Interception method and equipment for spam short messages of pseudo base station
A technology of spam text messages and pseudo base stations, which is applied in wireless communication, message/email/notification, electrical components, etc. It can solve the problem of not being able to intercept spam text messages, and achieve the effect of improving experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
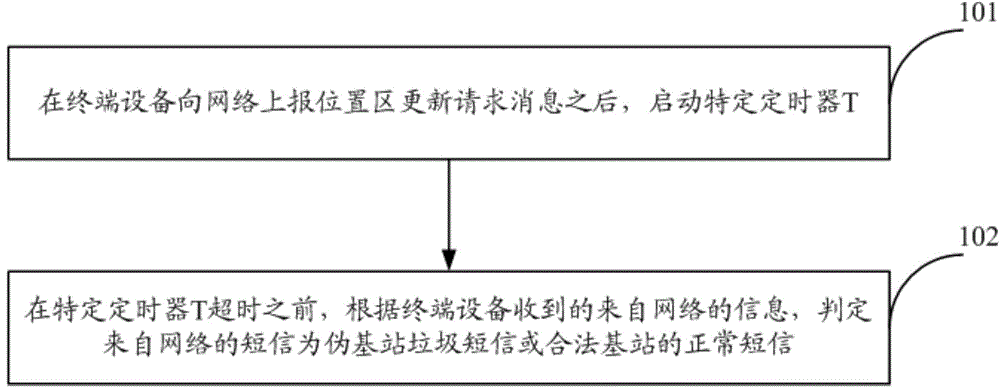
[0027] Aiming at the problems existing in the prior art, Embodiment 1 of the present invention provides a method for intercepting spam messages of pseudo base stations, by analyzing the working principle of spam messages issued by pseudo base stations, and intercepting spam messages of pseudo base stations in a targeted manner, thereby By intercepting spam messages sent by pseudo base stations, the user experience is improved. Among them, the working principle of the fake base station sending spam messages is: the fake base station obtains the frequency point information and system broadcast messages of the operator network, and then adjusts the frequency point information and system broadcast messages of the fake base station to the frequency point information of the operator network It is the same as the system broadcast message, so as to attract terminal equipment to connect to the pseudo base station, and induce the terminal equipment to initiate the location area update pr...
Embodiment 2
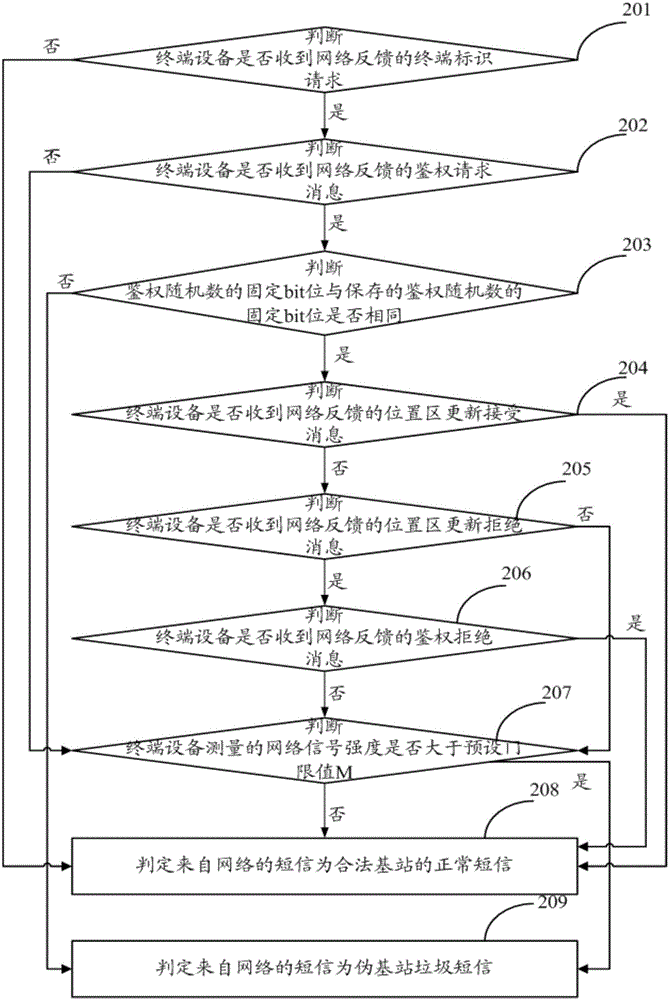
[0059] Based on the same inventive concept as in Embodiment 1, Embodiment 2 of the present invention provides a method for intercepting spam messages from fake base stations, by analyzing the working principle of sending spam messages from fake base stations, and intercepting spam messages from fake base stations in a targeted manner. In this way, the spam messages sent by the fake base station are intercepted, thereby improving user experience. Such as figure 2 As shown, the pseudo base station spam interception method comprises the following steps:
[0060] Step 201, judging whether the terminal device has received a terminal identification request fed back by the network; if yes, execute step 202; if not, execute step 208.
[0061] Step 202, judging whether the terminal device has received an authentication request message fed back by the network; if yes, execute step 203; if not, execute step 207.
[0062] Step 203, read the authentication random number from the authent...
Embodiment 3
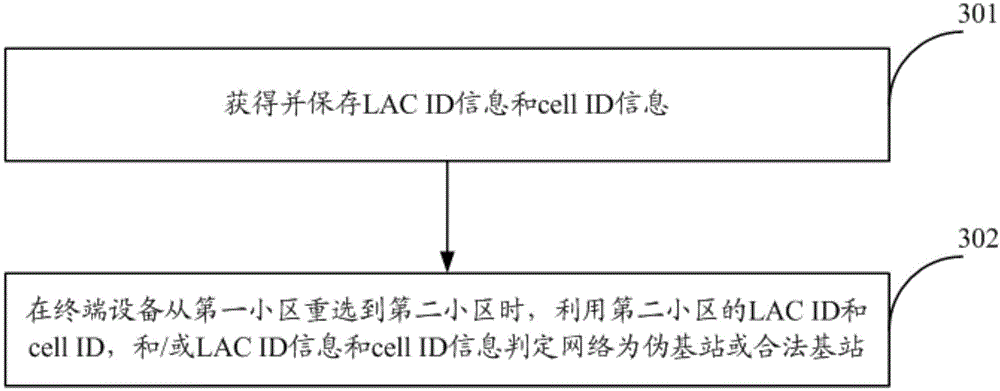
[0070] Based on the same inventive concept as in Embodiment 1, Embodiment 3 of the present invention provides a method for intercepting spam messages from fake base stations. By analyzing the working principle of sending spam messages from fake base stations, and intercepting spam messages from fake base stations in a targeted manner, In this way, the spam messages sent by the fake base station are intercepted, thereby improving user experience. Such as image 3 As shown, the pseudo base station spam interception method comprises the following steps:
[0071] Step 301, obtaining and storing LAC ID information and cell ID information.
[0072] Step 302, when the terminal device reselects from the first cell to the second cell, use the LAC ID and cell ID of the second cell, and / or the LAC ID and cell ID information to determine whether the network is a fake base station or a legitimate base station. When it is determined that the network is a pseudo base station, the terminal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com