Website bug online evaluation method and device
A website vulnerability and vulnerability online technology, applied in the Internet field, can solve the problems that cannot effectively play a preventive role, do not take into account the business impact of vulnerability website access traffic, website damage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The specific embodiments of the invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
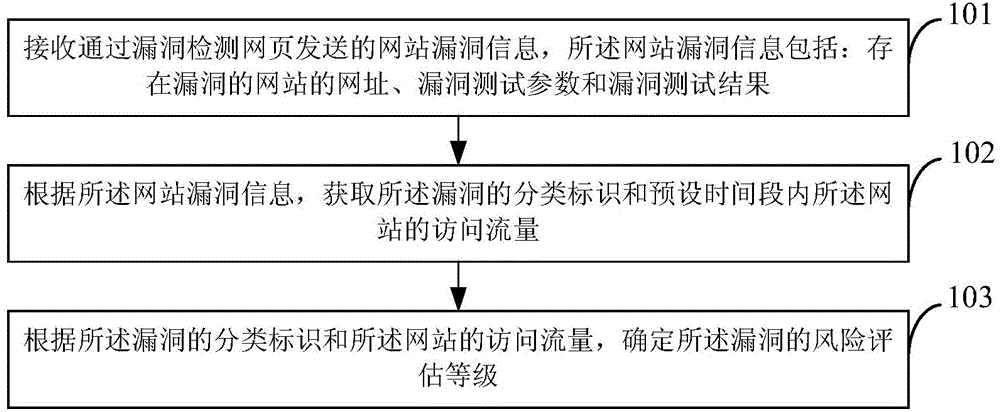
[0053] Figure 1A It shows a schematic flow chart of the website vulnerability online assessment method provided by an embodiment of the present invention, as shown in Figure 1A As shown, the website vulnerability online assessment method of this embodiment is as follows.
[0054] 101. Receive website vulnerability information sent through a vulnerability detection webpage, where the website vulnerability information includes: URLs of websites with vulnerabilities, vulnerability test parameters, and vulnerability test results.
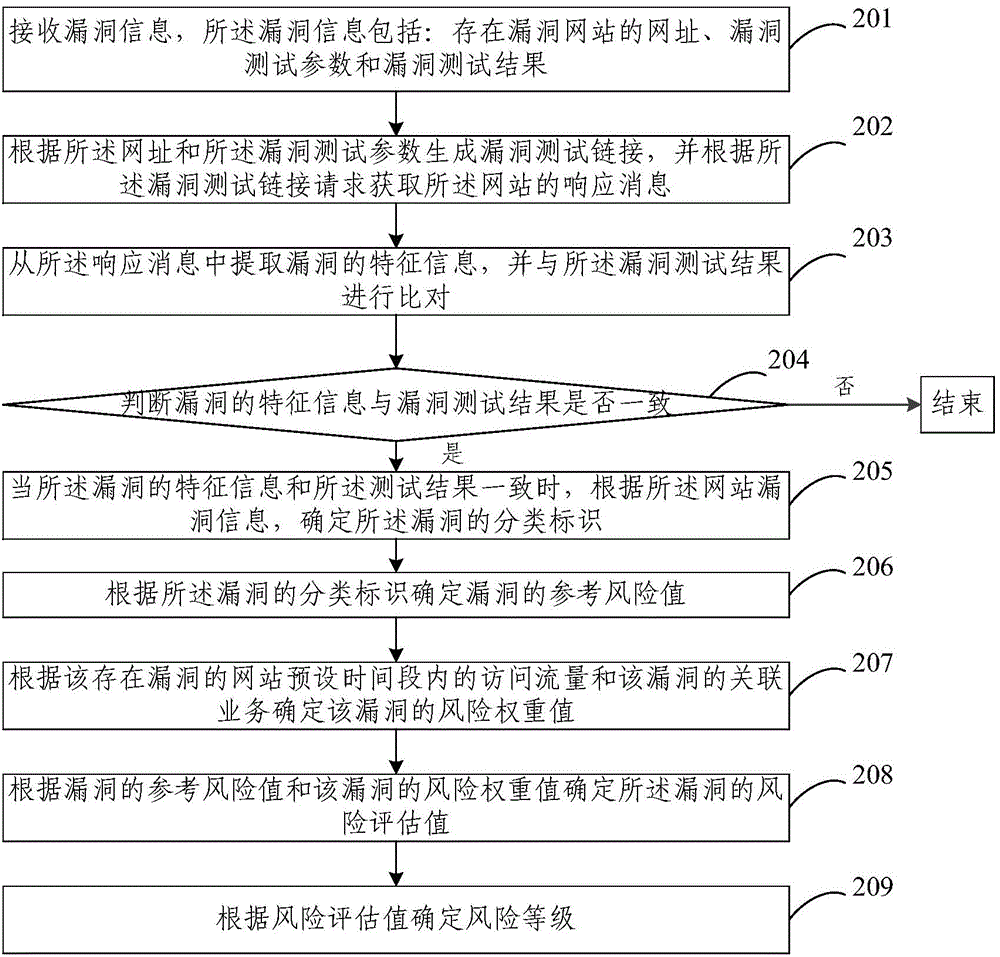
[0055] For example, the above website vulnerability information is the vulnerability information submitted by some professional users such as white ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com