Device and method for user identity authentication based on web browsing habits
A technology for user identity authentication and user identity recognition, which is applied in the field of information security to improve the detection rate and reduce the false alarm rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
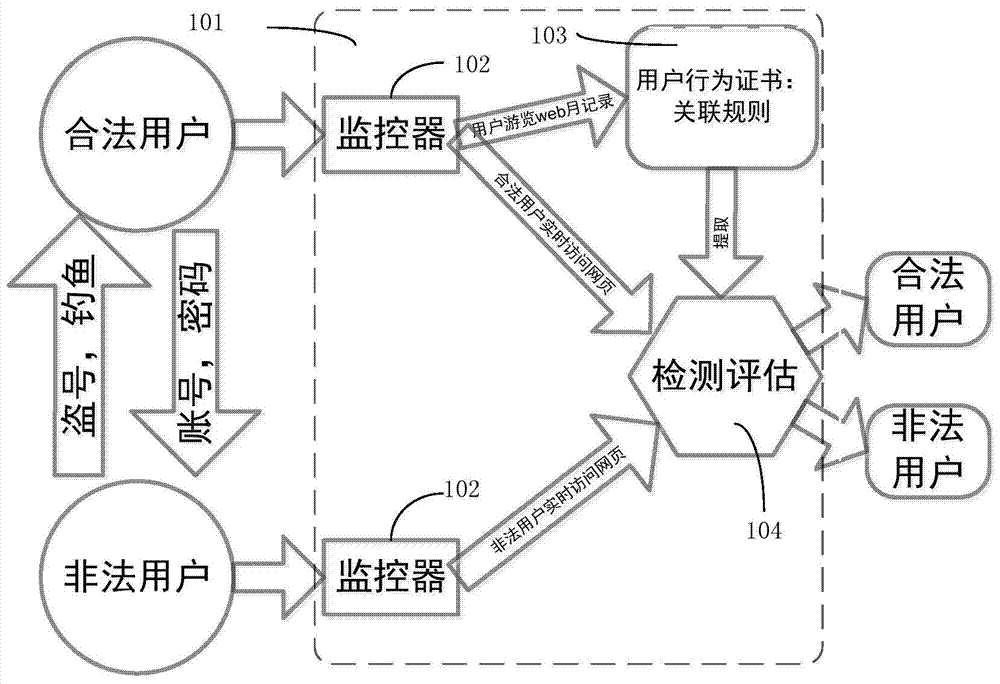
[0044] The monitor 102 of the user identity authentication device 101 based on WEB browsing habits of the present invention records the online behavior of legal users, and performs data mining on the WEB browsing records of the last month based on the sliding window principle to form a user behavior certificate based on association rules. When an illegal user logs in to a legitimate account, each webpage visited by the illegal user will be scored according to the user behavior certificate. If the score is lower than a certain threshold, we will consider the user's identity suspicious and warn for further identity verification. The whole scheme is divided into two parts: the first part is to form the user behavior certificate 103 based on the existing records, and the second part is to evaluate the user's real-time web browsing 104 based on the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com