PSO-OCSVM based industrial control system communication behavior anomaly detection method
A technology of PSO-OCSVM and industrial control system, applied in the direction of transmission system, digital transmission system, electrical components, etc., can solve the problem of inability to detect abnormal behavior of multiple data packet communication, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
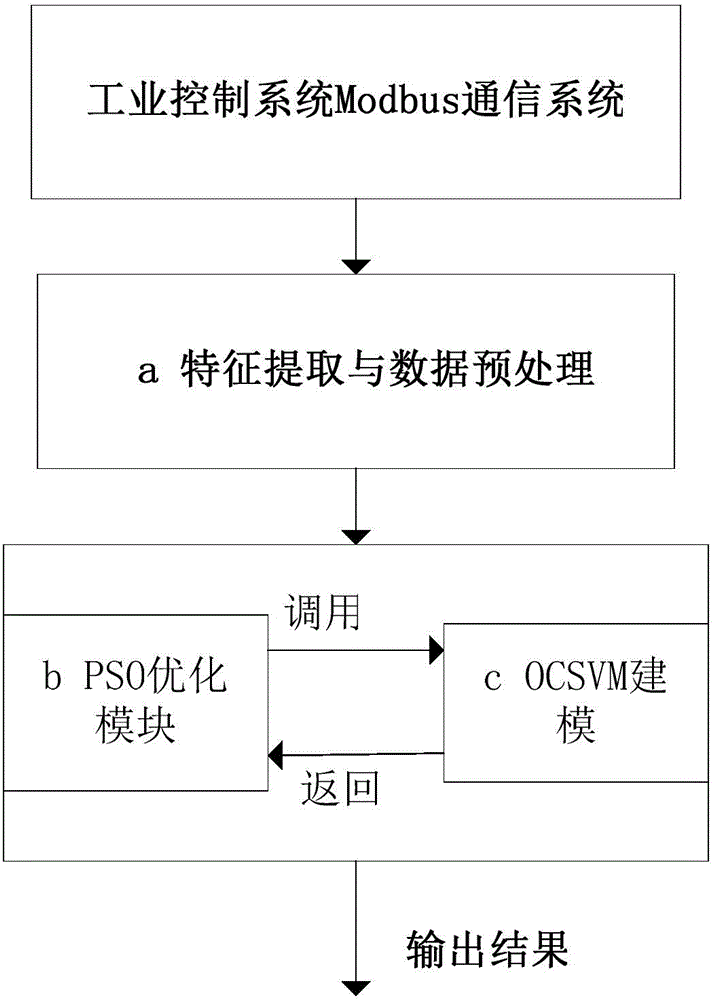
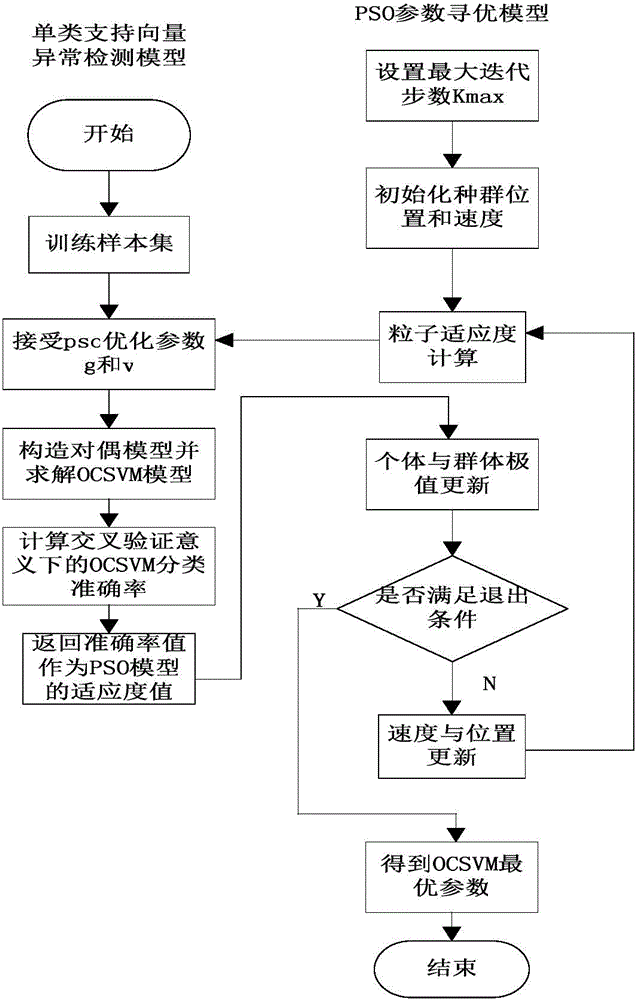
[0051] Such as figure 2 , 3 As shown, the communication behavior anomaly detection method based on OCSVM includes:
[0052] a. Feature extraction and preprocessing part
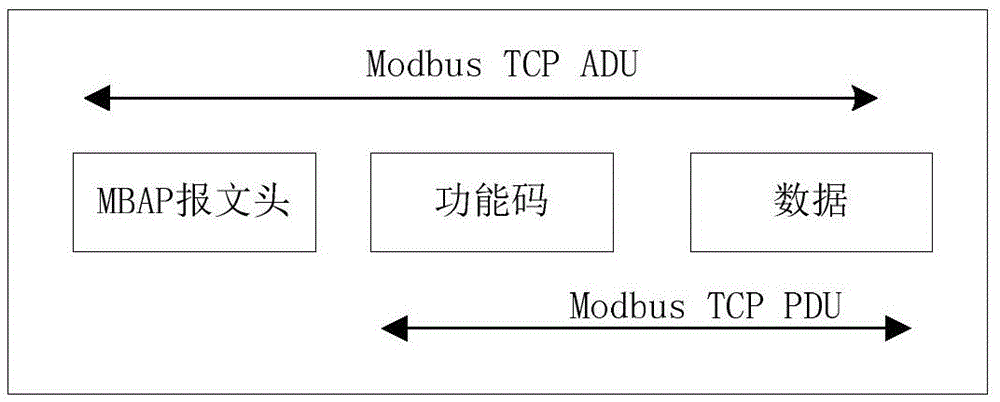
[0053] 1ModbusTCP message format has expanded some data structures on the basis of retaining all the functions of Modbus. The message format of ModbusTCP mainly includes three parts: MBAP message header, Modbus function code and data. When the client computer sends a message to the server device, the function code field is the only basis for the server to distinguish between read operations, write operations, data types, and data types, so the Modbus function code is used as a feature vector, such as figure 1 shown.
[0054] 2 The ModbusTCP traffic captured by wireshark contains redundant and unimportant features, remove redundant or unimportant features, and only retai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com