Method for detecting anomaly of Modbus TCP (transmission control protocol) communication on basis of SVM (support vector machine)
An anomaly detection and communication technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as unidentifiable attack behaviors and Modbus communication anomalies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
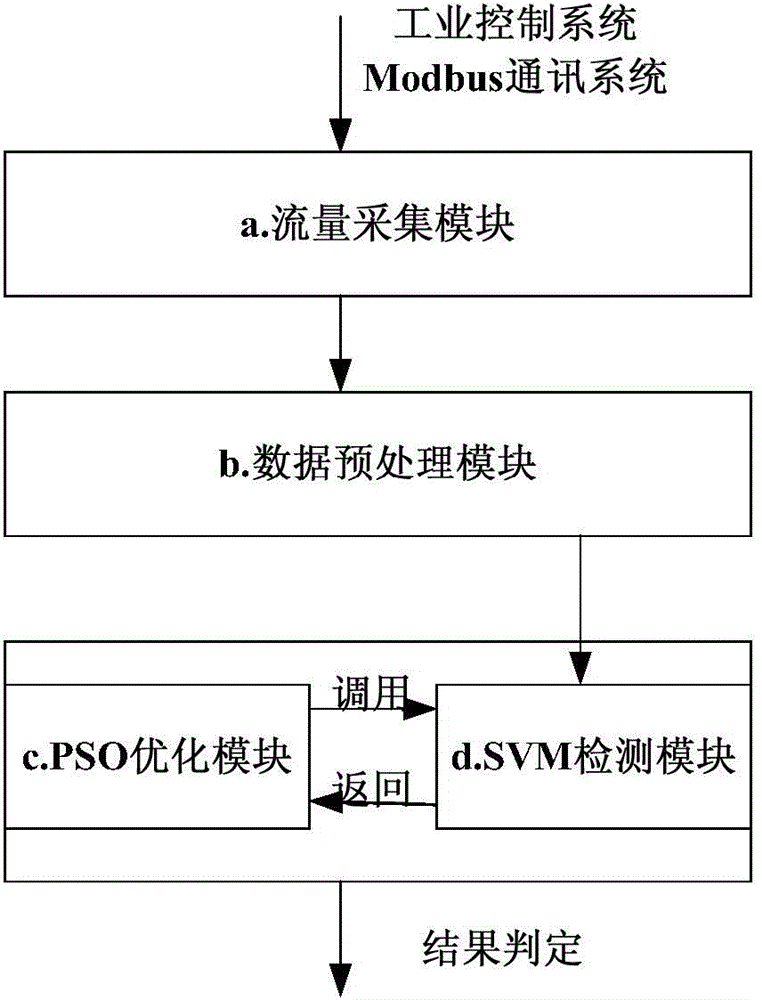
[0058] Such as figure 2 As shown, the abnormal detection method of SVM-based Modbus TCP communication includes:
[0059] a. Traffic collection part
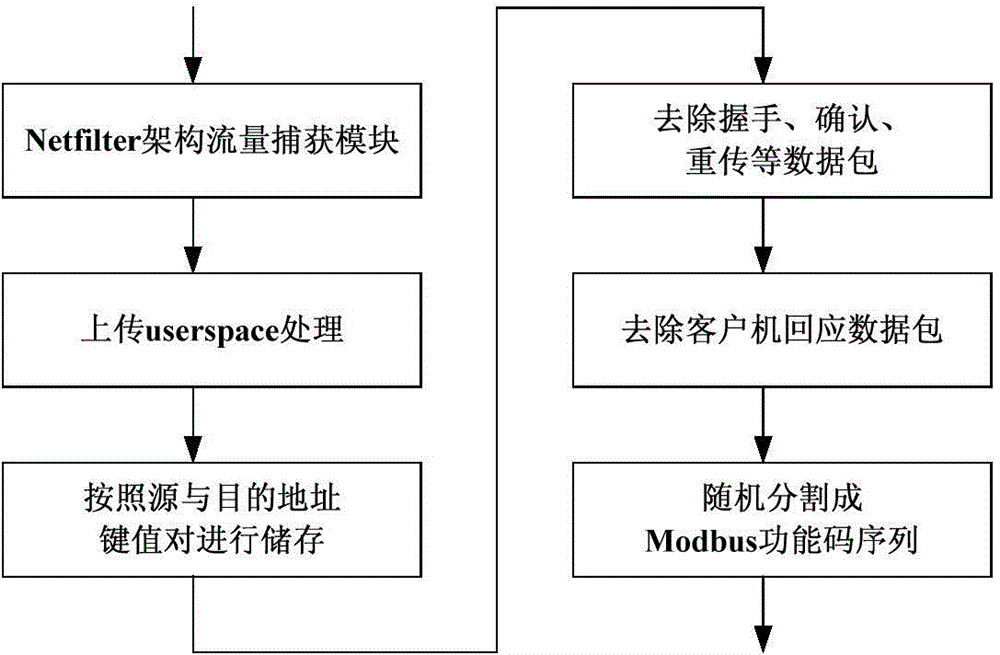
[0060] 1 Use the Netfilter mechanism of the Linux kernel to write a traffic capture module to capture the ModbusTCP communication traffic in the industrial control system, and classify and store it according to the key-value pairs of the source address and the destination address. On this basis, due to the focus on the security of the application layer protocol, it is necessary to eliminate data packets that do not contain Modbus function codes such as handshake, confirmation, and retransmission at the socket level, and further eliminate the Modbus server to the client. The data packet that the machine responds to.
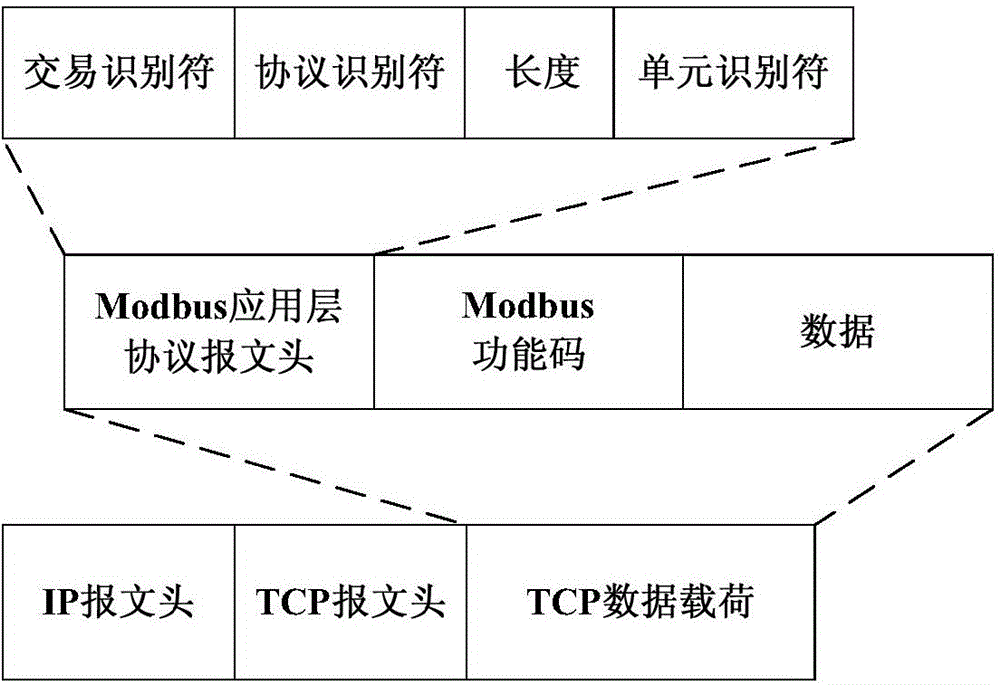
[0061] 2 In view of the fact that the Modbus function code can best reflect ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com