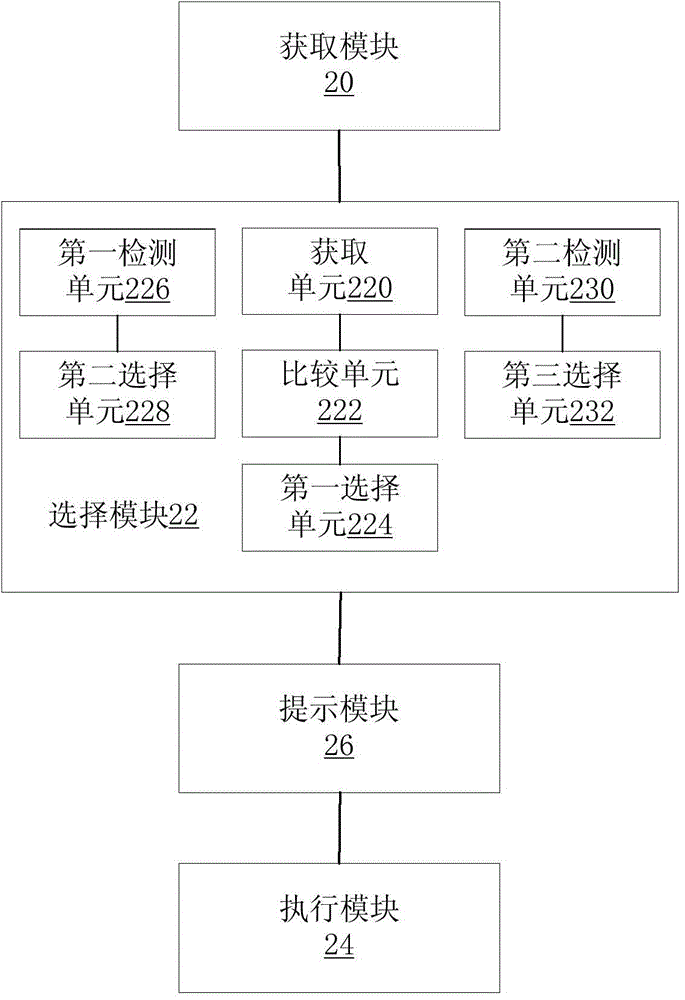
Image
Examples
Embodiment 1
[0056] In this embodiment, a scenario in which a user initiates a data service request is taken as an example for description.
[0057] Figure 5 It is a flow chart of a data service execution method according to preferred embodiment 1 of the present invention. Such as Figure 5 As shown, the method includes:
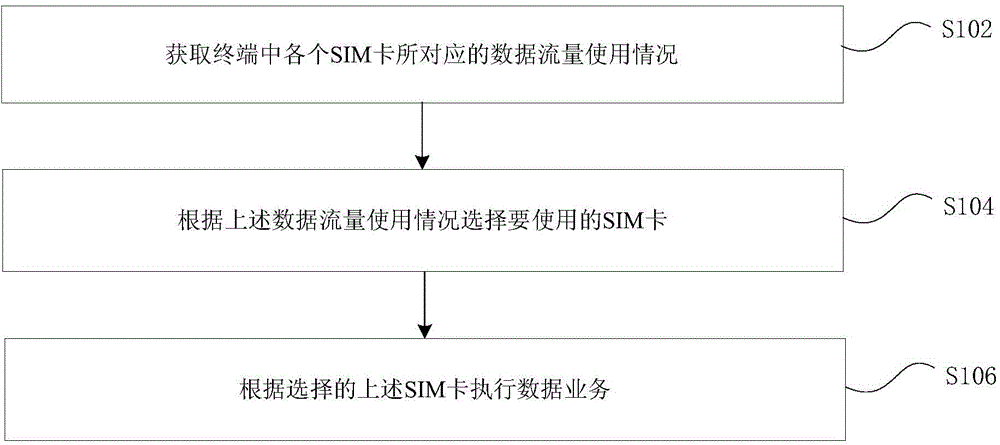
[0058] Step S502: the user uses the data service and initiates a data request.
[0059] Step S504: The data traffic management module 40 reads the cumulative used traffic of SIM1 and SIM2 from the mobile phone system, and calculates the remaining package traffic of the two cards, thereby obtaining the difference M of the actual remaining package traffic of the dual cards.
[0060] Step S506: Compare the difference M between the actual remaining package traffic of the dual card and the threshold value I of the remaining package traffic difference of the dual card set by the user. If M is greater than I, continue to use the SIM1 package traffic, and jump to S512 for ex...
Embodiment 2
[0066] In this embodiment, a scenario in which a user is using a data service is taken as an example for description.
[0067] Figure 6 It is a flowchart of a data service execution method according to the preferred embodiment 2 of the present invention. Such as Figure 6 As shown, the method includes:
[0068] Step S602: the user is using the data service.
[0069] Step S604: The data traffic control module regularly reads the data traffic S1 used by the SIM1 on that day from the mobile phone system.
[0070] Step S606: If S1 is less than the maximum SIM1 daily traffic HS1 preset by the user, continue to use the SIM1 package traffic, and jump to S616 for execution; otherwise, the SIM1 used traffic exceeds HS1, and execute S608.
[0071] Step S608: The data traffic control module reads the data traffic S2 used by the SIM2 on that day from the mobile phone system.
[0072] Step S610: If S2 is less than the maximum SIM2 daily traffic HS2 preset by the user, then go to S612...
Embodiment 3
[0079] In this embodiment, the user is using the data service as an example for description.
[0080] Figure 7 It is a flow chart of a data service execution method according to preferred embodiment 3 of the present invention. Such as Figure 7 As shown, the method includes:
[0081] Step 702: the user is using the data service.
[0082] Step S704: The data traffic control module regularly reads the accumulated data traffic S1 used by the SIM1 from the mobile phone system.
[0083] Step S706: If S1 is less than the data set of SIM1, then jump to S718 for execution; otherwise, S1 has exceeded the data set data.
[0084] Step 708: Judging whether the user has enabled the alarm function when the package data traffic is used up, if not enabled, then jump to S718 for execution; otherwise, if the alarm function is enabled, continue to perform subsequent rule judgment.
[0085] Step S710: The data flow control module regularly reads the accumulated used data flow S2 of the SIM2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com