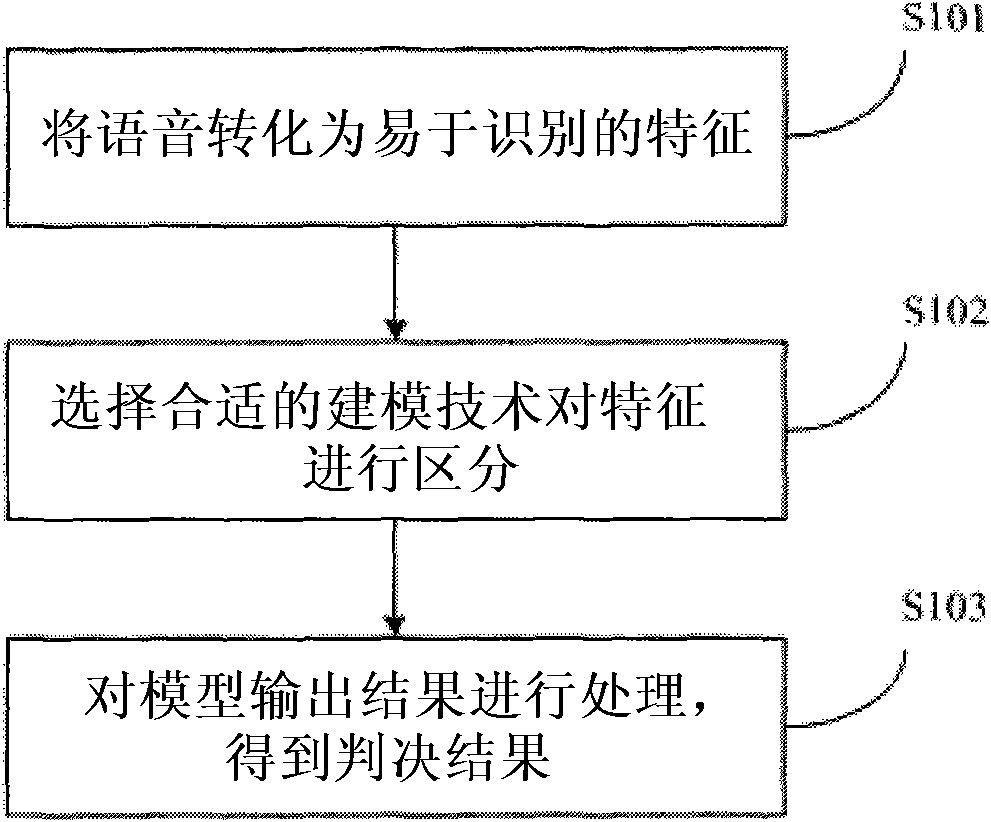
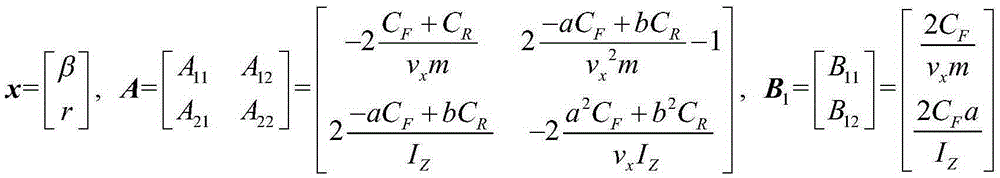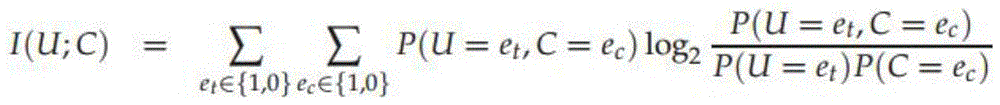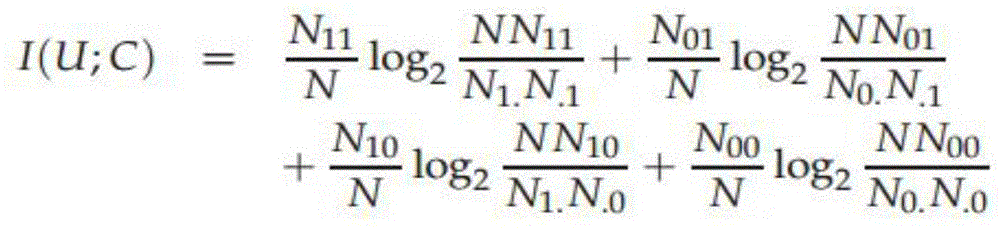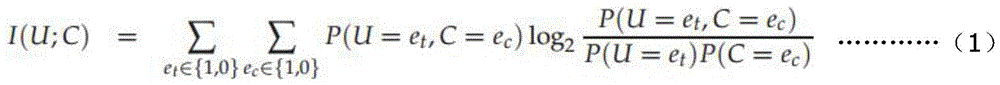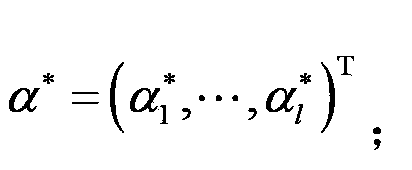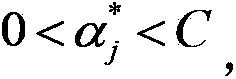Patents
Literature
510 results about "Support vector machine algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The support vector machine is an algorithm that is primarily focused on detecting and analyzing relationships. This machine learning algorithm works by analyzing data sets through a series of variables. The way that the data respond to the variables can be mapped out.
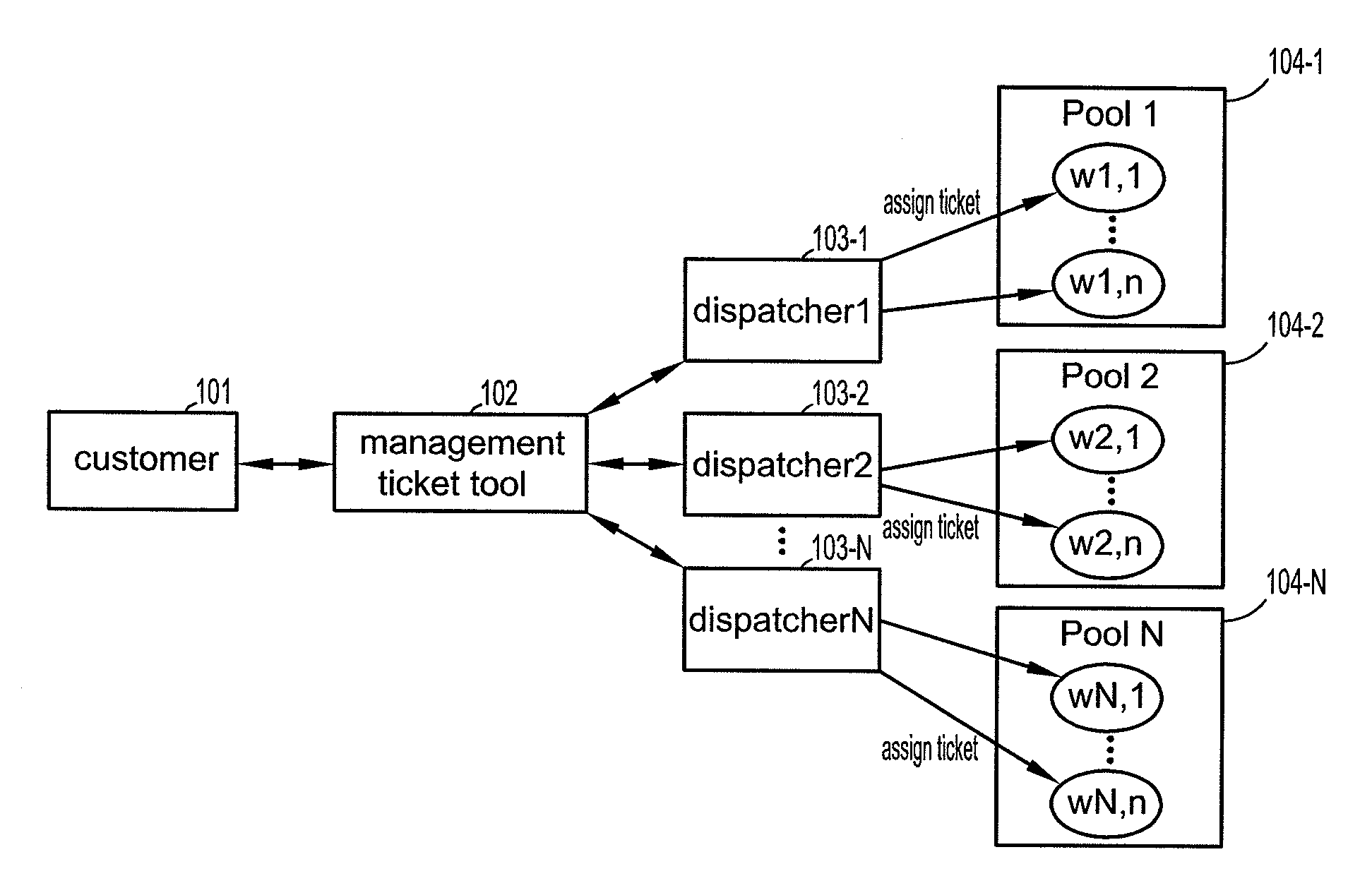
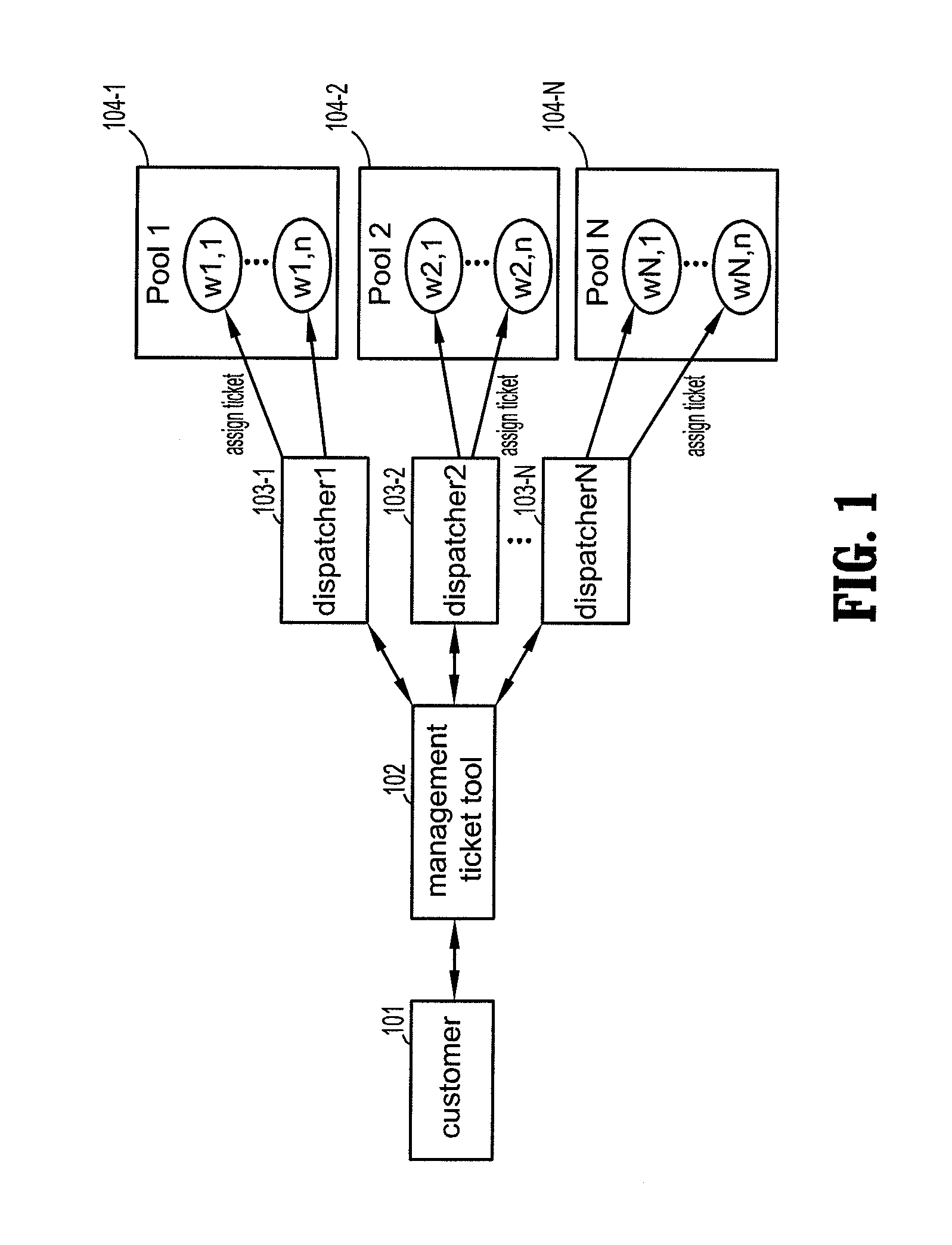
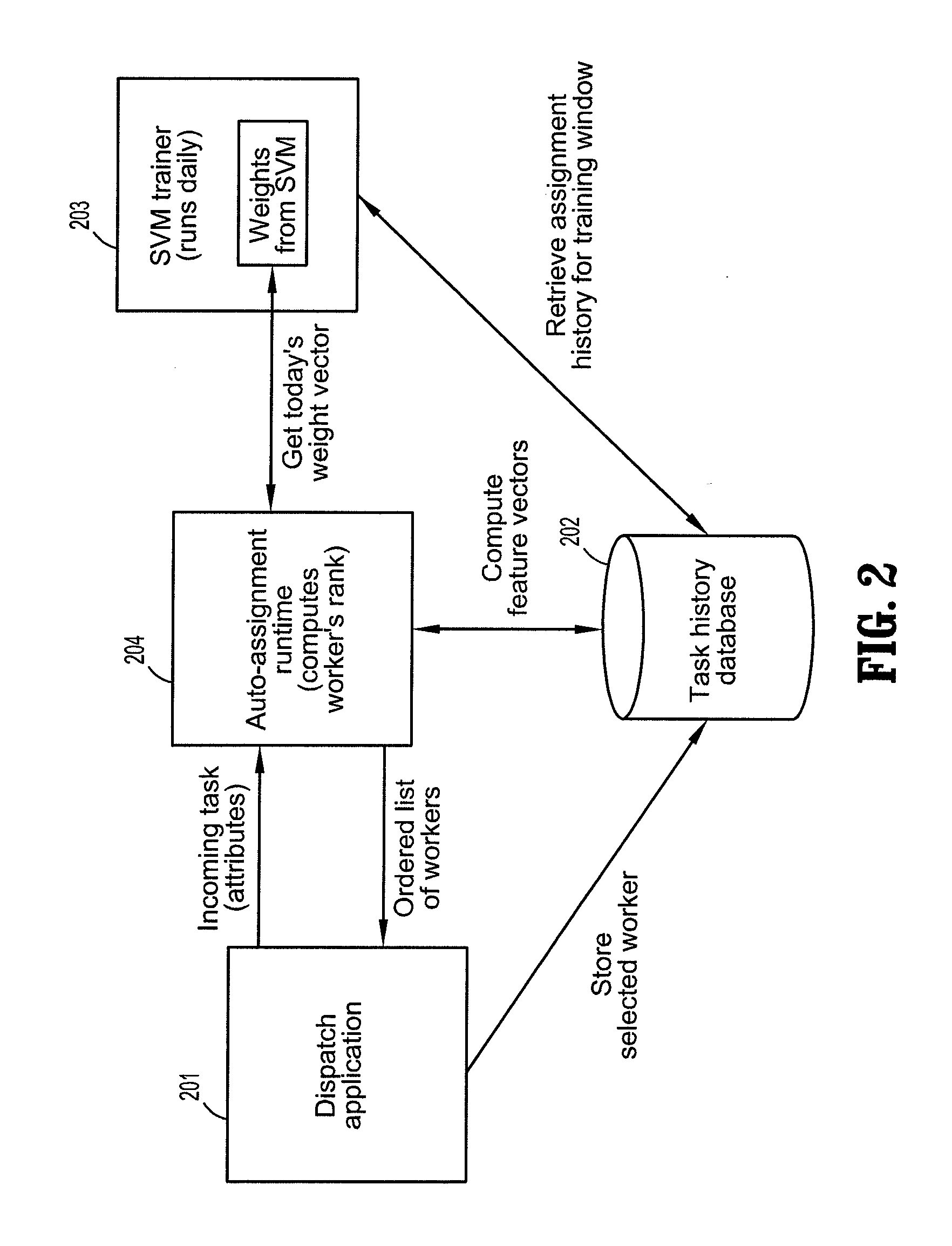
Task assignment using ranking support vector machines
ActiveUS20130111488A1Kernel methodsMultiprogramming arrangementsFeature vectorSupport vector regression machine
A method of ranking workers for an incoming task includes recording a list of completed tasks in a computer data structure, extracting first attributes from the list for the tasks that were completed during a pre-determined period, generating a first feature vector for each task and worker from the first extracted attributes, training a Support Vector Machine (SVM) based on the feature vector to output a weight vector, extracting second attributes from an incoming task, generating a second feature vector for each worker based on the second extracted attributes, and ranking the workers using the second feature vectors and the weight vector. The first attributes may be updated during a subsequent period to re-train the SVM on updated first feature vectors to generate an updated weight vector. The workers may be re-ranked based on the second feature vectors and the updated weight vector. Accordingly, the feature vectors are dynamic.
Owner:KYNDRYL INC
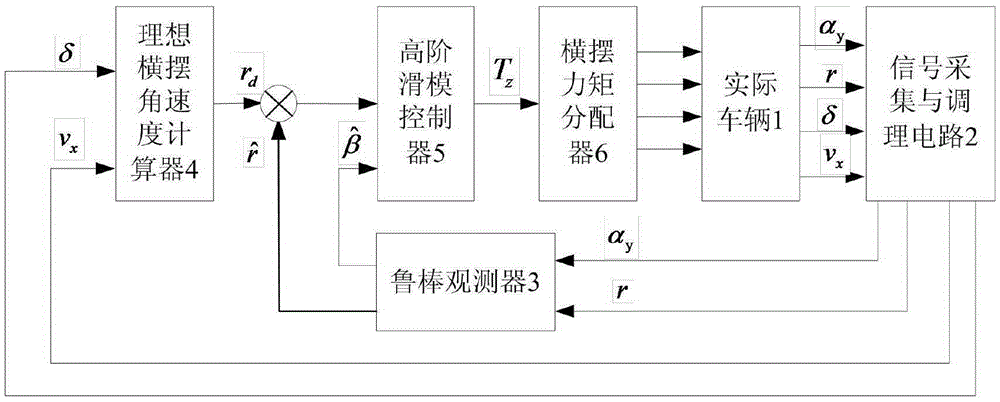
Method for controlling electric automobile stability direct yawing moment based on high-order slip mold
ActiveCN105416276AImprove robustnessImprove reliabilityDriver input parametersEngineeringBrake force
The invention provides a method for controlling the electric automobile stability direct yawing moment based on a high-order slip mold and relates to the field of control over electric automobile stability. The method includes the steps that the rotation angle of a steering wheel and the longitudinal automobile speed are detected through a signal acquisition and conditioning circuit, so that the ideal yawing angular speed value is obtained; according to the detected yawing accelerated speed at the current moment of an automobile and the actual yawing angular speed, the side slip angle estimated value is obtained through a robust slip mold observer based on active control and self-adaptive estimation; two parameters of the difference of the yawing angular speed and the ideal yawing angular speed and the actual slide slip angle of the automobile serve as input variables, a high-order slip mold control strategy is adopted, and the direct yawing moment meeting the requirement for automobile stability is obtained; and finally, the automobile stability margin serves as an objective function and a constraint condition, and a support vector machine algorithm is used for distributing drive force or brake force. By the adoption of the method, the finite time constriction of an automobile stability direct yawing moment control system is achieved, and the travel stability of the automobile under the limit conditions of the high speed, the severe road and the like is improved.
Owner:BAISHAN POWER SUPPLY COMPANY OF STATE GRID JILIN ELECTRONICS POWER COMPANY
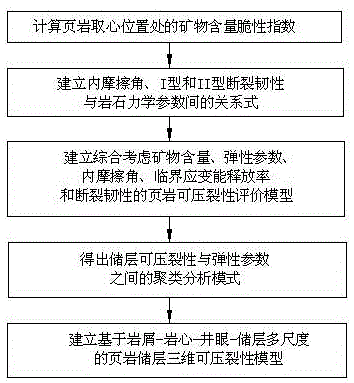
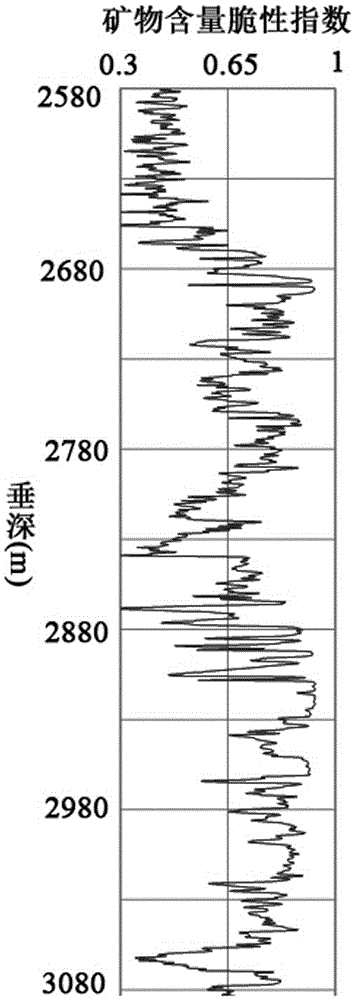
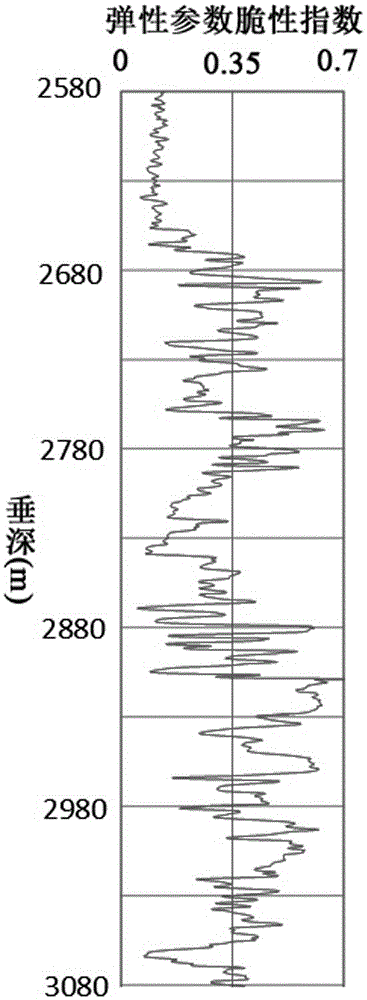
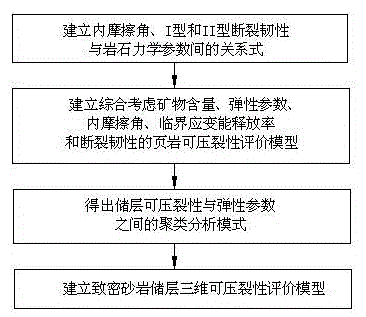
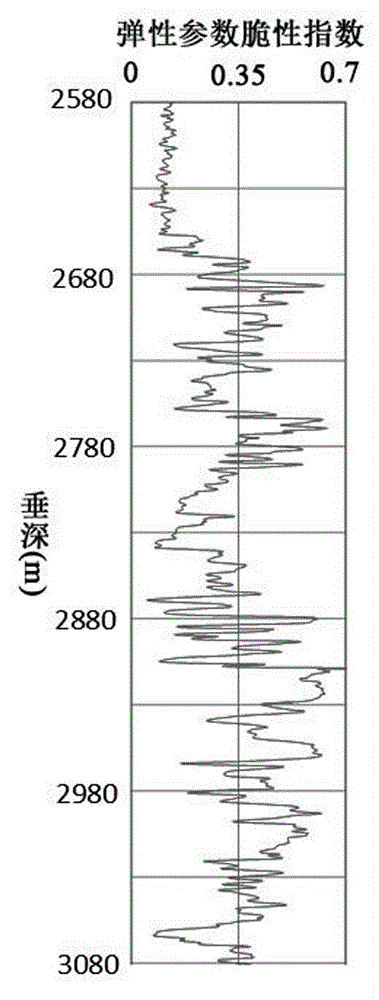
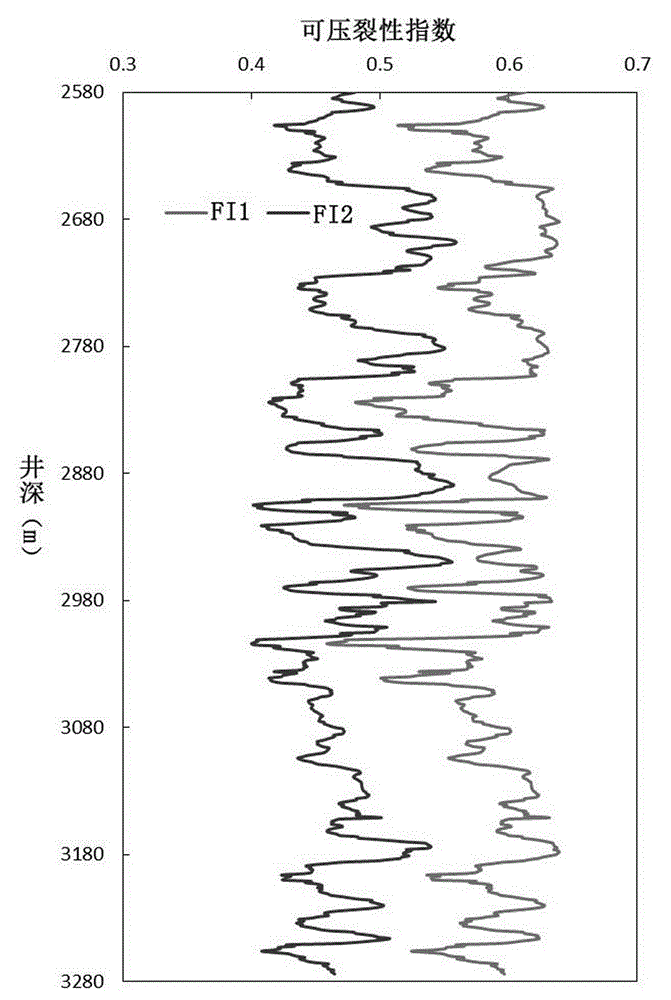
Debris-core-borehole-reservoir multiscale shale reservoir three-dimensional fracturing evaluation method
ActiveCN105156103ALarge capacityQuantification of fracabilityBorehole/well accessoriesType fractureWell placement
The invention relates to a debris-core-borehole-reservoir multiscale shale reservoir three-dimensional fracturing evaluation method. The method comprises the steps of: (S1) calculating mineral content brittleness indexes in a shale coring position; (S2) building relations among an internal friction angle, I type and II type fracture toughness and rock mechanical parameters; (S3) building shale fracturing evaluation models comprehensively considering a mineral content, elastic parameters, the internal friction angle, a critical strain energy release rate and the rapture toughness; (S4) applying a support vector machine algorithm to obtain a cluster analysis mode between a reservoir fracturing performance and the elastic parameters; and (S5) applying the cluster analysis mode and a reservoir three-dimensional elastic parameter data body to obtain a debris-core-borehole-reservoir multiscale shale reservoir three-dimensional fracturing model. The method can be applied to obtain the fracturing performance of any space position in a shale reservoir, so that the well position selection blindness is prevented, and the fracturing modification effect and the after-pressing yield are improved.
Owner:SOUTHWEST PETROLEUM UNIV +1
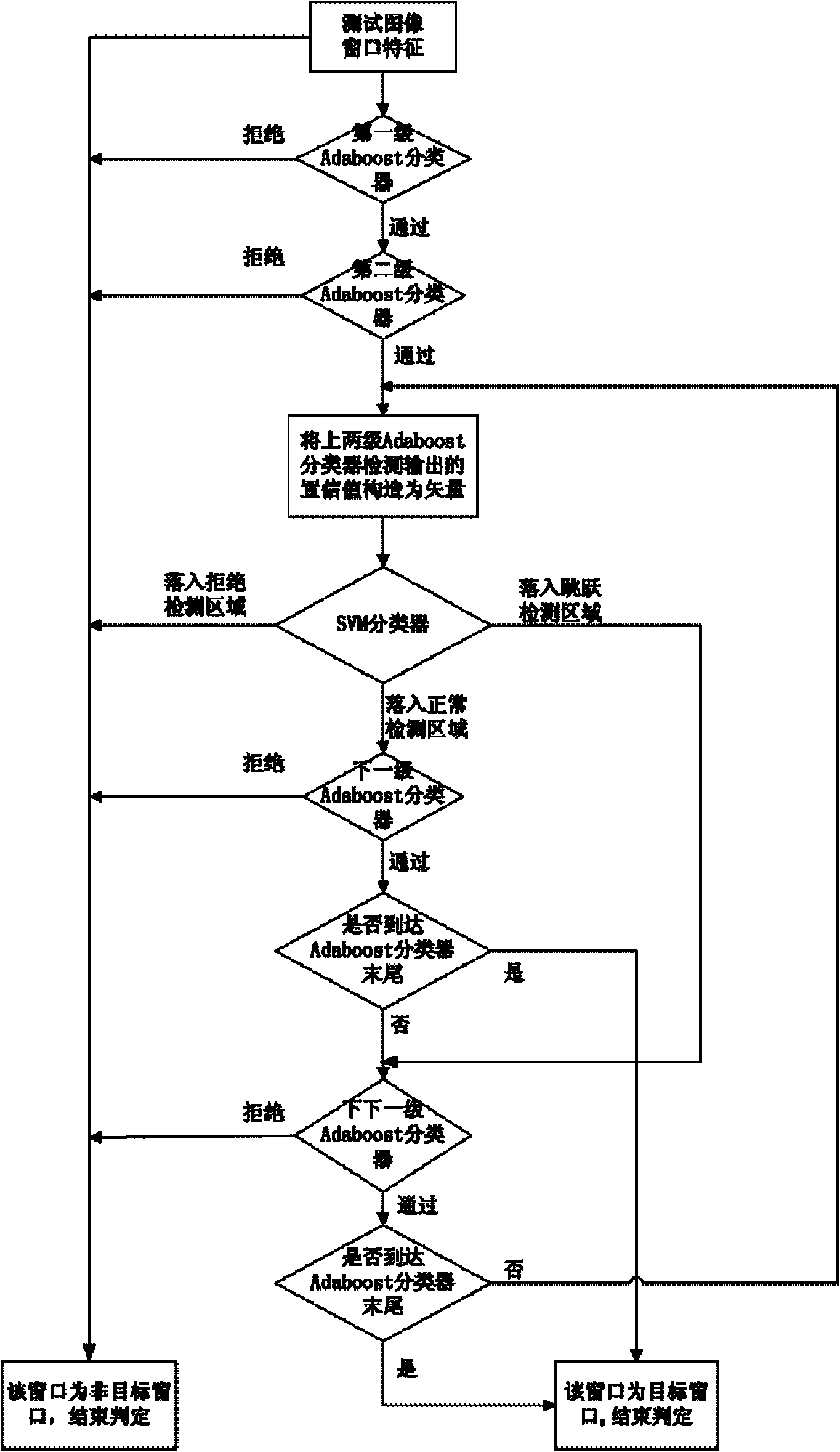
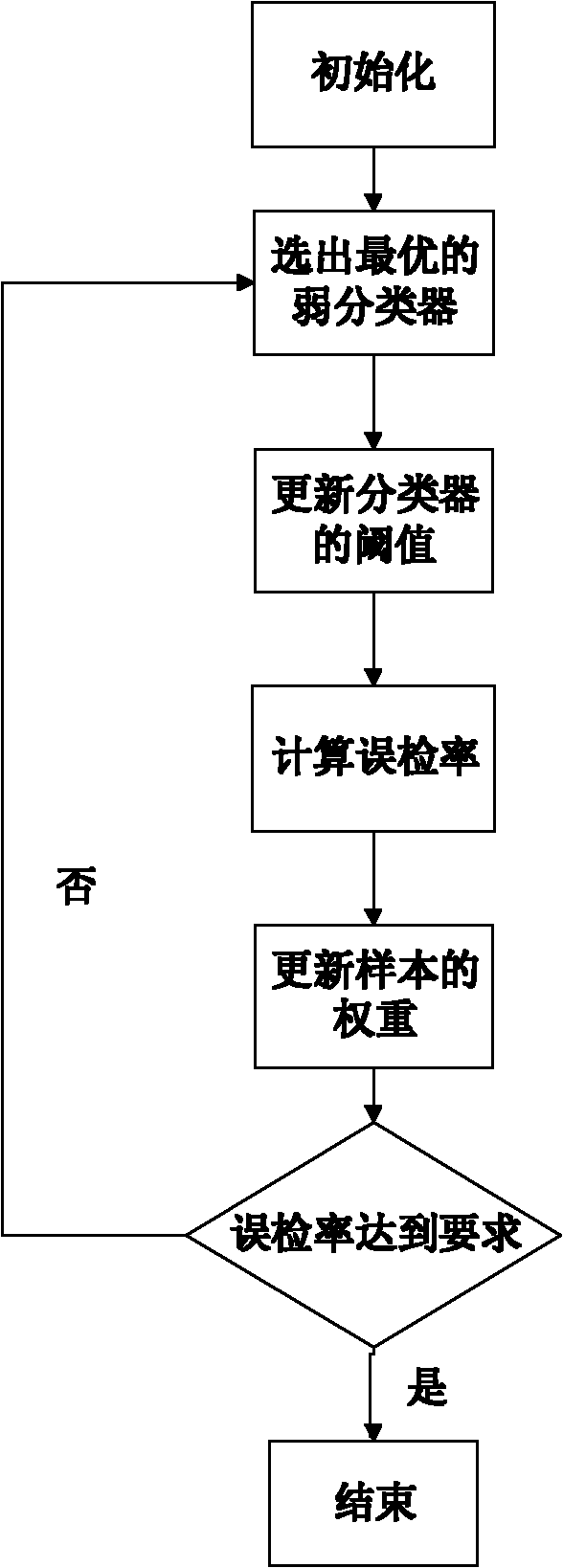
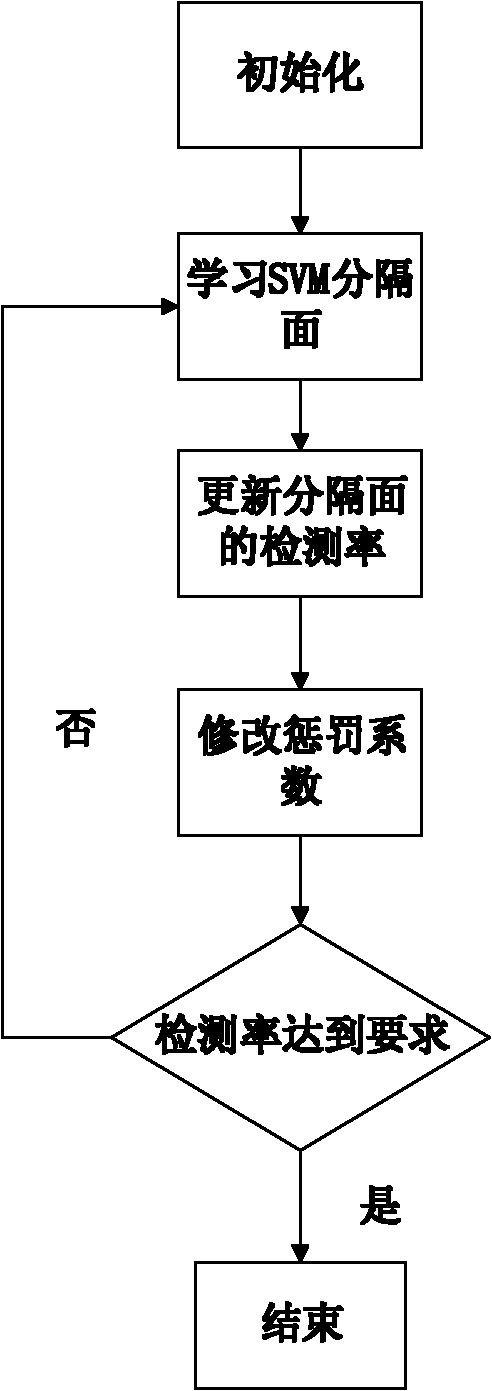
Target identification method based on training Adaboost and support vector machine
InactiveCN102147866AImprove efficiencyHigh precisionCharacter and pattern recognitionImaging processingAdaBoost
The invention relates to a target identification method based on training Adaboost and a support vector machine, relating to the technical field of image processing. The target identification method comprises the following steps: extracting haar characteristics of an original sample and using the haar characteristics for training to obtain a cascading classifier based on the Adaboost and the SVM (support vector machine) and then carrying out target identification on an image to be identified by using the cascading classifier to obtain a final identification result. The target identification method can accurately and rapidly identify targets such as people, vehicles and the like.
Owner:SHANGHAI JIAO TONG UNIV
Modeling method for compact sandstone reservoir three-dimensional fracability model
ActiveCN105134156AImproving the effectiveness of volumetric fracturingShorter payback timeFluid removalSpecial data processing applicationsModel methodWell placement
The invention relates to a modeling method for a compact sandstone reservoir three-dimensional fracability model. The method comprises the following steps: S1, establishing a relation formula among an internal friction angle, I type and II type crack fracture toughness and the parameter of sandstone mechanical characteristics; S2, establishing a shale fracability evaluation model which comprehensively considers an elastic parameter, the internal friction angle, the critical strain energy release rate and fracture toughness; S3, adopting a support vector machine algorithm to obtain a cluster analysis mode between the reservoir fracability and the elastic parameter; S4, adopting the cluster analysis mode to obtain a reservoir three-dimensional elastic parameter data body, and establishing the multi-scale compact sandstone reservoir three-dimensional fracability evaluation model based on the core, the borehole and the reservoir of multiple scales. According to the method, the fracability of an arbitrary space position in the compact sandstone reservoir can be obtained, a sweet spot with high fracability can always be drilled when drilling a compact sandstone gas well, blindness of well location selection is avoided, and the fracture modification effect and the yield after fracture are improved.
Owner:SOUTHWEST PETROLEUM UNIV
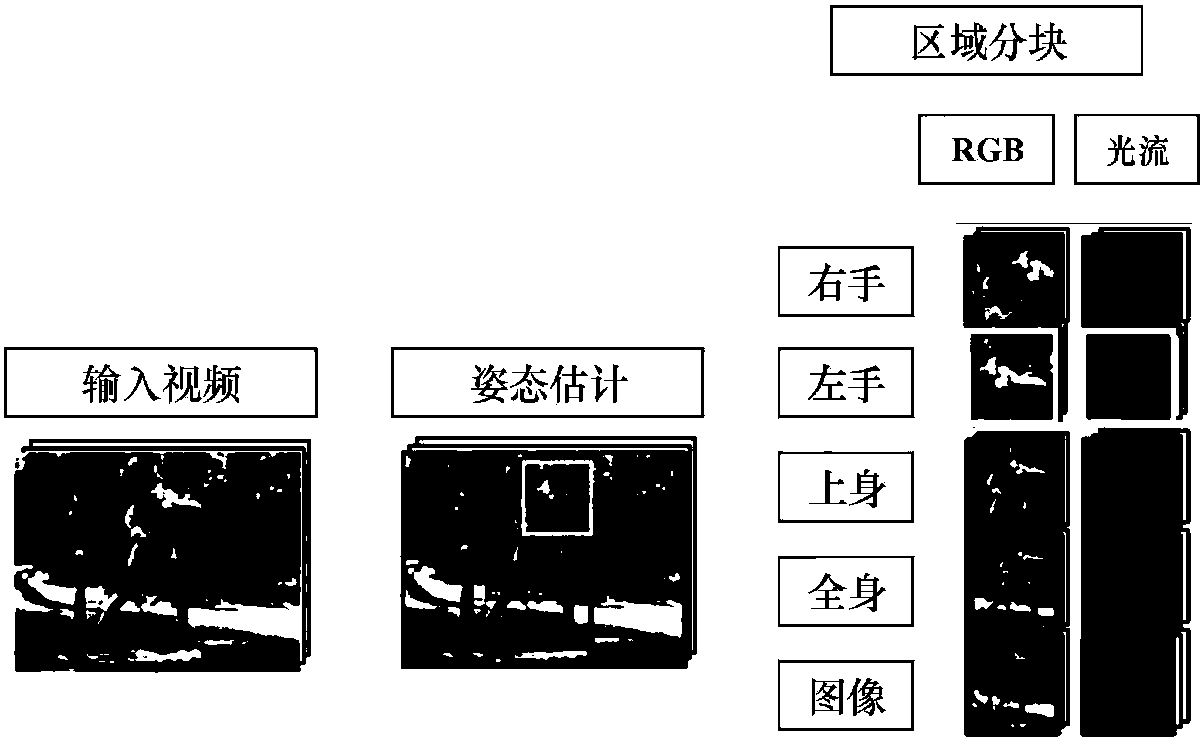
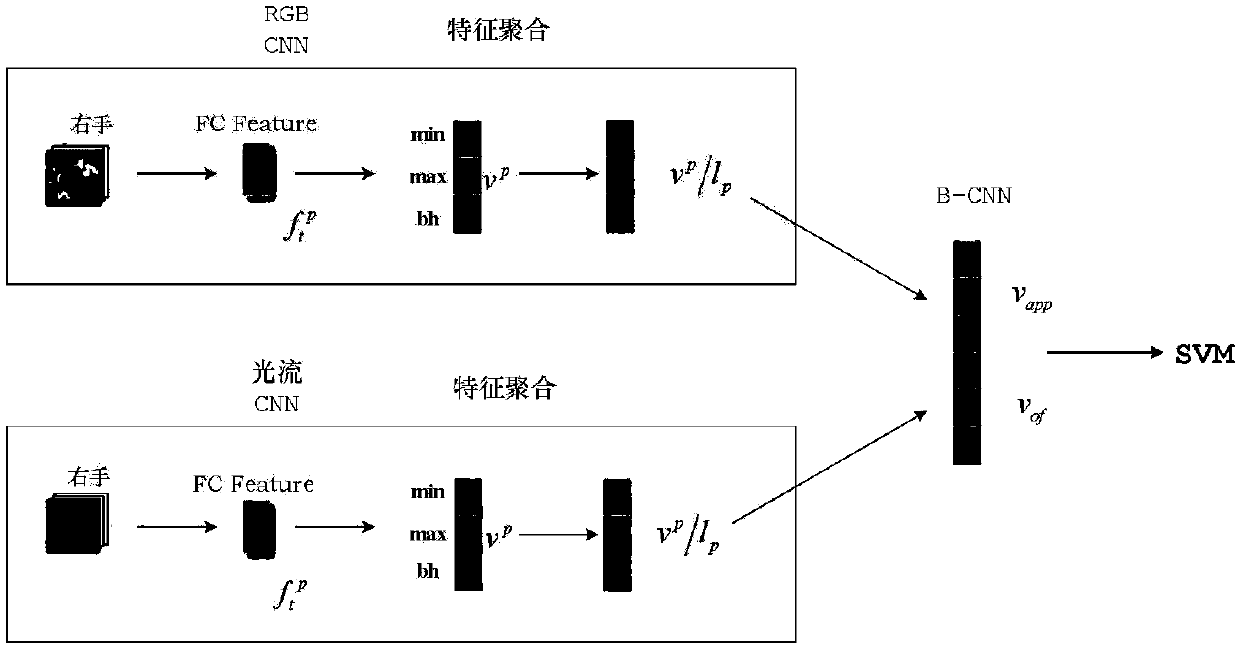
Human movement identification method through fusion of deep neural network model and binary system Hash
InactiveCN108108699AEasy to identifyCharacter and pattern recognitionPattern recognitionSupport vector machine algorithm
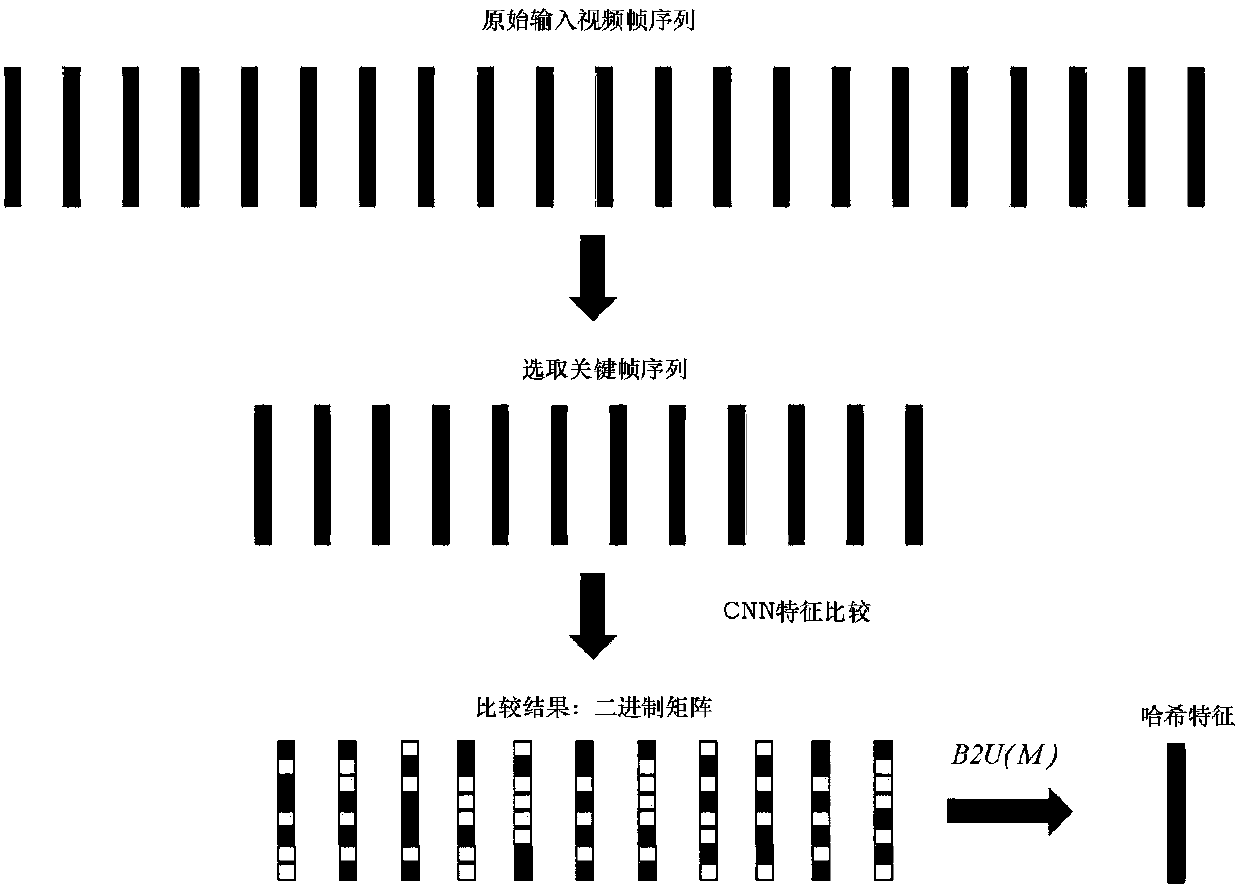
The present invention provides a human movement identification method through fusion of a deep neural network model and binary system Hash, belonging to the technical field of mode identification. Themethod comprises the steps of: performing preprocessing of a movement identification database, dividing the movement identification database into frame sequences, calculating an optical flow graph, employing an attitude estimation algorithm to calculate coordinates of human joint points, and employing result coordinates to extract video area frames; employing a pre-training VGC-16 network model to extract FC (Full-Convolutional) features of RGB flows and optical flows of the videos, selecting key frames from the video frame sequences, and obtaining a difference of the FC features corresponding to the key frames; performing binary processing of the difference; employing a binary-hashing method to obtain uniform feature expression of each video; employing a plurality of normalization methods such as L1 and L2 to obtain feature expressions of the videos after the fusion of the uniform feature expressions and the PCNN features; and finally, employing a support vector machine algorithm totrain a classifiers to identify the human movement videos. The human movement identification method through fusion of the deep neural network model and the binary system Hash has a high movement identification correct rate.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Incremental learning-fused support vector machine multi-class classification method
InactiveCN101944122AAvoid problems caused by outliersShorten test timeSpecial data processing applicationsOne-class classificationClassification methods
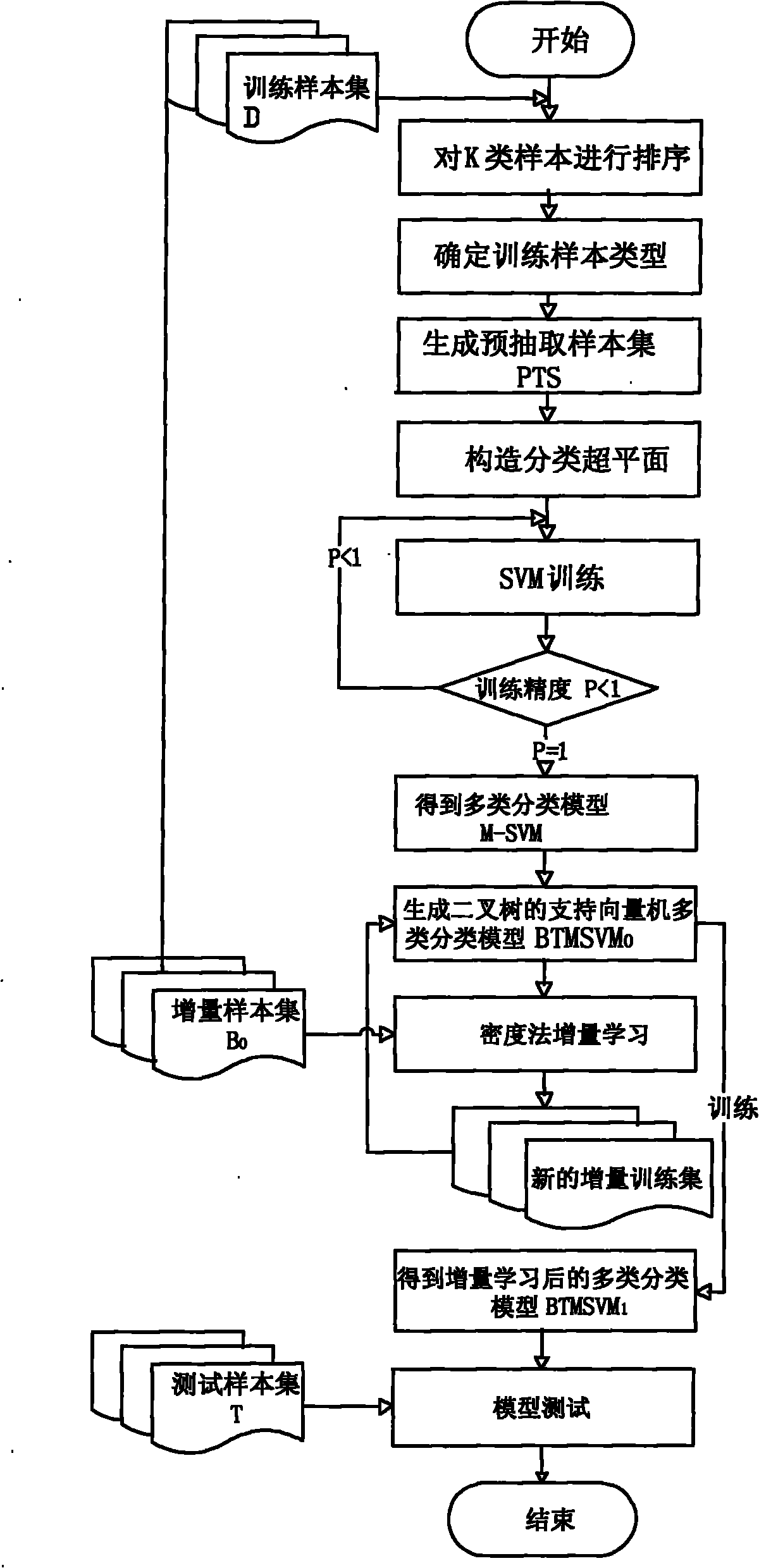
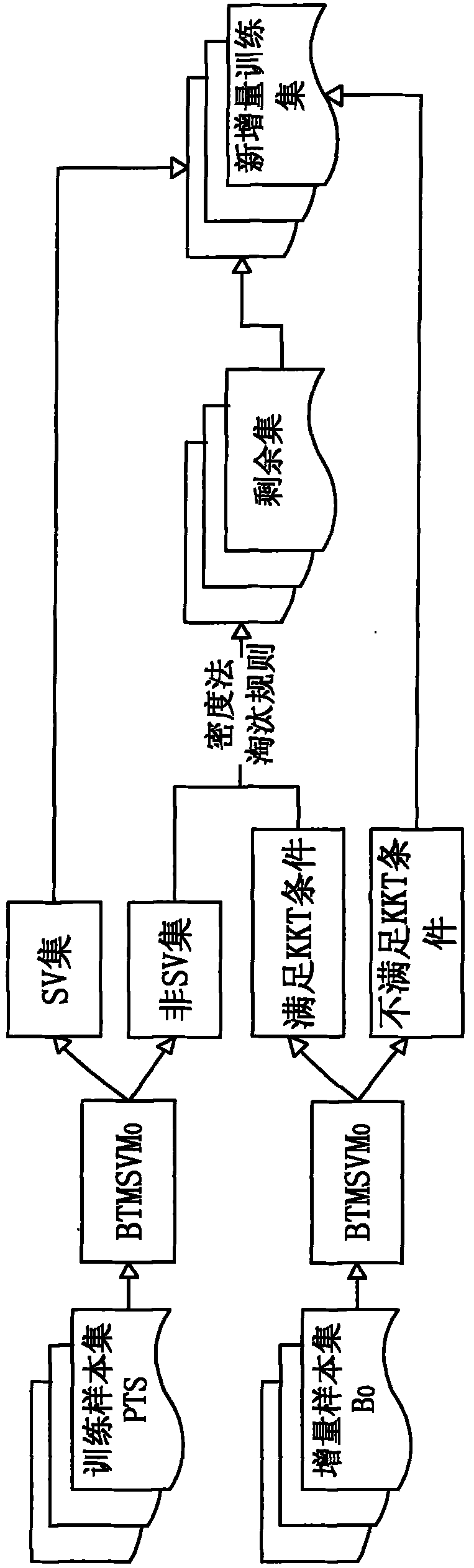
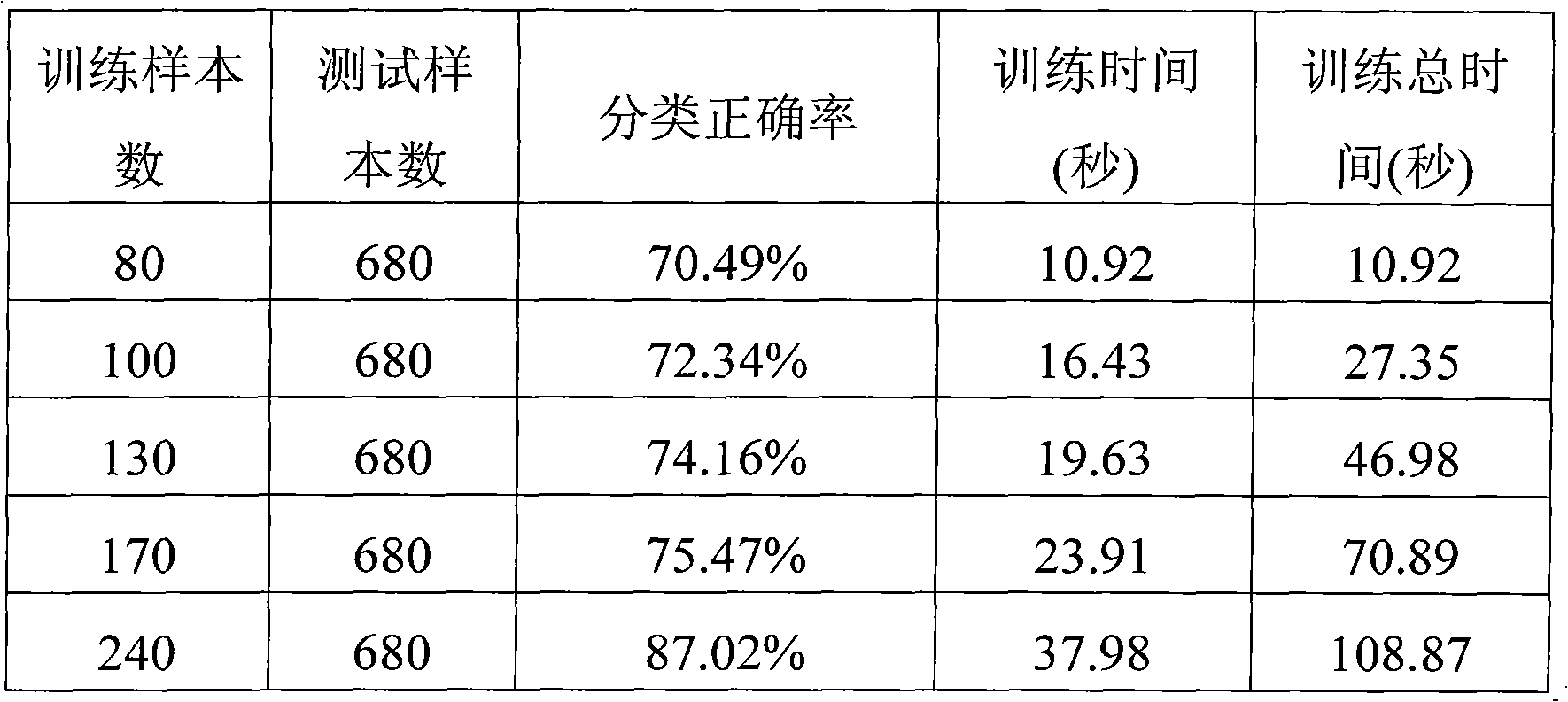
The invention relates to an incremental learning-fused support vector machine multi-class classification method, and aims to reduce sample training time and improve classification precision and anti-interference performance of a classifier. The technical scheme comprises the following steps of: 1, extracting partial samples from total samples at random to serve as a training sample set D, and using the other part of samples as a testing sample set T; 2, pre-extracting support vectors from the training sample set D; 3, performing support vector machine training on a pre-extracted training sample set PTS by using a cyclic iterative method so as to obtain a multi-class classification model M-SVM; 4, performing binary tree processing on the multi-class classification model M-SVM to obtain a support vector machine multi-class classification model BTMSVM0; 5, performing incremental learning training on the multi-class classification model BTMSVM0 to obtain a model BTMSVM1; and 6, inputting the testing sample set T in the step 1 into the multi-class classification model BTMSVM1 for classification. The incremental learning-fused support vector machine multi-class classification method is used for performing high-efficiency multi-class classification on massive information through incremental learning.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Characteristic extraction method of text classification on the basis of mutual information
InactiveCN105701084ACharacter and pattern recognitionNatural language data processingPart of speechFeature extraction
The invention discloses a characteristic extraction method of text classification on the basis of mutual information. Text preprocessing work mainly comprises the following steps: removing a document sign, removing stop words, carrying out word segmentation, carrying out the labeling of the part of speech, carrying out statistics on word frequency, data cleaning and the like, and extracting a characteristic word according to a characteristic algorithm. A text classification stage is characterized in that a model parameter is mainly trained for a vectorized training set through a support vector machine algorithm, and a text which needs to be classified is subjected to machine learning classification. The scheme of the invention is applied, a situation that noise characteristics are brought into a machine learning process can be effectively avoided when the characteristic extraction of the text classification is carried out, text classification precision is improved, the scale of a characteristic library is greatly reduced, and memory occupation is lowered.
Owner:SYSU CMU SHUNDE INT JOINT RES INST +1
Binary tree-based SVM (support vector machine) classification method
ActiveCN102915447AReasonable designEasy wiringCharacter and pattern recognitionFuzzy support vector machineClassification methods
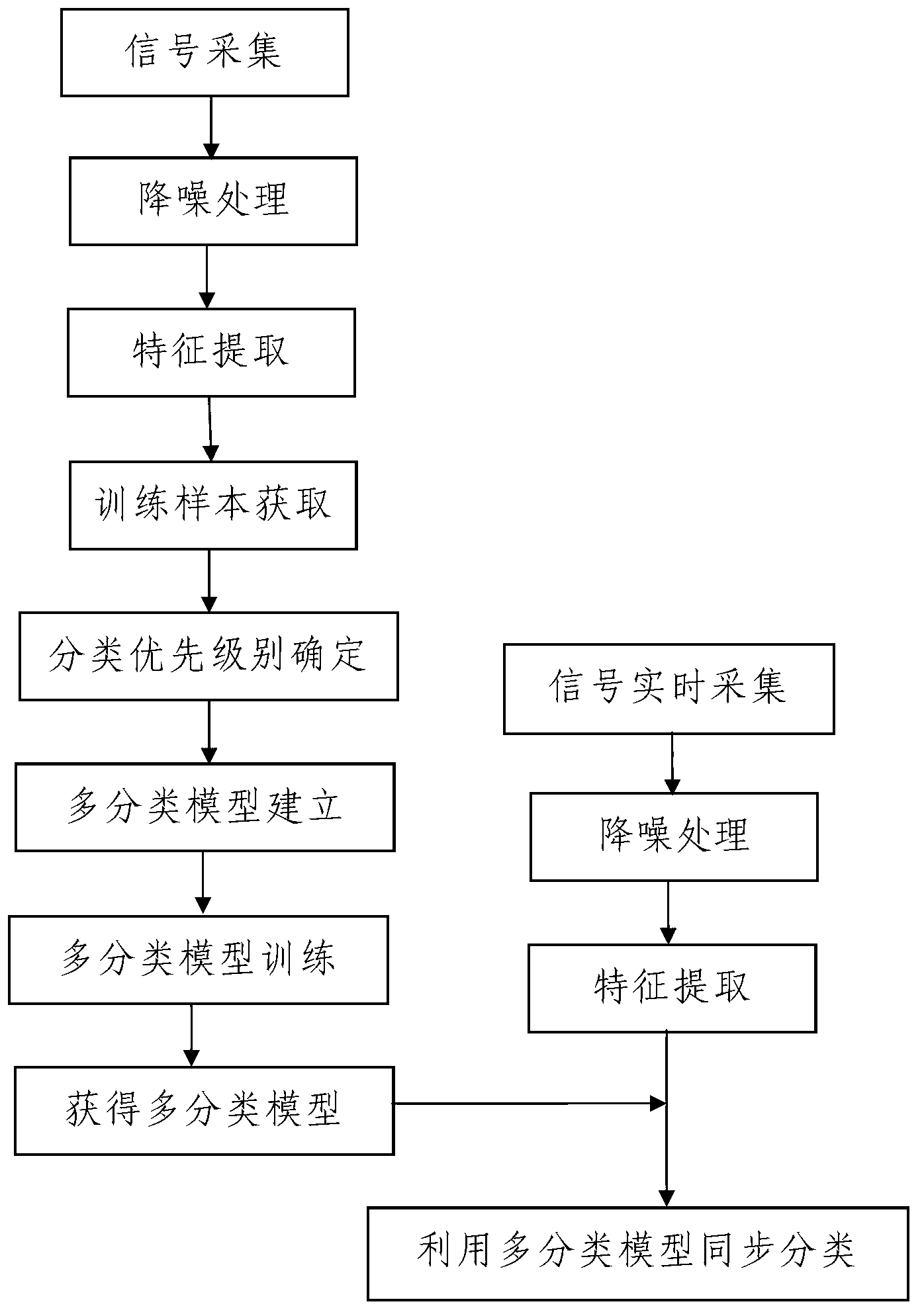
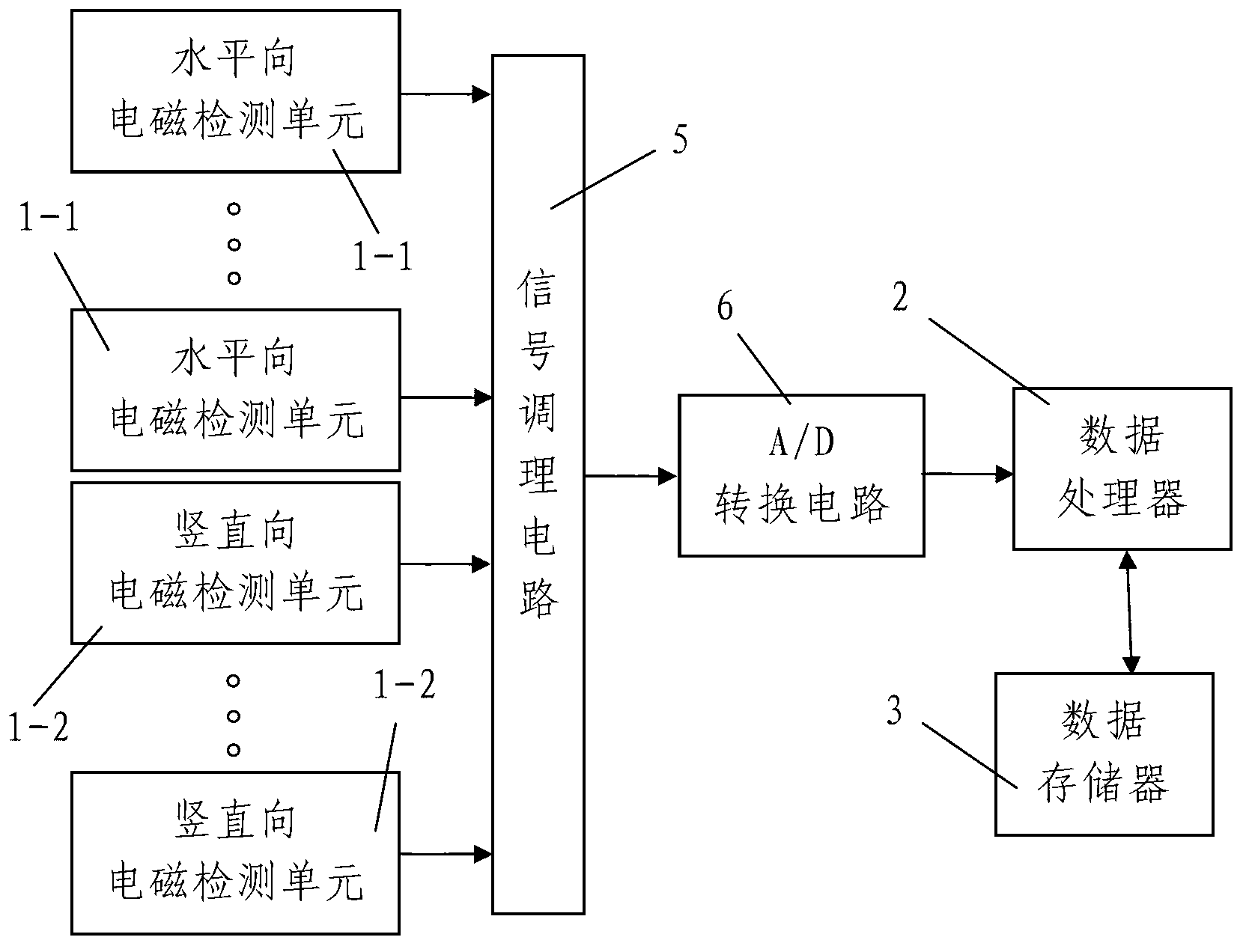
The invention discloses a binary tree-based SVM (support vector machine) classification method. The binary tree-based SVM classification method comprises the following steps: 1, acquiring signals, namely detecting working state information of an object to be detected in N different working states through a state information detection unit, synchronously transmitting the detected signals to a data processor, and acquiring N groups of working state detection information which corresponds to the N different working states; 2, extracting characteristics; 3, acquiring training samples, namely randomly extracting m detections signals to form training sample sets respectively from the N groups of working state detection information which are subjected to the characteristic extraction; 4, determining classification priority; 5, establishing a plurality of classification models; 6 training a plurality of classification models; and 7, acquiring signals in real time and synchronously classifying. The binary tree-based SVM classification method is reasonable in design, easy to operate, convenient to implement, good in use effect and high in practical value; and optimal parameters of an SVM classifier can be chosen, influence on the classification due to noises and isolated points can be reduced, and classification speed and precision are improved.
Owner:XIAN UNIV OF SCI & TECH
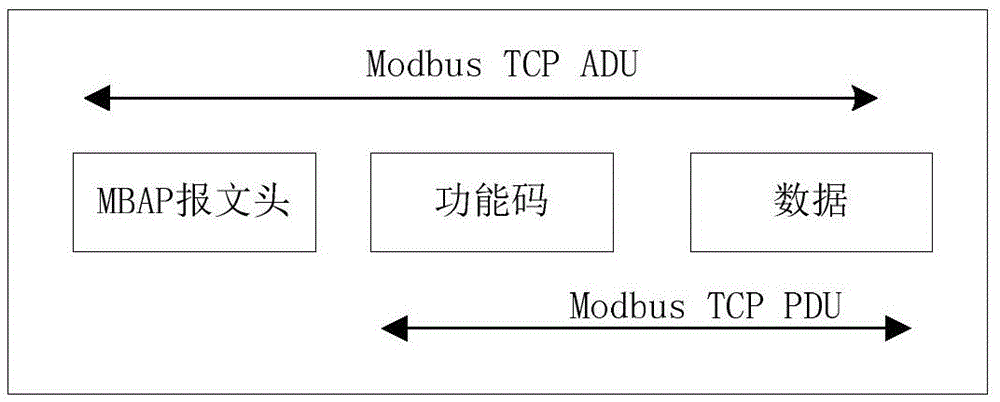
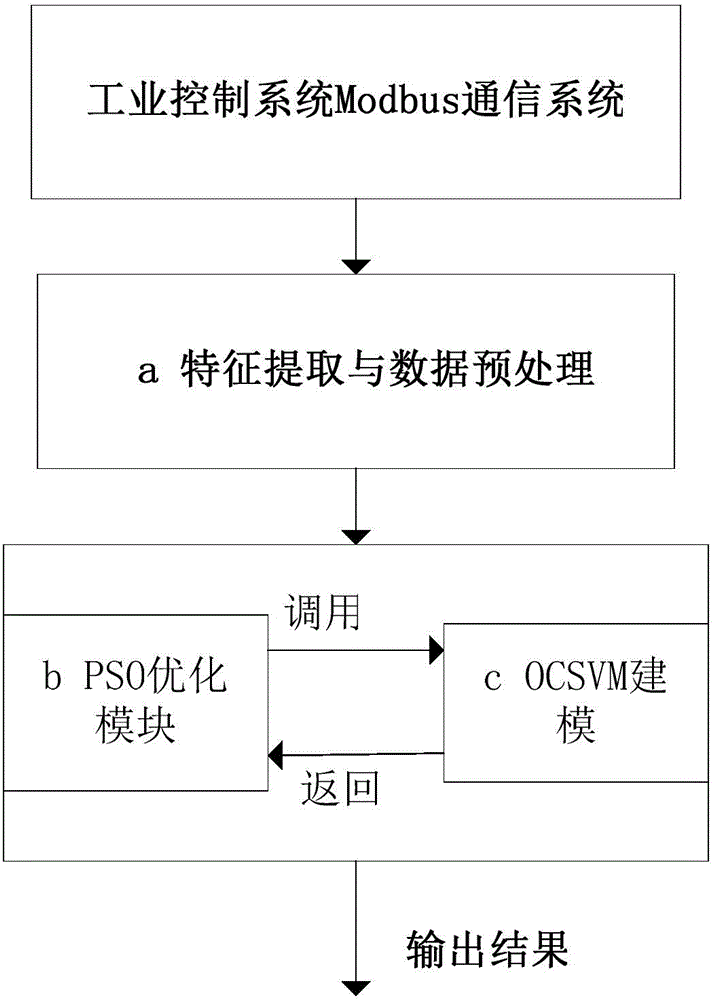
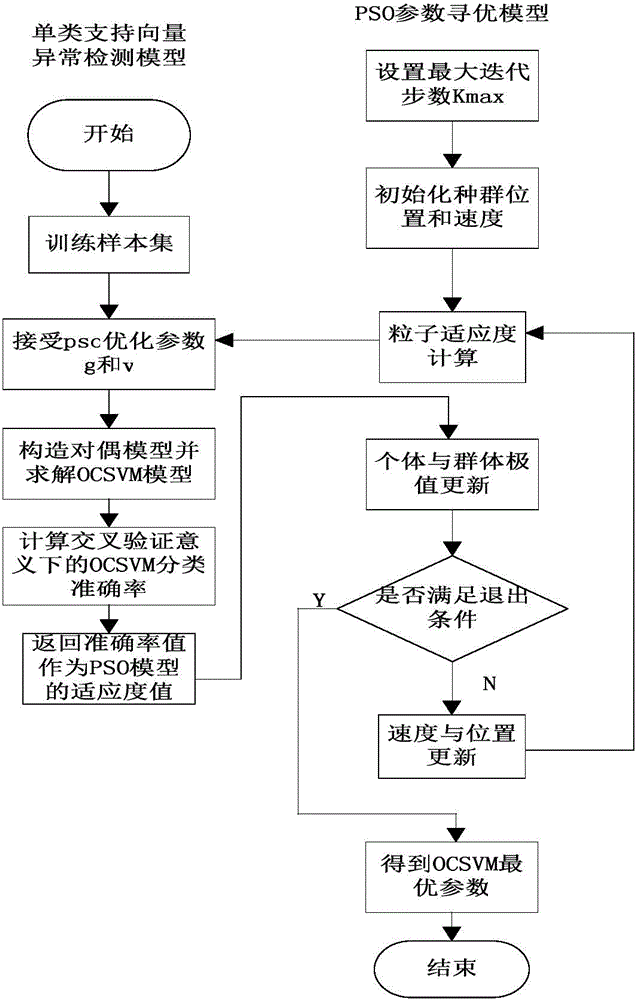
PSO-OCSVM based industrial control system communication behavior anomaly detection method
The invention puts forward a PSO-OCSVM based industrial control system communication behavior anomaly detection method based on an OCSVM algorithm. According to the invention, an improved one-class support vector machine algorithm is adopted to establish a normal communication behavior profile according to a normal Modbus function code sequence, a PSO-OCSVM method for parameter optimization based on a particle swarm optimization (PSO) algorithm is designed, and an intrusion detection model is established to identify abnormal Modbus TCP communication traffic. The method of the invention improves the reliability and efficiency of anomaly detection, and is more suitable for practical application.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Modeling method and modeling device for language identification
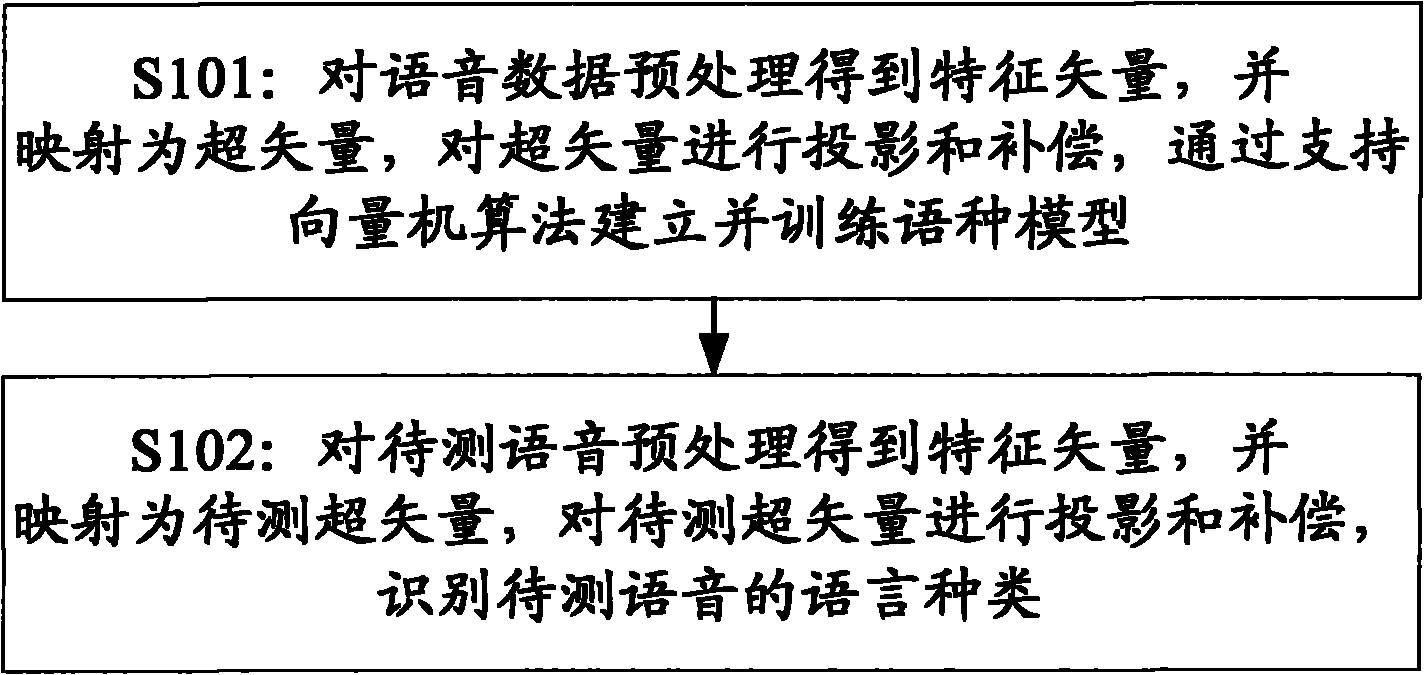
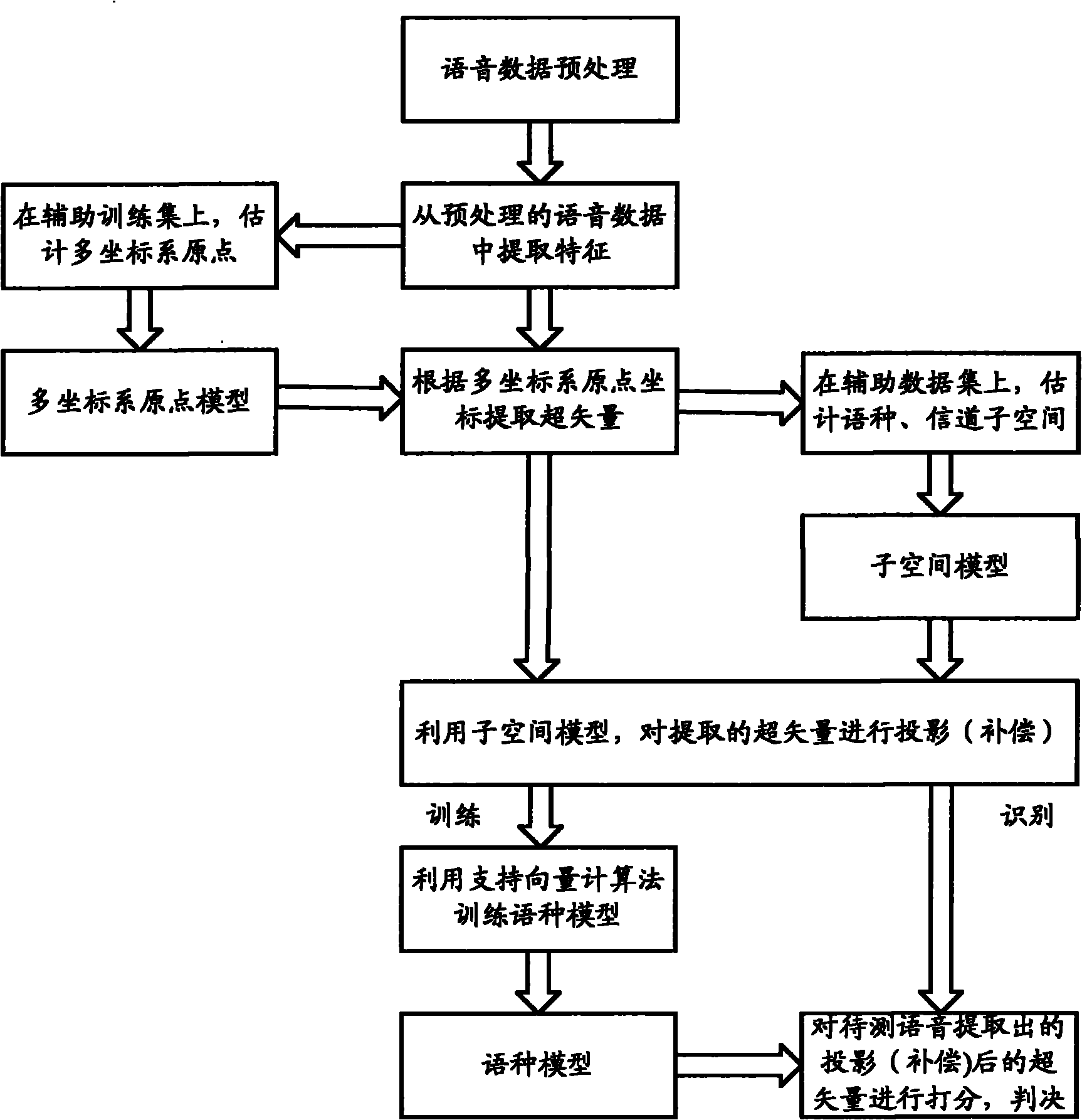
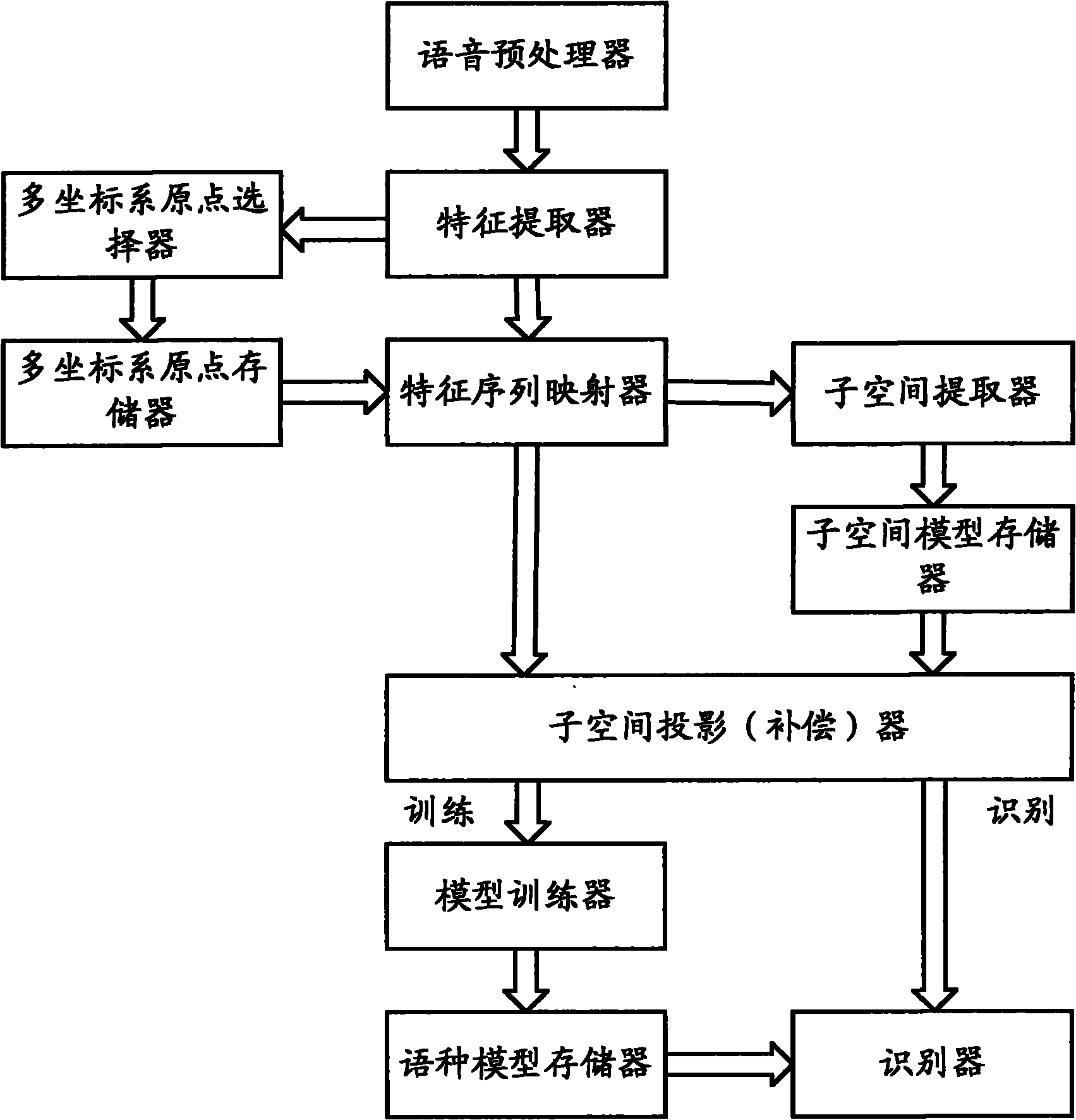
InactiveCN101894548AImprove accuracyReduce operational complexitySpeech recognitionAlgorithmLanguage type
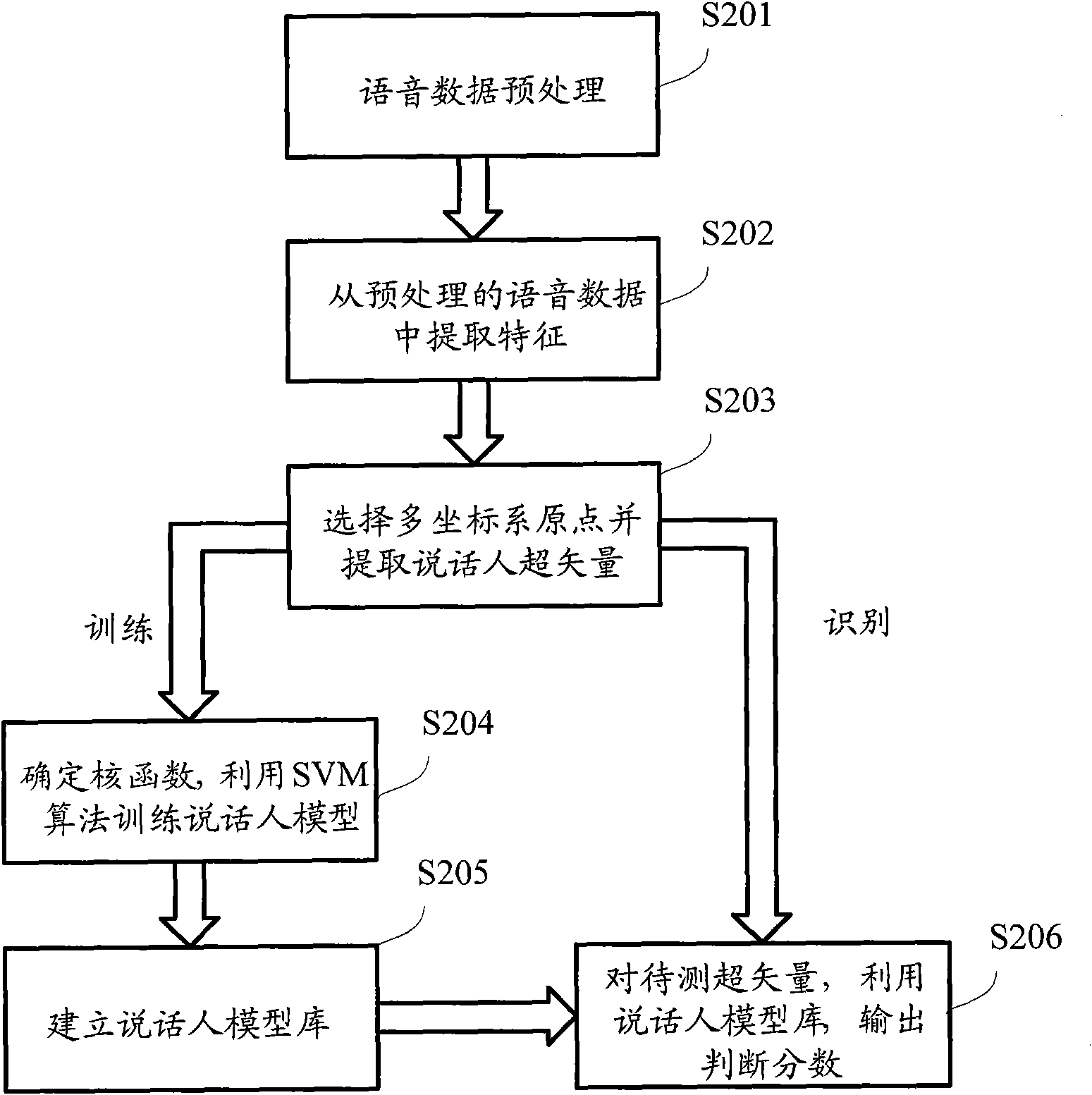
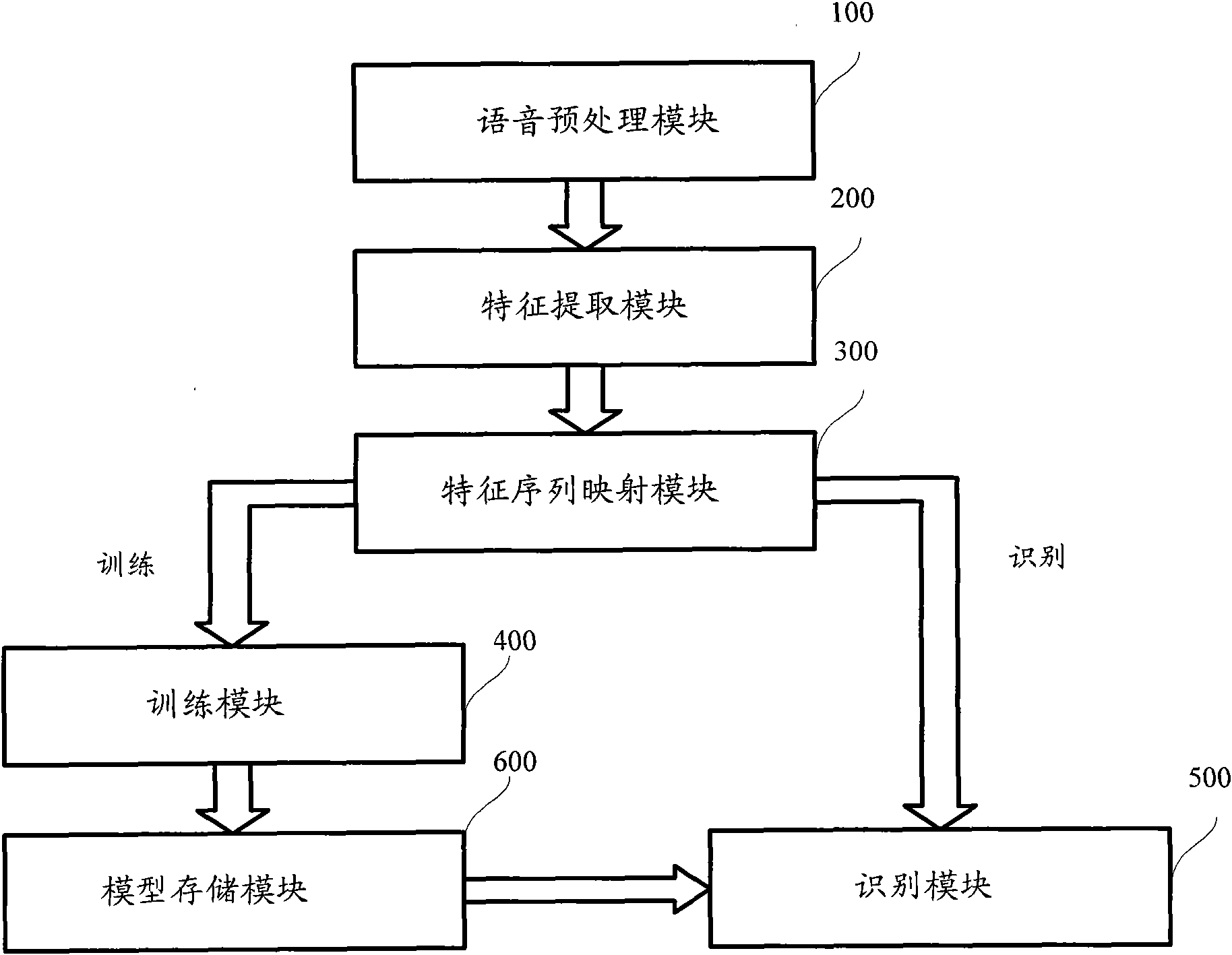
The embodiment of the invention provides a modeling method for language identification, which comprises the following steps of: inputting voice data, preprocessing the voice data to obtain a characteristic sequence, mapping a characteristic vector to form a super vector, performing projection compensation on the super vector, and establishing a training language model through an algorithm of a support vector machine; and adopting the steps to obtain a super vector to be measured of the voice to be measured, performing the projection compensation on the super vector to be measured, grading the super vector to be measured by utilizing the language model, and identifying language types of the voice to be measured. The embodiment of the invention also provides a modeling device for the language identification, which comprises a voice preprocessing module, a characteristic extraction module, a multi-coordinate system origin selection module, a characteristic vector mapping module, a subspace extraction module, a subspace projection compensation module, a training module and an identification module. According to the method and the device which are provided by the embodiment of the invention, information which is invalid to the identification in high-dimension statistics is removed, the correction rate of the language identification is improved, and the computational complexity on an integrated circuit is reduced.
Owner:TSINGHUA UNIV
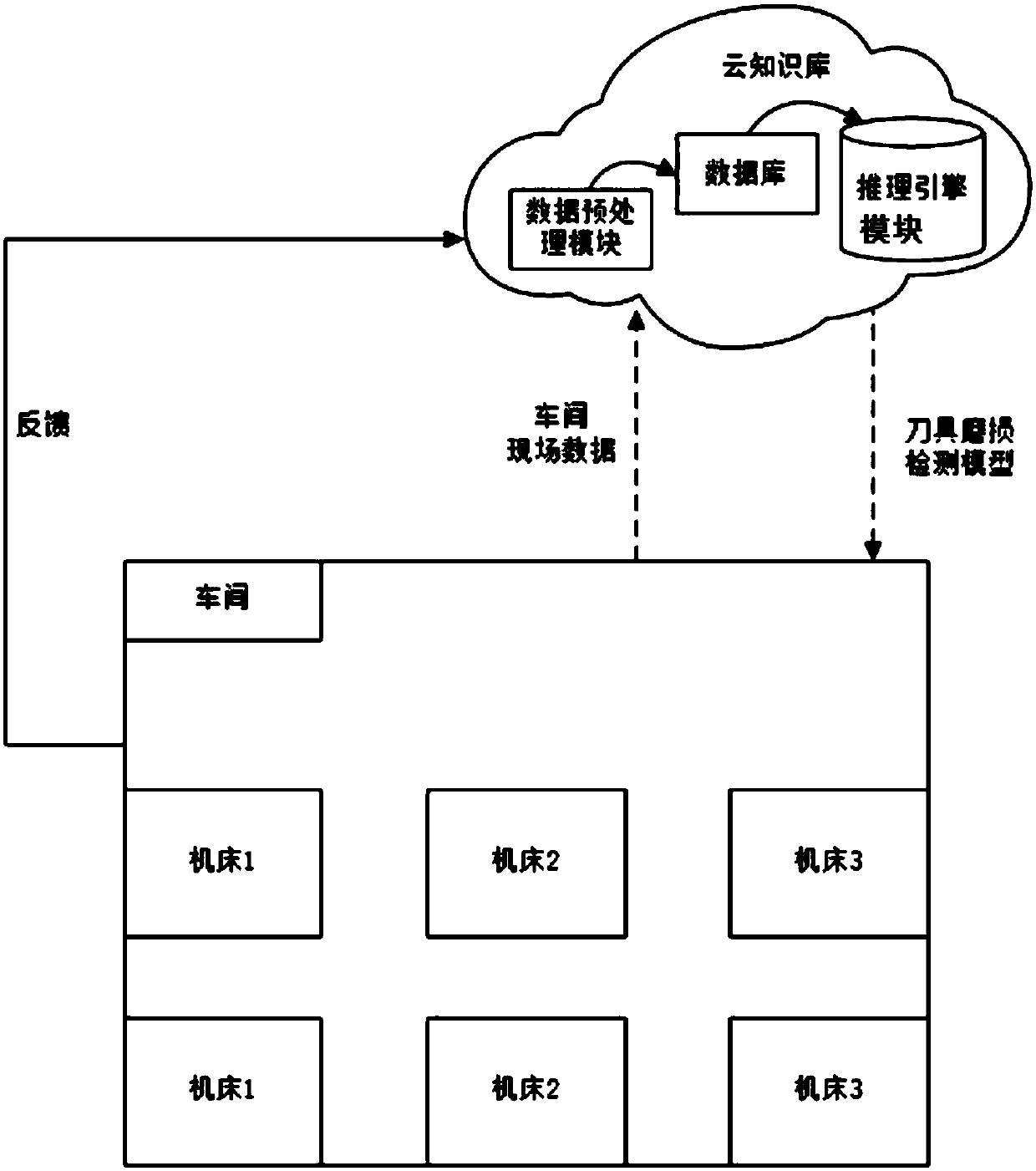
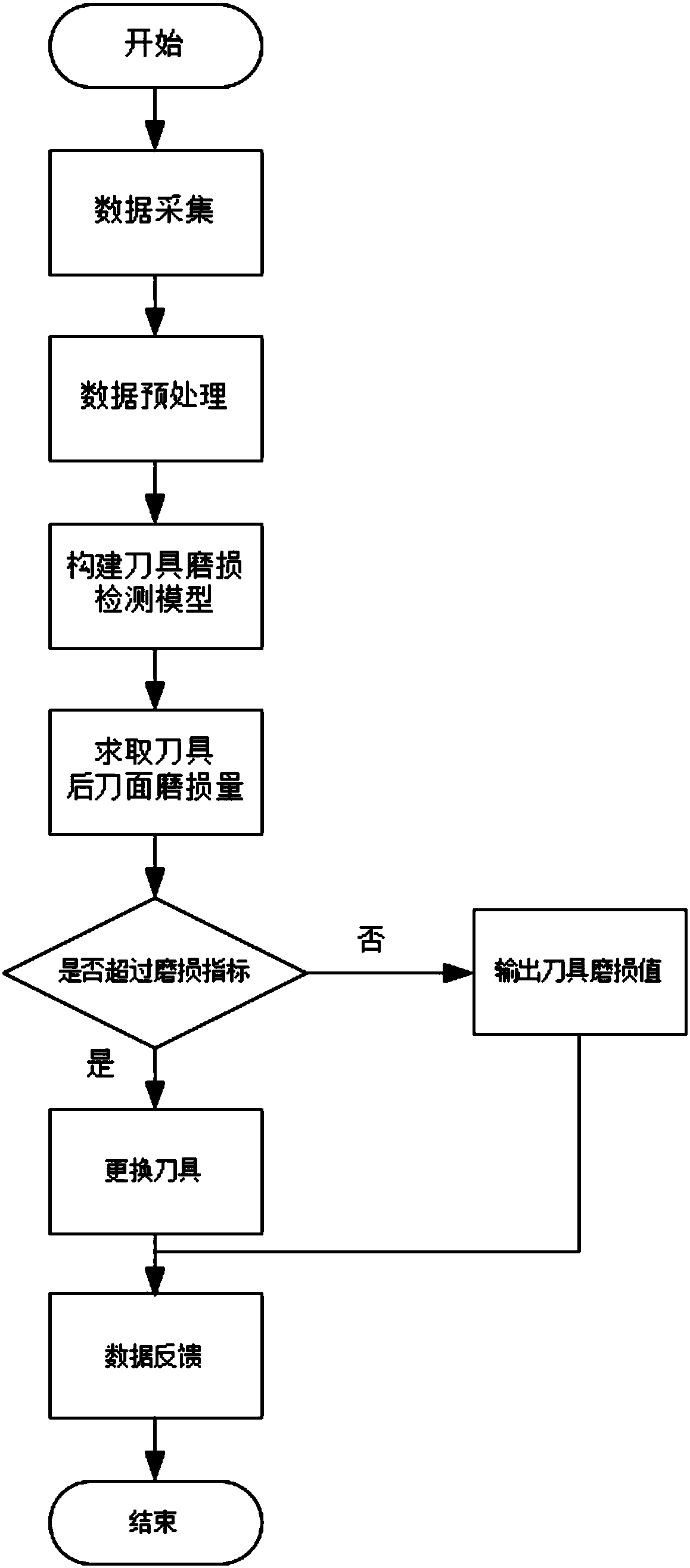
Numerical control device cutter wearing detection method based on cloud knowledge base and machine learning
InactiveCN108107838AImplement storageAchieving processing powerProgramme controlComputer controlNumerical controlComputer science
The present invention relates to a numerical control device cutter wearing detection method based on a cloud knowledge base and machine learning. The method comprises the steps of: A, constructing andtraining a cutter wearing detection model: (1) establishing a cloud knowledge base, (2) collecting condition data of a workshop and storing the condition data, (3) designing a cutter wearing detection model, and employing a support vector machine to perform training of the cutter wearing detection model; and B, performing cutter wearing detection through the cutter wearing detection model: (4) updating the cutter wearing detection model to a local numerical control machine tool, performing detection of a cutter on the local numerical control machine tool, and when the cutter wearing amount achieve a dulling standard, replacing the cutter, and (5) taking newly detected condition data and the detected cutter wearing amount as feedback information, and transmitting the feedback information to the local numerical control machine tool through a network. The cutter wearing cutter prediction accuracy rate and the detection speed are improved.
Owner:SHANDONG UNIV
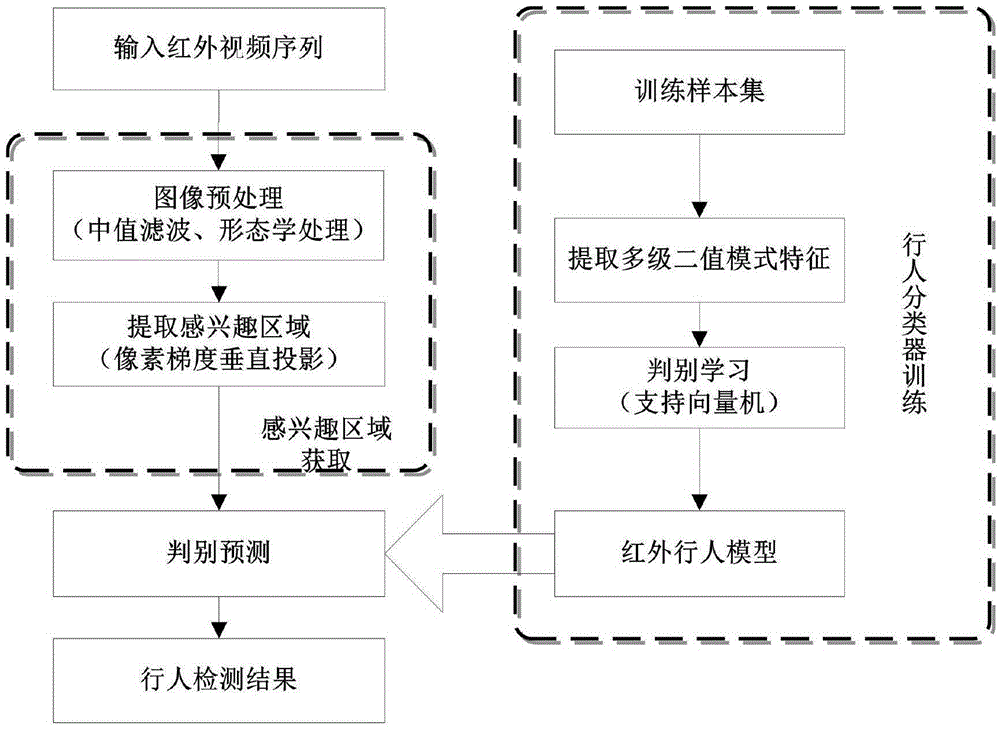
Infrared-based night intelligent vehicle front pedestrian detection method
InactiveCN105404857AReduce noiseImprove real-time performanceScene recognitionVertical projectionFeature description
The invention provides an infrared-based night intelligent vehicle front pedestrian detection method. The method comprises the following steps that de-noising preprocessing is performed on input infrared image sequences by utilizing a smoothing filtering method and a morphological processing technology; pedestrian preselection areas in the input image sequences are captured by a vertical projection method based on pixel gradients, and areas of interest are extracted from the pedestrian preselection areas according to pedestrian geometric features; infrared image multistage binary mode feature description areas of interest are extracted; a pedestrian classifier model is offline trained by utilizing a support vector machine algorithm; and the areas of interest are judged to be target pedestrians or backgrounds online by utilizing the classifier model. Compared with methods in the prior art, robustness of the pedestrian classifier is effectively improved by the method so that the method can detect vertical pedestrians in the still, walking or running and other movement modes and the method is also suitable for detecting human bodies riding bicycles or motorcycles, and a system realized based on the method can be applied to barrier detection for an unmanned intelligent vehicle and a wheeled robot, etc.
Owner:BEIJING UNION UNIVERSITY
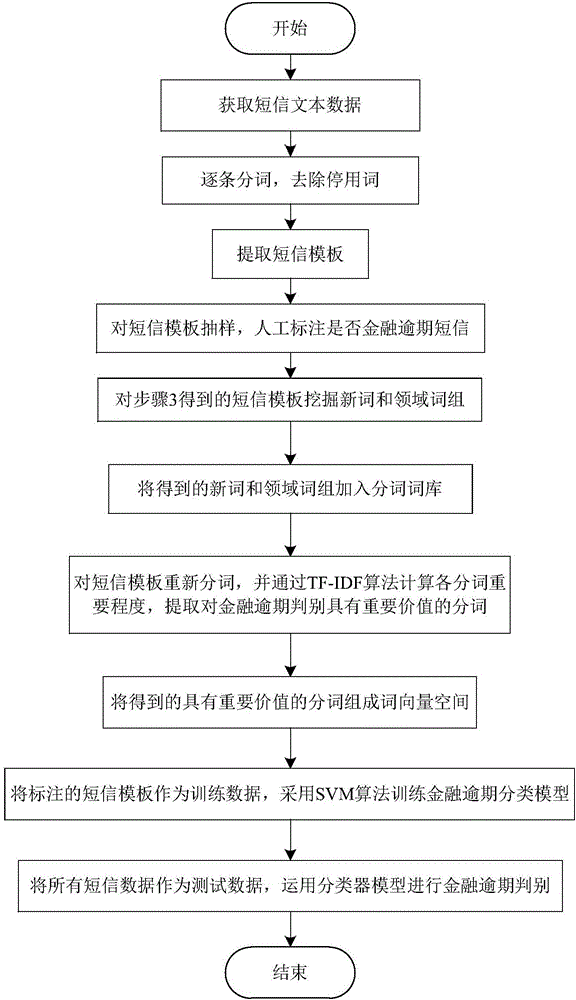
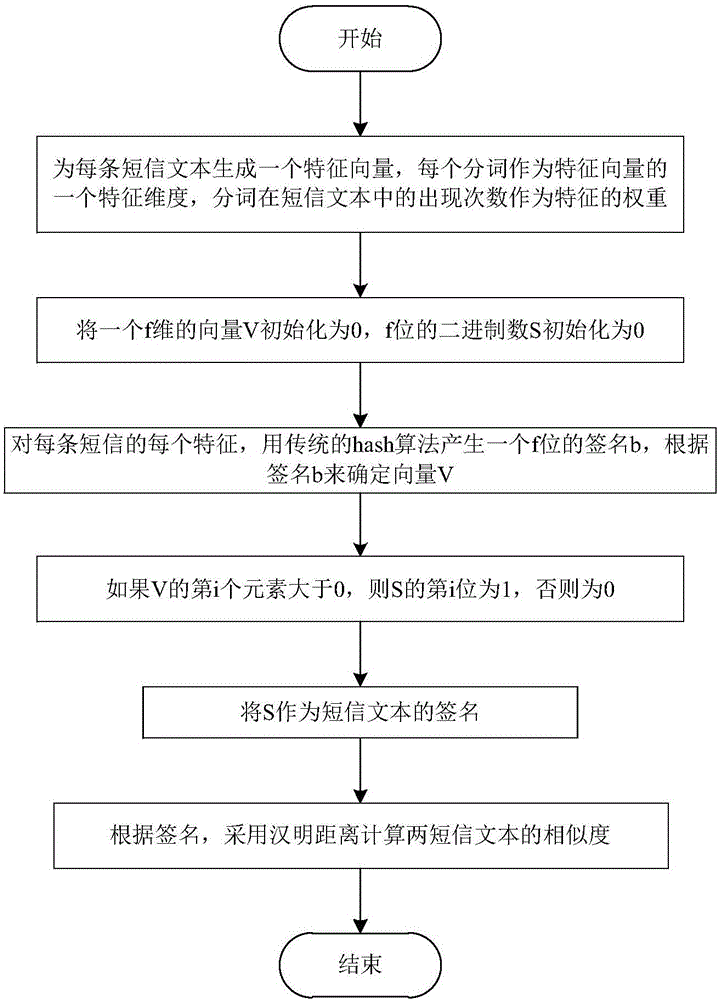
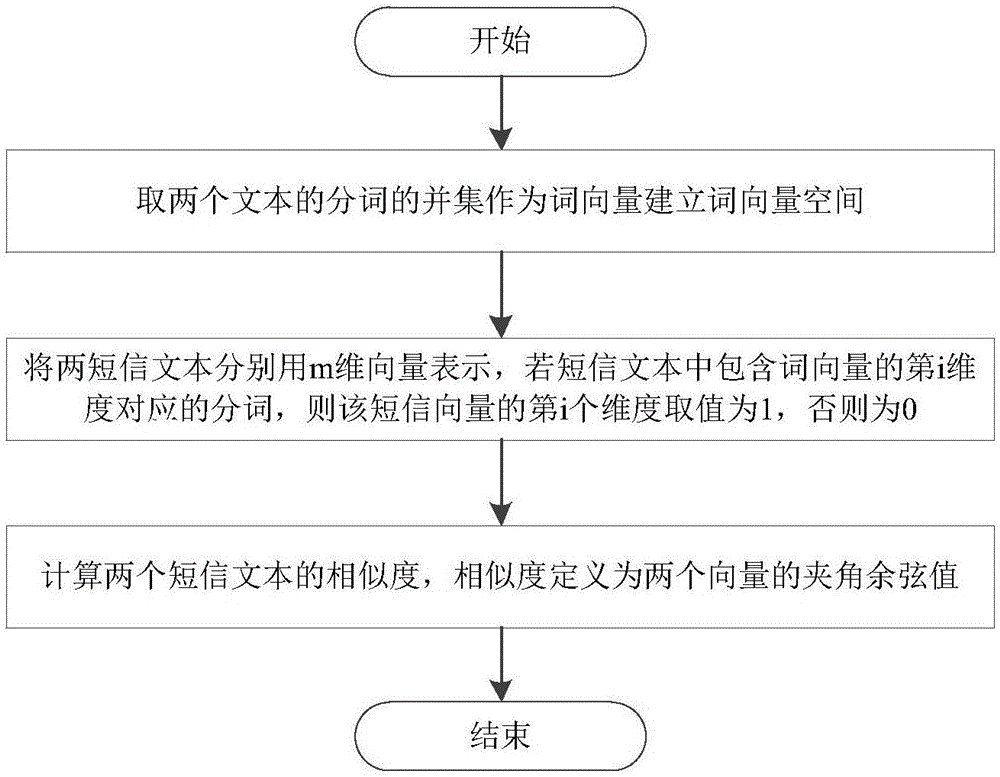
Text mining-based financial expiry short message intelligent judgment method
ActiveCN106547738AHigh precisionIntelligent discriminationFinanceNatural language data processingText miningWord group
The invention discloses a text mining-based financial expiry short message intelligent judgment method and belongs to the field of text data mining. The method mainly comprises the steps of obtaining short message texts, performing word segmentation, calculating the similarity of the short message texts, and extracting short message templates; sampling and tagging whether the short message templates are financial expiry short messages or not; performing word segmentation on all the short message templates, mining new words and field word groups, and forming a new word library; performing word segmentation on the short message templates again by using the new word library, extracting segmented words with important values for expiry judgment, and forming eigenvector spaces; and taking the tagged short message templates as training data, training a financial expiry classifier model by adopting a support vector machine algorithm, inputting all short messages after training, and performing expiry classification judgment. By adopting the method, the financial expiry related short messages can be quickly extracted from a large amount of short message texts, so that important reference values are provided for personal credit investigation businesses.
Owner:BEIJING EMAY SOFTCOM TECH
Identifying Possible Disease-Causing Genetic Variants by Machine Learning Classification
The techniques described herein relate identification of disease-causing genetic variant by machine learning classification. The techniques may include receiving a training dataset of predetermined variants associated with disease. A hyperplane is identified having a maximum margin between points of the dataset. Patient input data is received including an observed variant of a gene. Features of the observed variant are selected, and a score is determined The score is determined using Support Vector Machine algorithms based on an observation of a novel non-linear relationship with the selected features of the observed variant. The observed variant may be classified based on the score indicating a distance of the observed variant from the identified hyperplane.
Owner:PIERIANDX INC
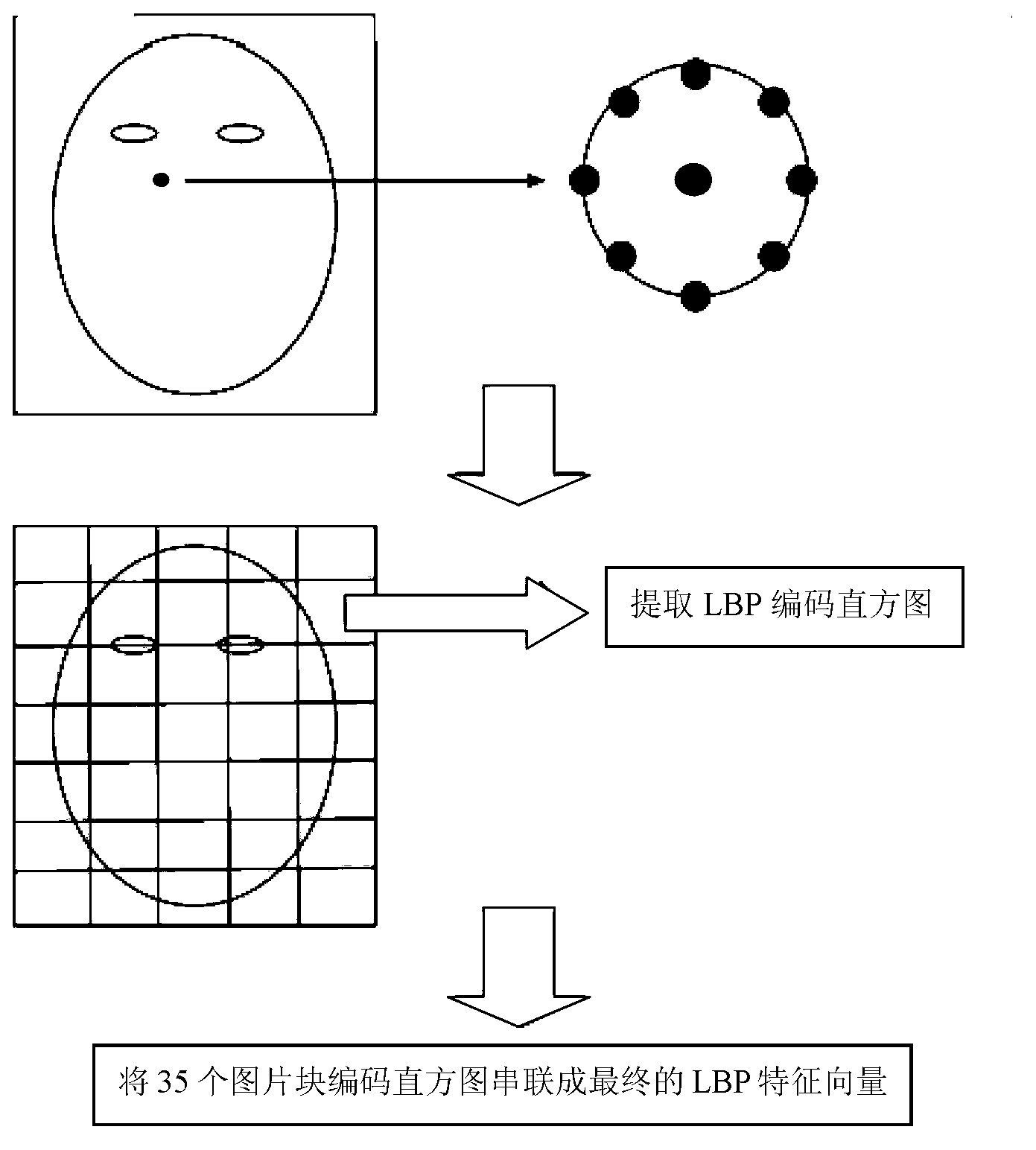
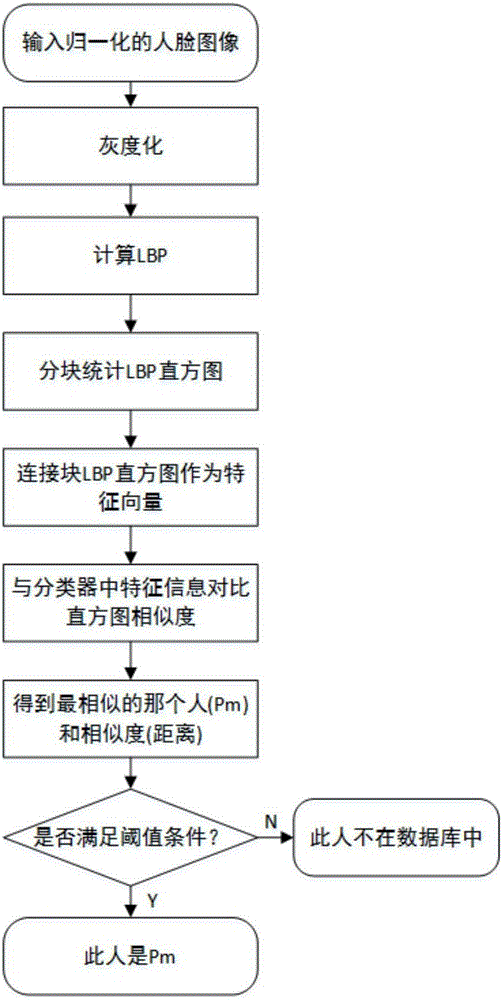
Facial feature extraction method and face recognition method based on large-scale image data
ActiveCN102938065AImprove accuracyReduce correlationCharacter and pattern recognitionFace detectionFeature vector
The invention discloses a facial feature extraction method and a face recognition method based on large-scale image data. The facial feature extraction method comprises the following steps of: 1) establishing a face image database A, wherein each person has face images with multiple expressions, postures and illumination, and establishing a face image database B; 2) performing face detection on each image in the databases A and B, and outputting a rectangular frame comprising the face, and pixel coordinates of the two eyes; 3) correcting and zooming each face image, generating an image with a set standard format, and extracting a bottom texture feature vector; 4) training a classifier capable of recognizing each person a by utilizing a support vector machine algorithm for the person a in the database A; and 5) generating a new face image into an image with a set standard format, judging the bottom texture feature vector of a new face by utilizing each classifier, and establishing a vector according to a criteria score to serve as a feature vector of the new face image. According to the extraction method, the robustness of an extracted face feature is greatly improved.
Owner:BEIJING KUANGSHI TECH
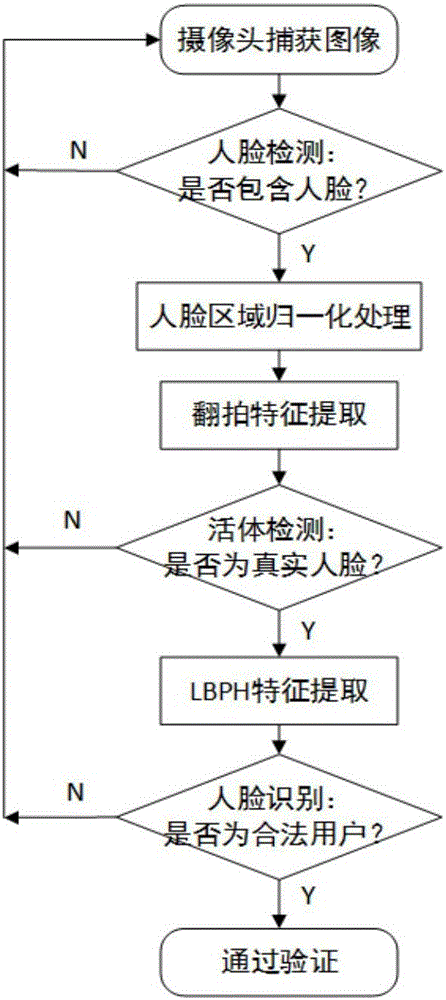
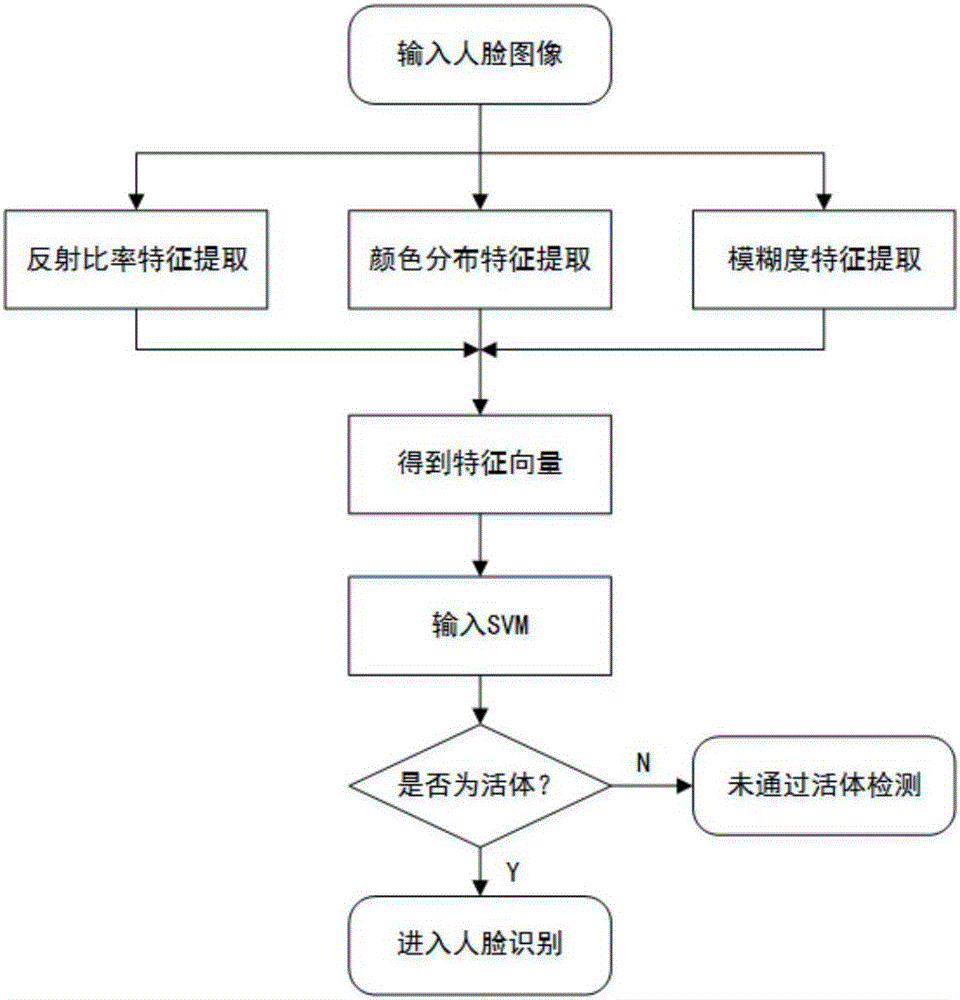
Face recognition method for identifying counterfeit photo deception
InactiveCN106650669ANot vulnerable to targeted attacksImprove robustnessSpoof detectionColor imageMirror reflection
Owner:CHONGQING UNIV OF POSTS & TELECOMM
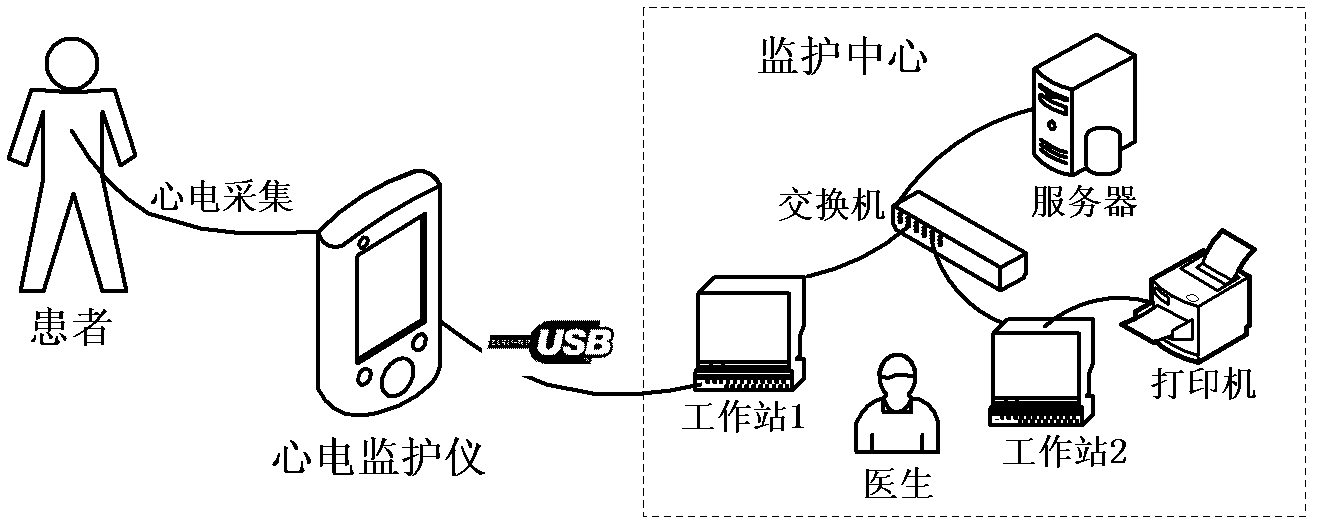
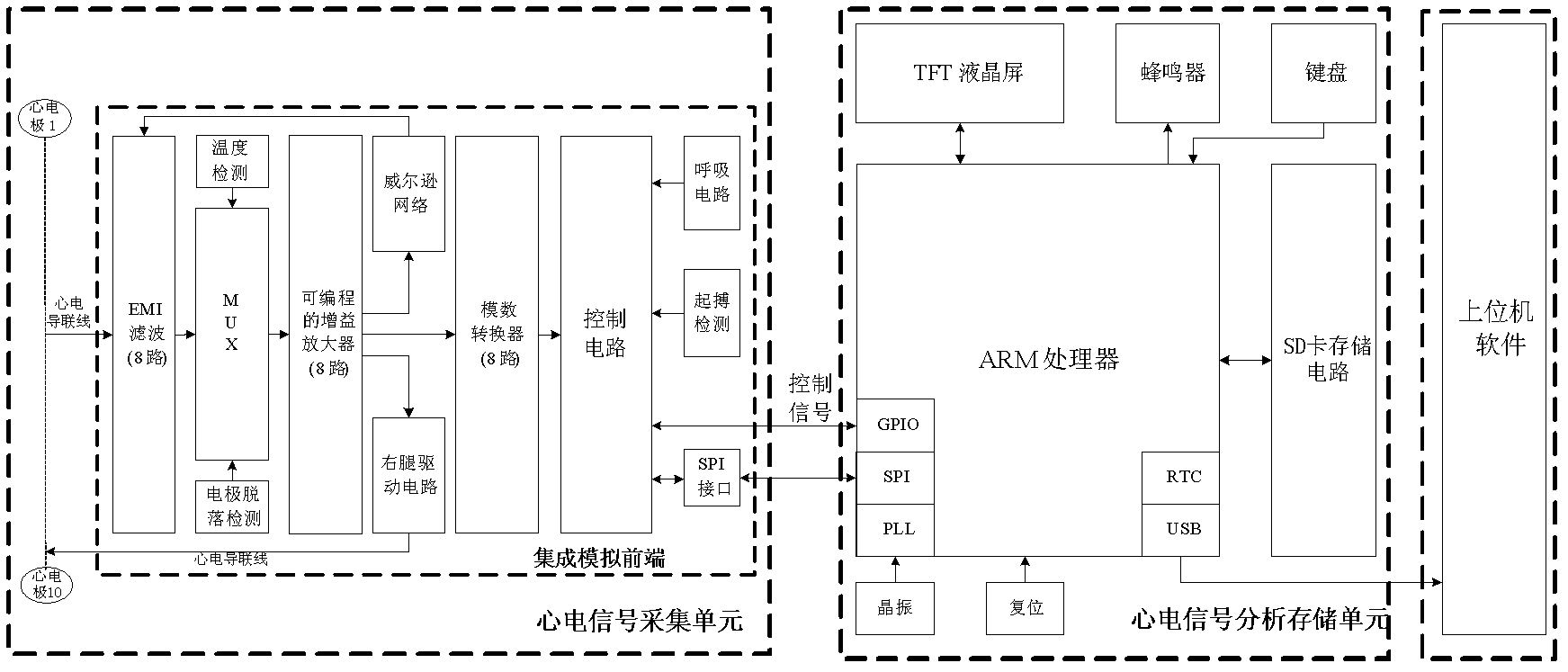
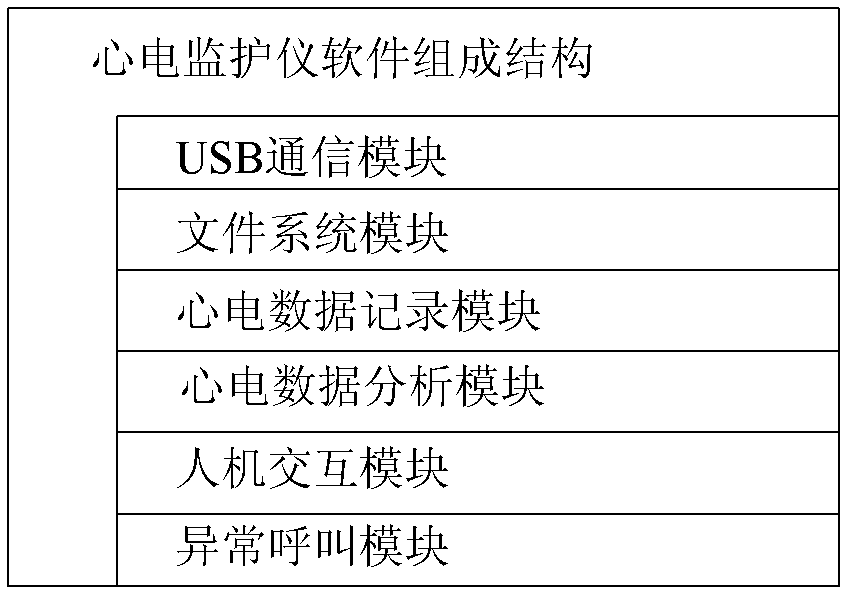
Low-power consumption portable electrocardiograph monitor and control method thereof
InactiveCN102274020AHigh measurement accuracyHighly integratedDiagnostic recording/measuringSensorsEcg signalElectrocardiographic monitor
The invention relates to a low-power consumption portable electrocardiograph monitor and a control method thereof, which belongs to the field of medical appliances. The portable electrocardiograph monitor comprises an electrocardiosignal collection unit, an electrocardiosignal analysis and storage unit and an upper computer. The control method comprises the following steps of: step 1: carrying out digital filtering to collected signals by using a wavelet entropy optimal threshold denoising method; step 2: carrying out rejection of baseline drift to the signals processed by step 1 by using a morphological filtering method; and step 3: carrying out disease classification to the signals processed by step 2 by using a support vector machine algorithm. The invention has the advantage of high integrity, and has the characteristics of portability, compactness and economy.
Owner:NORTHEASTERN UNIV
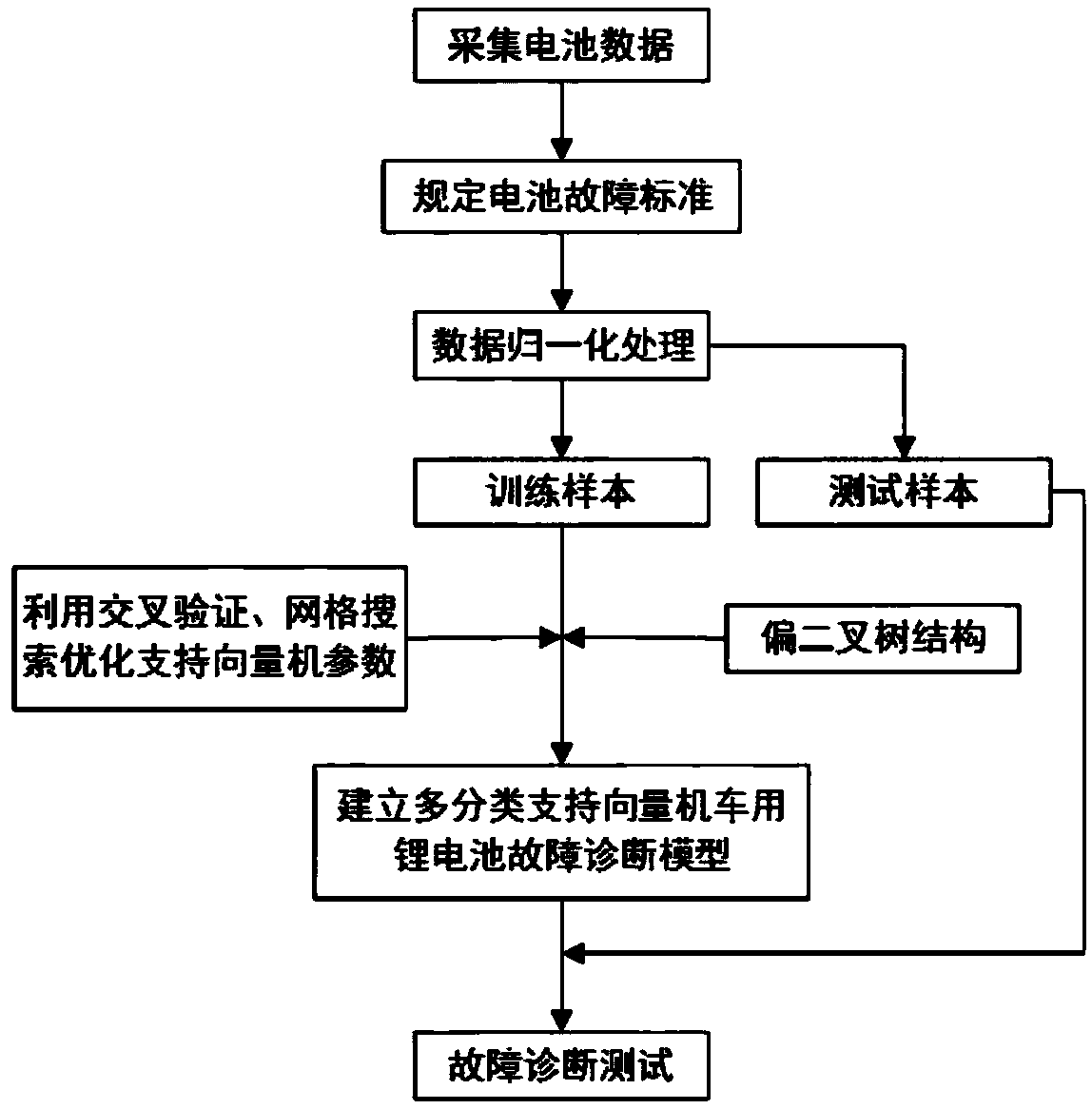
Fault diagnosis method of vehicle lithium battery based on multi-class support vector machine algorithm
ActiveCN109165687ASolve the problem of repeated classificationReduce the numberCharacter and pattern recognitionResourcesDiagnosis methodsEngineering
A fault diagnosis method of a vehicle lithium battery based on a multi-class support vector machine algorithm belongs to the field of vehicle lithium battery fault diagnosis. In order to solve the problem that the existing vehicle lithium battery fault diagnosis technology requires high amount of training data, which leads to the difficulty of realizing real-time on-line fault detection, the method of the invention comprises the following steps of: grouping battery samples into experiments, and sorting the collected data to form a training set and a test set; specifying battery failure criteria; using cross-validation and network search methods to optimize the parameters; constructing a kernel function support vector machine; constructing as biased binary tree five-class support vector machine to get the fault diagnosis model of vehicle lithium battery which can identify different states of lithium battery. The method can quickly and accurately complete the fault diagnosis of a lithiumbattery for a vehicle.
Owner:HARBIN UNIV OF SCI & TECH
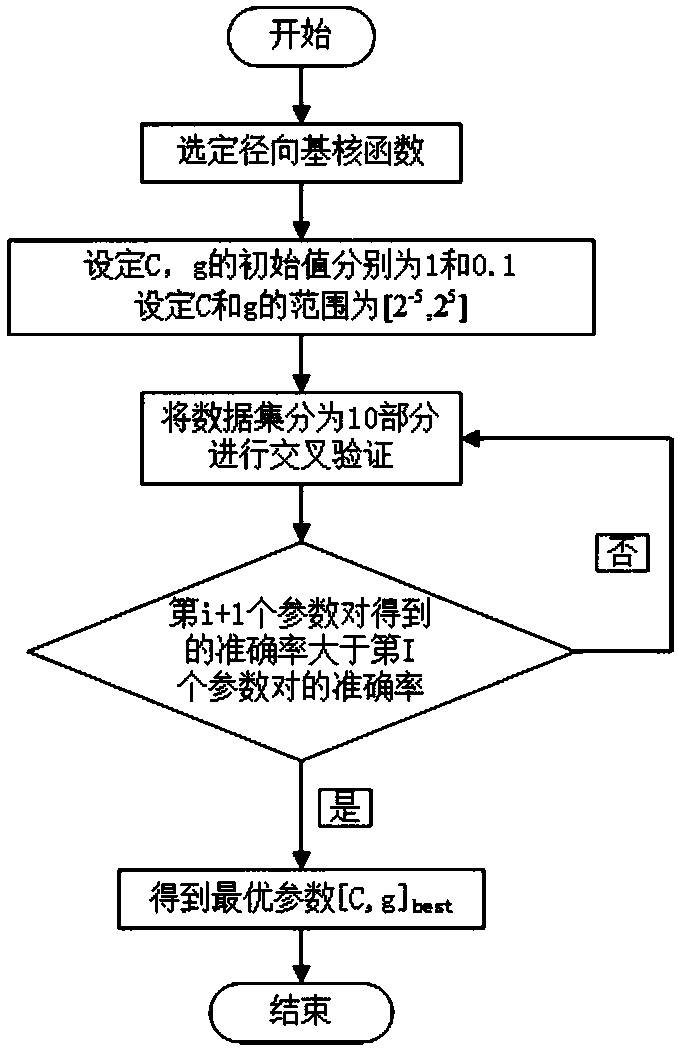
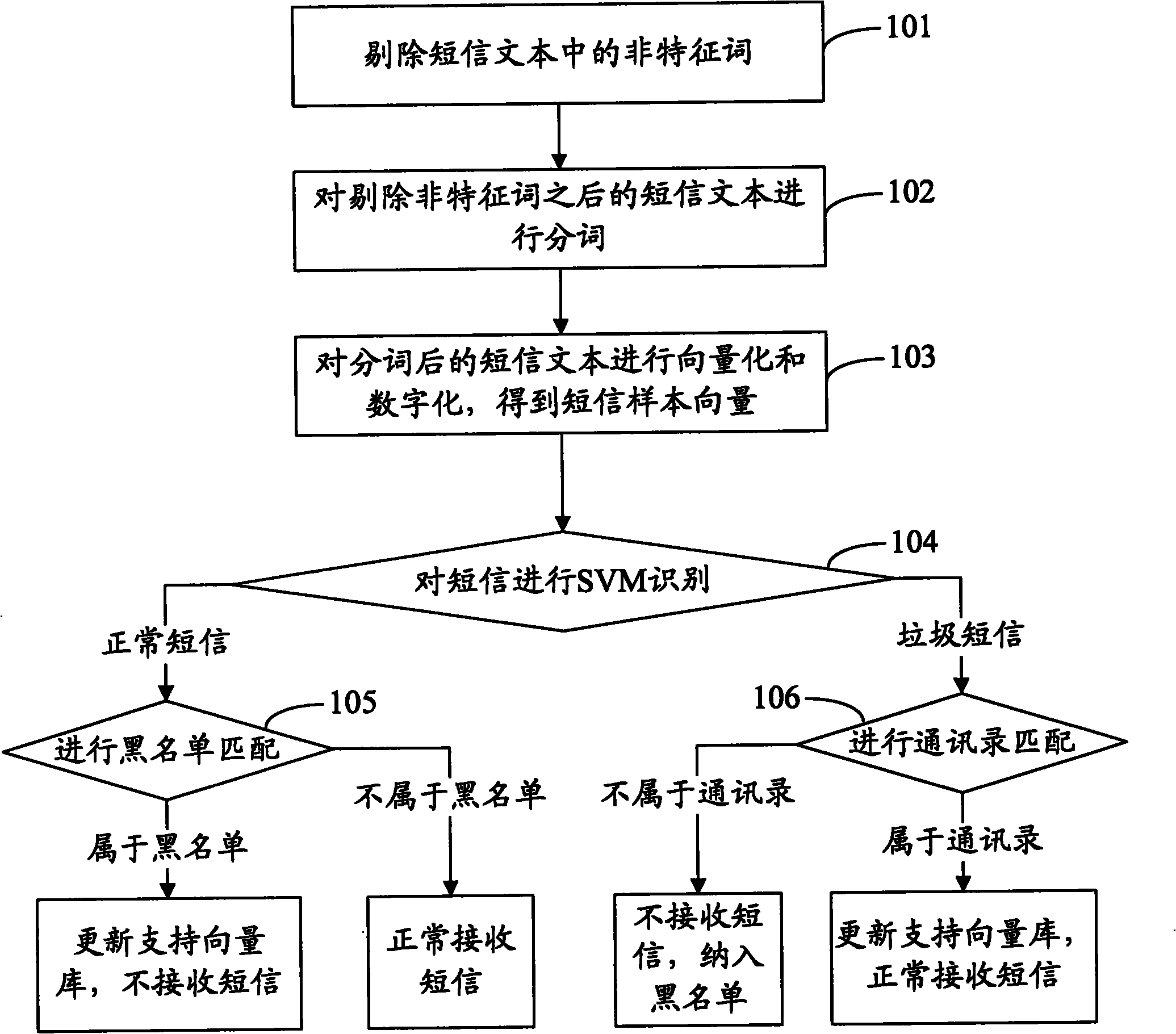
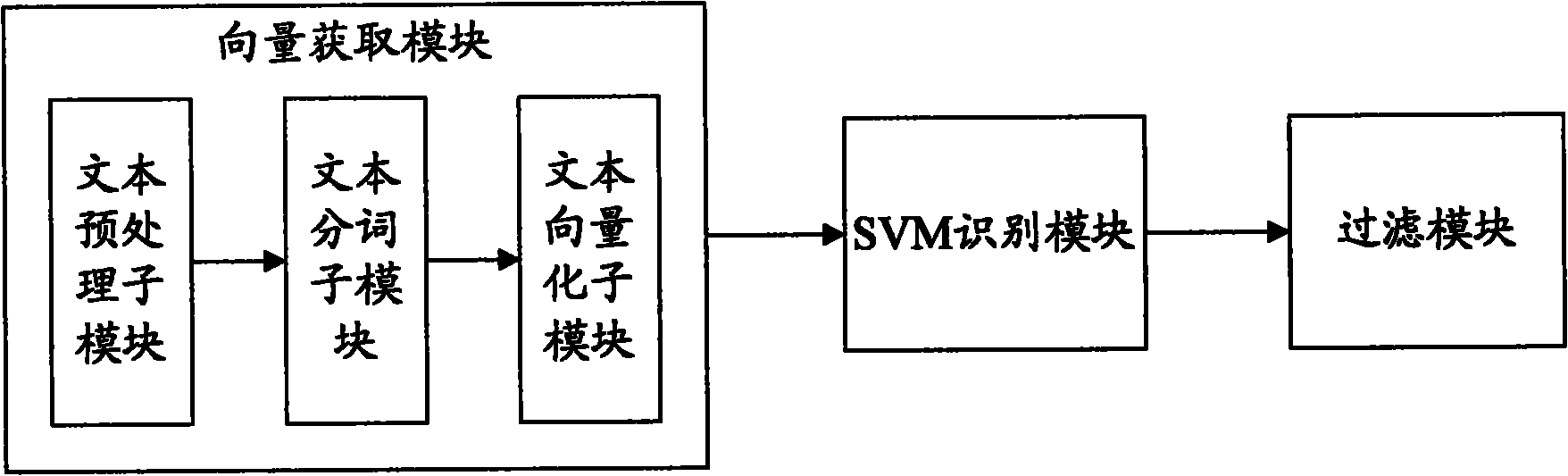
Mobile terminal and filtering method of short messages thereof
The invention discloses a mobile terminal and a filtering method of short messages thereof. A support vector machine algorithm is used for sorting short messages, and simultaneously, a self-feedback function is provided; simple address list or black list matching operation is carried out based on the sorted short messages; and wrongly sorted short messages are fed back and learned to update a support vector library. Thus, the support vector library is continuously perfected, and the filtering capacity is continuously adjusted automatically and enhanced. Because the support vector machine algorithm and the address list or black list matching operation are combined for use, the scheme of the invention can aim at the short messages in various formats and especially can filter the short messages which do not belong to a black list or an address list.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
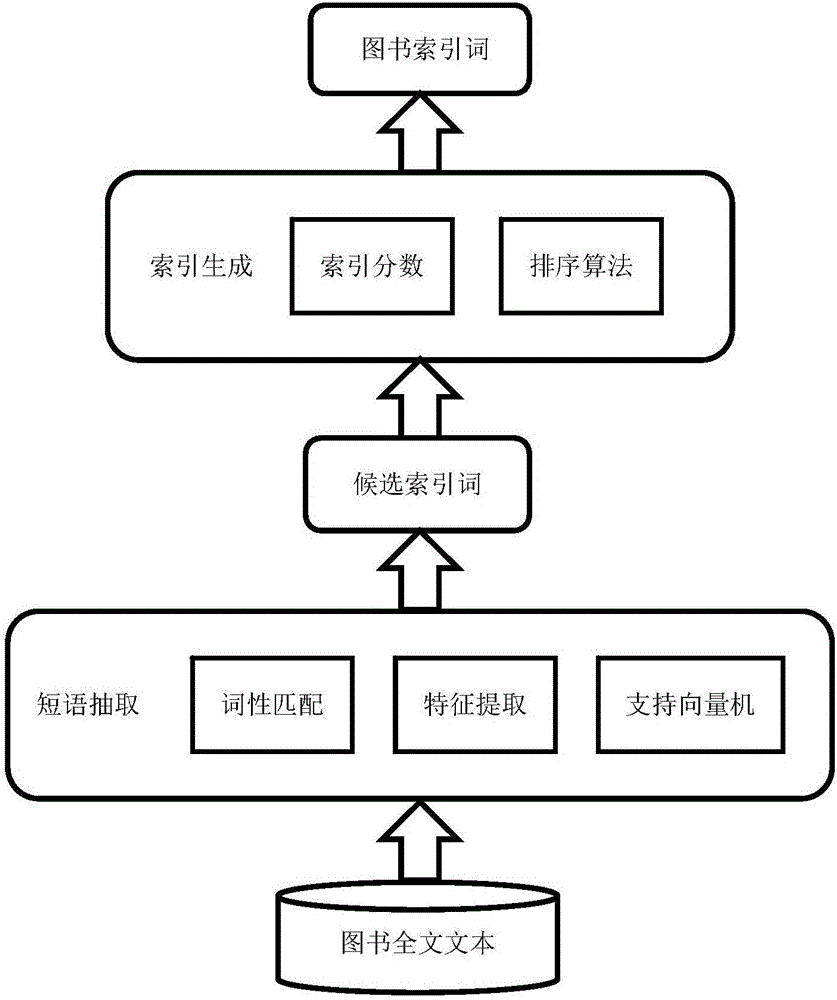
Method for automatically establishing back-of-book indexes of book based on book contents
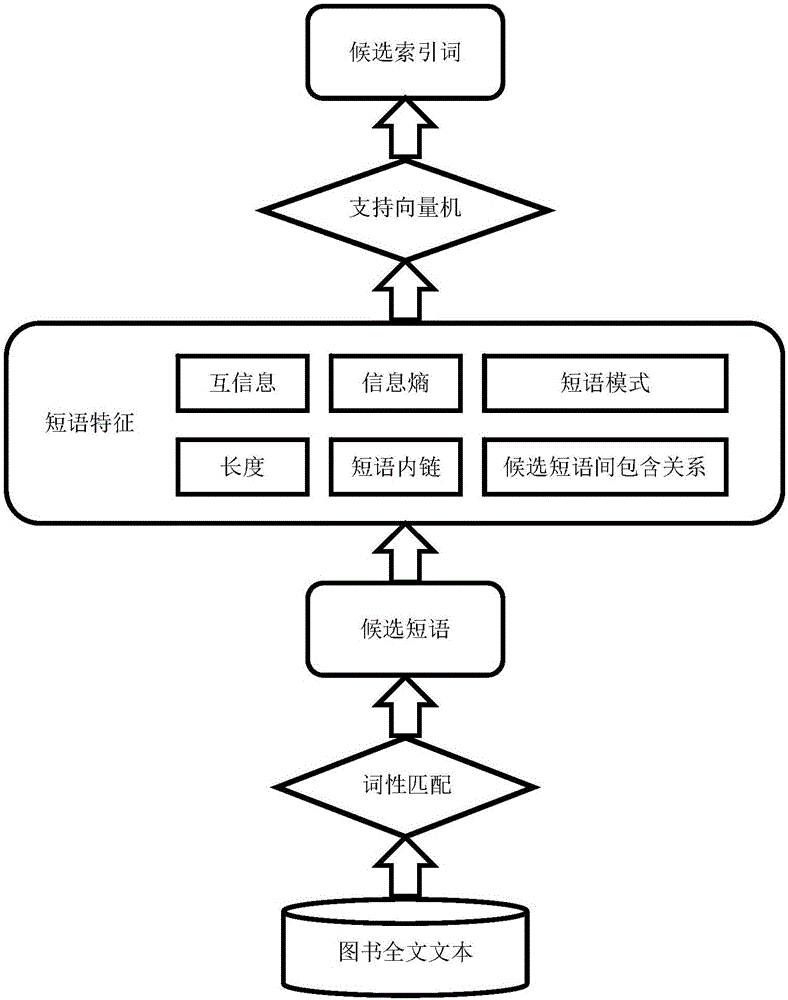
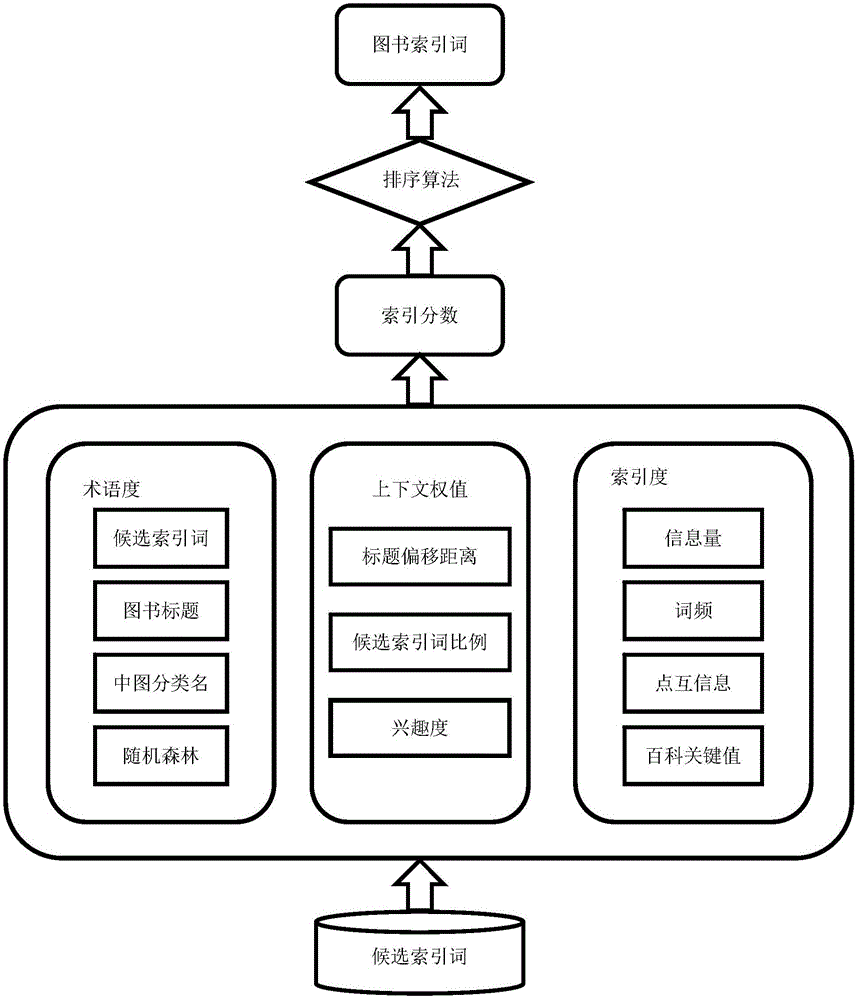
ActiveCN106649597AEvenly distributedRealize generationSemantic analysisSpecial data processing applicationsArray data structureEncyclopedia
The invention discloses a method for automatically establishing back-of-book indexes of a book based on book contents. The method comprises the following steps: first, analyzing text in a digital book; taking a chapter as a unit, and performing part-of-speech tagging on the text by using a natural language processing tool to obtain a part-of-speech array; matching by utilizing a high-frequency part-of-speech rule, and extracting candidate phrases; then, classifying to obtain the phrases to serve as candidate index terms by using a support vector machine algorithm by utilizing semantic and grammatical characteristics; calculating the similarity between the candidate index terms and the field corresponding to the book to serve as termhood; calculating information amounts, term frequency, point mutual information and encyclopedia key values to obtain an index degree; calculating a title offset distance, a candidate index term proportion and interestingness to obtain a context weight value; finally, combining the termhood, the indexing degree and the context weight value to obtain an index score, and obtaining the book index terms through limited sequencing. According to the method, the indexes can be added to the book which does not have the back-of-book terms, and the readability and the searchability of the book are improved.
Owner:ZHEJIANG UNIV
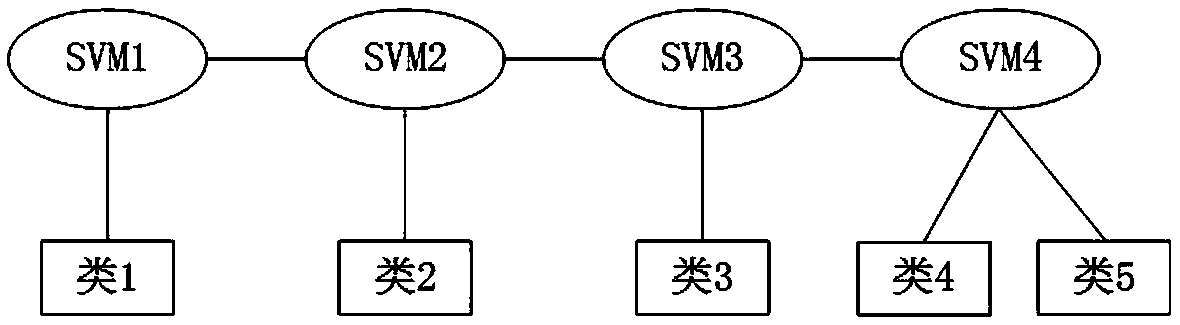
MSVM (multi-class support vector machine) electroencephalogram feature classification based method and intelligent wheelchair system
ActiveCN103473294AWheelchairs/patient conveyanceSpecial data processing applicationsExperimental validationBrain computer interfacing
The invention discloses an MSVM (multi-class support vector machine) electroencephalogram feature classification based method, and relates to the fields of feature classification and identification control of brain-computer interface technology. A support vector machine is adopted to perform feature classification on electroencephalograms, and aiming for the problem about parameter selection of an existing support vector machine algorithm, an improved parameter optimization method is provided. In order to achieving the multi-classification purpose, the principle and the structure of a multi-class support vector machine are researched on the basis of binary classification. Through analysis and comparison, the multi-class support vector machine in a binary tree form is selected to perform multi-feature classification, and the improved parameter optimization method is subjected to experimental verification under an offline environment.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Speaker recognition method based on multi-coordinate sequence kernel and system thereof
InactiveCN101640043AReduce operational complexityImprove accuracySpeech recognitionModel testingHigh dimensional
The invention provides a speaker recognition method based on a multi-coordinate sequence kernel, comprising a training stage and a recognition stage. The method comprises the following steps: in the training stage, preprocessing training voice; extracting a characteristic vector sequence from the preprocessed training voice; selecting an origin of a multi-coordinate system in a characteristic vector space, and mapping the characteristic vector sequence in each coordinate system; selecting an algorithm according to the coordinate system and splicing the vector sequence of each coordinate systeminto a super-vector; determining a super-vector space and a kernel function of a support vector machine (SVM), and training with the SVM algorithm to obtain a trained speaker model; and in the recognition stage, testing the super-vector by the trained model and outputting a decision mark. In the invention, by effective modeling on the voice signal characteristic sequence, the speaker recognitionmethod helps utilize the information contained in high dimensional statistics, reduce computational complexity of an integrated circuit, and improve speaker recognition accuracy and recognition speed.
Owner:TSINGHUA UNIV
Weighted hyper-sphere support vector machine algorithm based image classification method
InactiveCN104112143AHigh speedSmall amount of calculationCharacter and pattern recognitionSamplesortAlgorithm
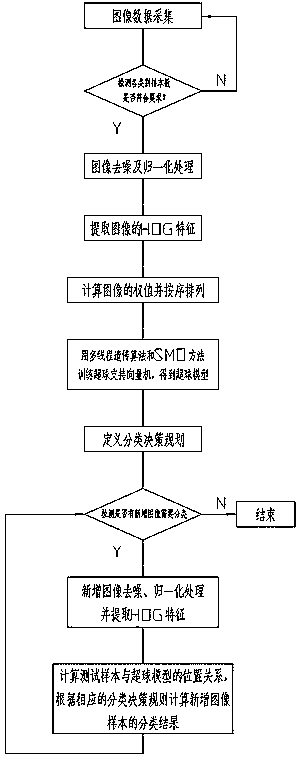
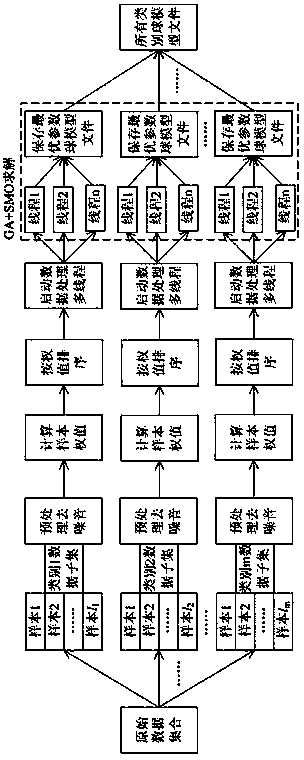
The invention discloses a weighted hyper-sphere support vector machine algorithm based image classification method which can improve the calculation speed and the calculation accuracy. The weighted hyper-sphere support vector machine algorithm based image classification method comprises collecting image data; denoising and performing normalization processing on images, calculating characteristics of HOG (Histograms of Oriented Gradients) of the images, adding predefined categories into image categories and classifying the images; calculating a data center of every category, calculating the weight of every sample of the category of data according to the data center and ordering the training samples according to the weight; training a hyper-sphere support vector machine through a multithreading genetic algorithm and an SMO (Sequential Minimal Optimization) method and solving an optimal parameter and a corresponding hyper-sphere model; extracting HOG characteristics of the newly collected images, calculating position relationships between newly collected samples and the hyper-sphere model, obtaining label categories according to a distinguish rule and labelling categories of the newly collected images.
Owner:DALIAN NATIONALITIES UNIVERSITY
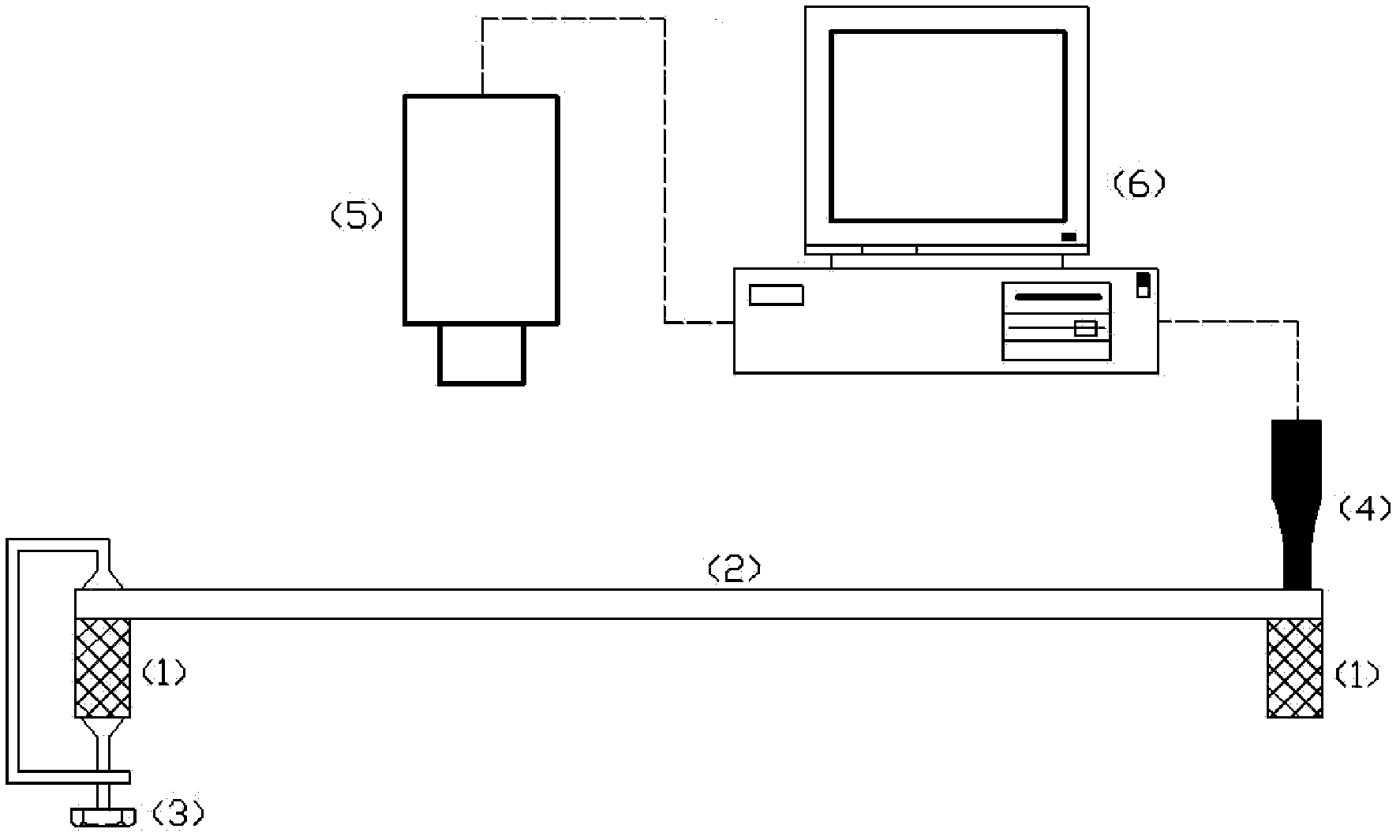
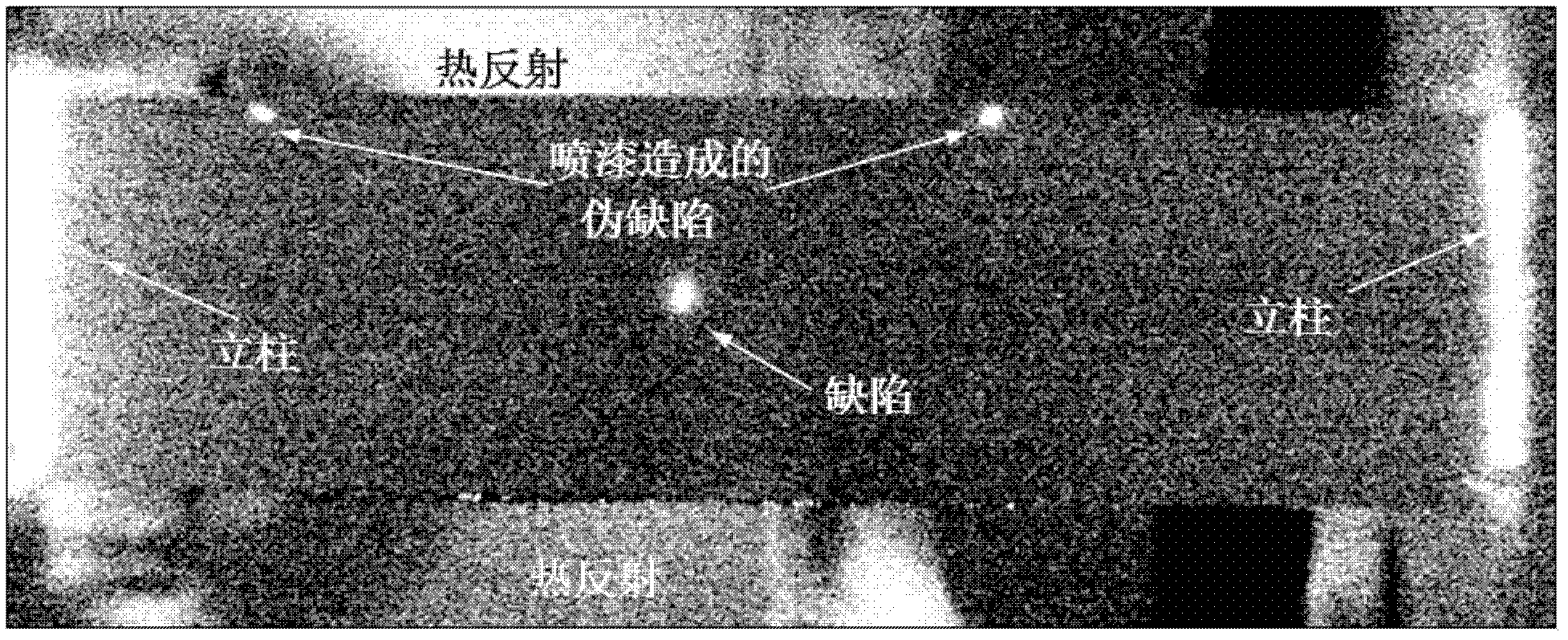
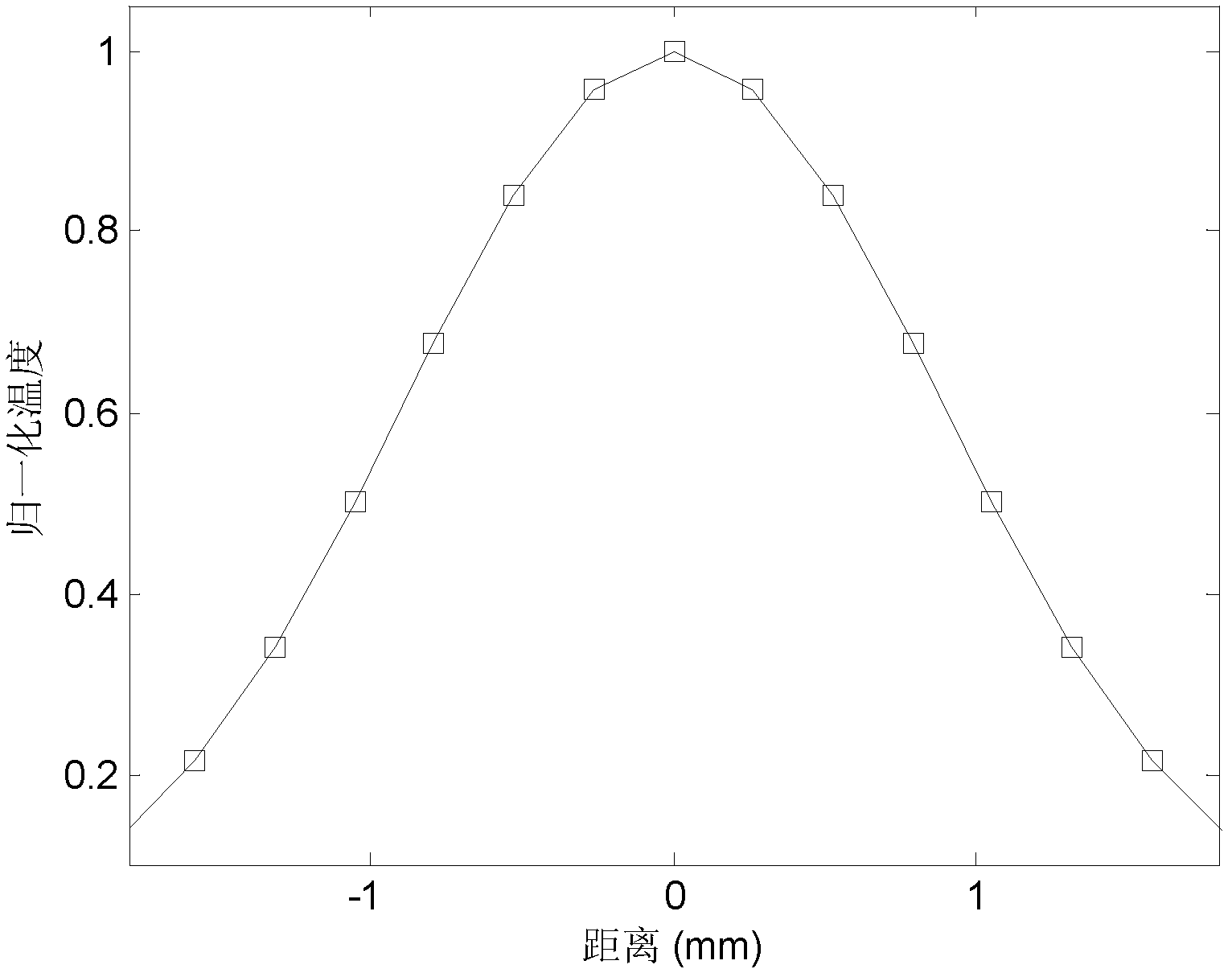
Automatic identification method of thermography sequence defect signals in ultrasonic infrared nondestructive test
ActiveCN102628796ARealize automatic identificationMaterial flaws investigationColor/spectral properties measurementsDiffusionSonification
The invention discloses an automatic identification method of thermography sequence defect signals in an ultrasonic infrared nondestructive test. The automatic identification method is characterized in that an ultrasonic source is applied to a piece needing to be tested under conditions of certain frequency and pulse time and then heat is generated at defects due to friction or thermoelastic effects so that the change of a thermal field of a corresponding surface is caused; the change of the thermal field is recorded by a thermal imager and characteristic values of two-dimensional thermal diffusion are extracted; and through combination of image processing and a support vector machine algorithm, the automatic identification of thermography sequence defect signals in an ultrasonic infrared nondestructive test is realized effectively.
Owner:CAPITAL NORMAL UNIVERSITY +2
Self-adaptive trojan communication behavior detection method on basis of dynamic feedback
ActiveCN103532949AEliminate redundancyReduce false positive informationTransmissionRelevant informationSimilarity analysis
The invention discloses a self-adaptive trojan communication behavior detection method on the basis of dynamic feedback, which comprises the steps of processing trojan detection alarm information, constructing a sample set for dynamic feedback learning by utilizing the alarm information, and determining updating opportunity of detection by detecting concept drift of a data stream, wherein the step of processing the trojan detection alarm information comprises the sub-steps of carrying out merging and association processing on the alarm information which is subjected to standard description, then establishing an intrusion track event and storing the intrusion track event into an intrusion event table. According to the invention, aiming at the problem of self-adaption of information stealing trojan detection, the information stealing trojan detection alarm information is analyzed, methods of similarity analysis, clustering analysis and the like are combined, related information of a target IP (Internet Protocol) is acquired additionally by driving detection, the sample set for dynamic feedback learning is constructed by the alarm information, an increment support vector machine algorithm is used as an algorithm for dynamic feedback learning, and the updating opportunity of a detection system is determined by detecting the concept drift of the data stream.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
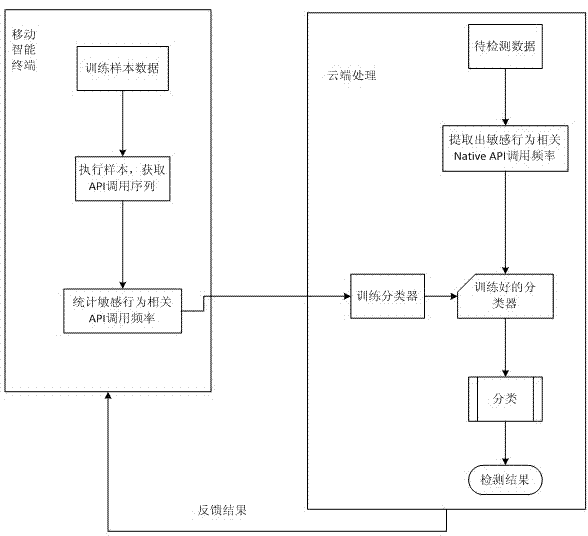
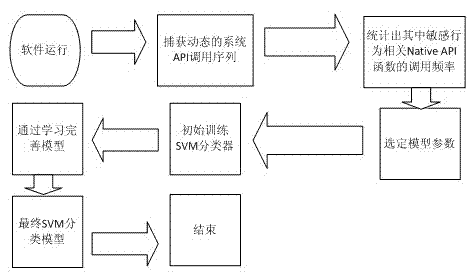
Dynamic behavior analysis method for mobile intelligent terminal software based on support vector machine algorithm
InactiveCN104751052AEfficient detectionPlatform integrity maintainanceSupport vector machine algorithmNetwork behavior
The invention discloses a dynamic behavior analysis method for mobile intelligent terminal software based on a support vector machine (SVM) algorithm. The method comprises the steps: the first step, capturing application program interface (API) function called in the software running by the terminal execution software; the second step, analyzing the NativeAPI calling sequence related to five sensitive behaviors, wherein five sensitive behaviors are the privilege behavior, progress behavior, document behavior, network behavior and terminal memory operation behavior, and calculating the calling frequency of the NativeAPI function related to five sensitive behaviors; the third step, using the calling frequency as the dynamic behavior characteristic of the software, sending to the cloud end, modeling by using the SVM algorithm and training the classifier, and finally detecting the malignant software behavior by using the trained classifier. The method uses the dynamic detection technology and cannot be affected by the deformation and packing encryption technology, and the method is capable of analyzing and detecting the self-modifying program, making up the lack that the static behavior cannot detect the variety behavior, and effectively detecting the vicious software behavior.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
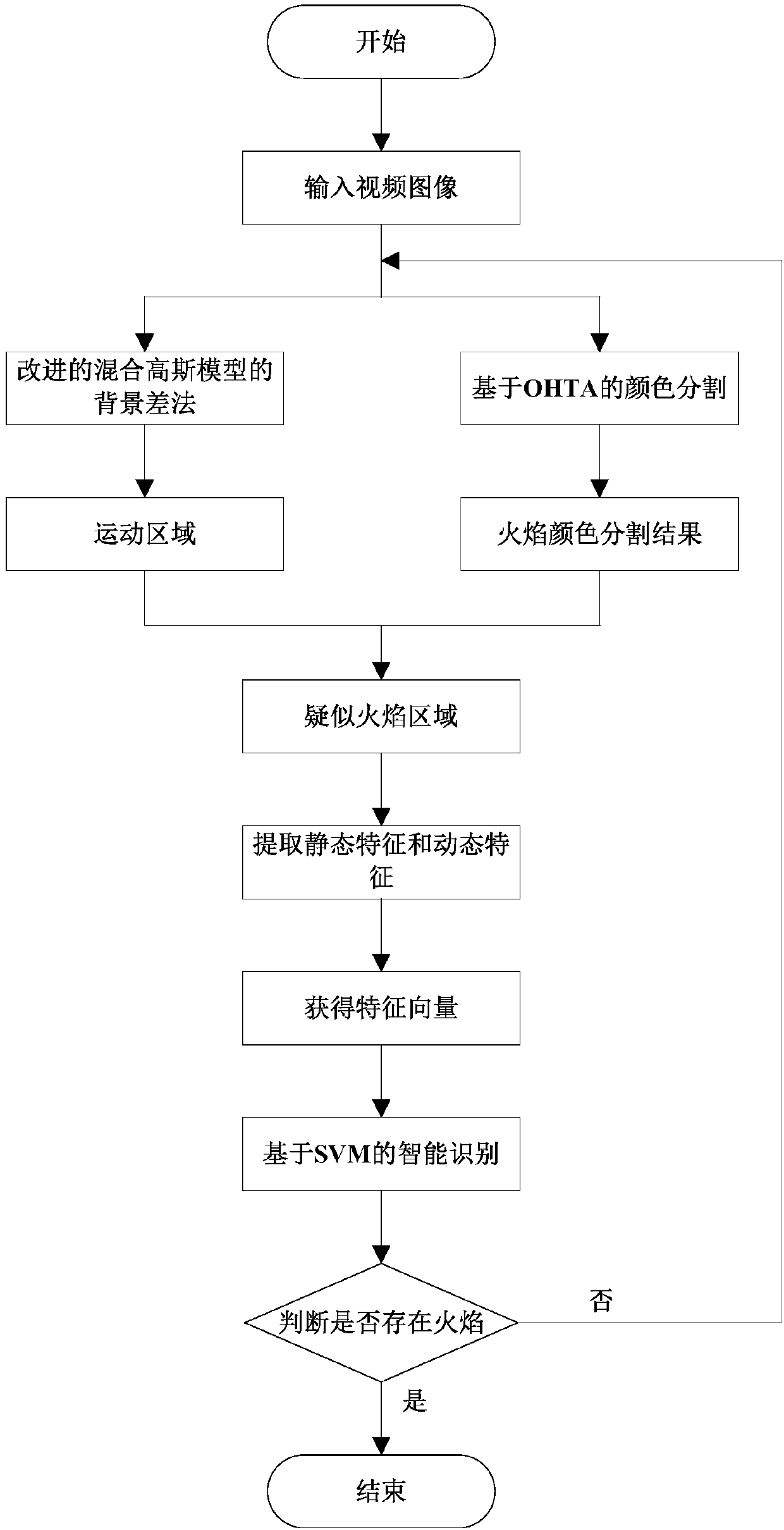
Motion detection and multi-feature extraction-based flame intelligent-recognition method
InactiveCN108229458APrecision motion zoneImprove flame recognition rateCharacter and pattern recognitionFire alarm radiation actuationFeature extractionVisual perception
The invention discloses a motion detection and multi-feature extraction-based flame intelligent-recognition method, which relates to the field of computer vision. According to the method, firstly, animproved mixed Gaussian model is utilized for motion region extraction, then OHTA-based color segmentation is combined for color segmentation for obtaining a suspected flame region; then flame static-features and dynamic-features are extracted; and finally, a support vector machine-based algorithm is used for flame recognition. According to the method, the suspected flame region with a high accuracy degree is extracted, interference of flame-similar objects is largely eliminated, and the various flame distinctive-features are fused. The algorithm has robustness, anti-interference performance and adaptability, and is high in a recognition rate on flame at the same time.
Owner:HUNAN VISION SPLEND PHOTOELECTRIC TECH
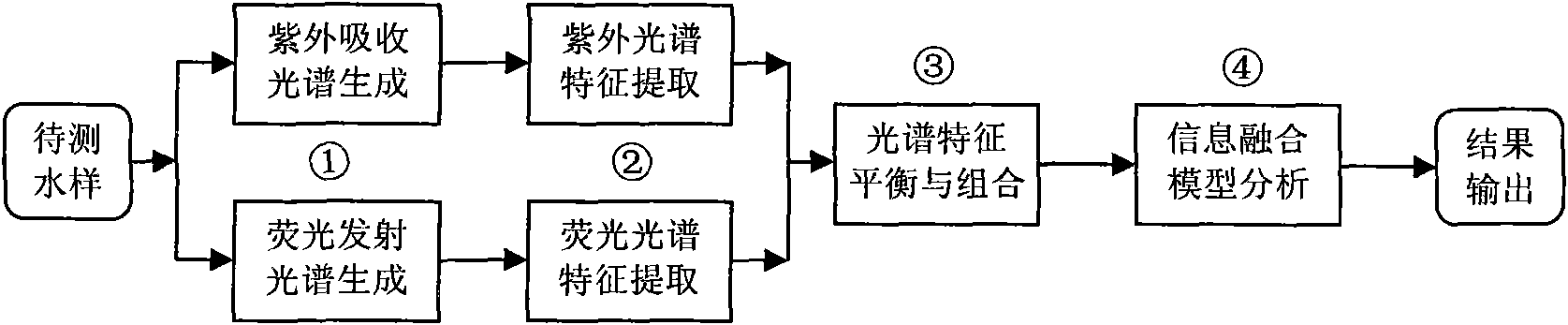
Analytical method of multi-source spectrum fusion water quality
InactiveCN101576485AImprove analysis accuracyMeet the needs of on-site rapid analysisColor/spectral properties measurementsFluorescence/phosphorescencePretreatment methodData set
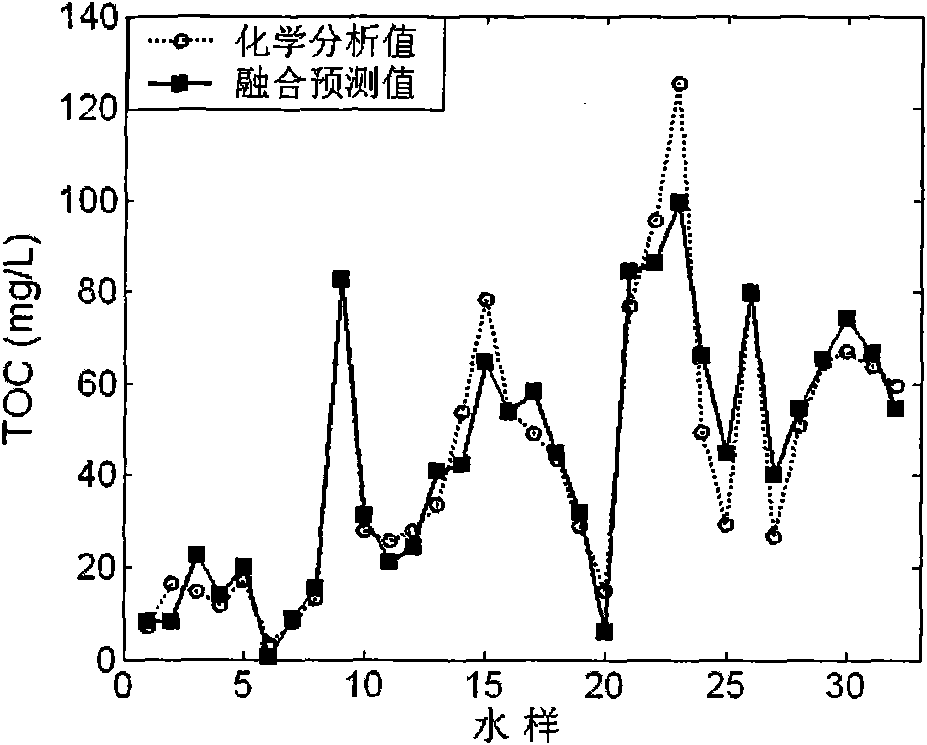
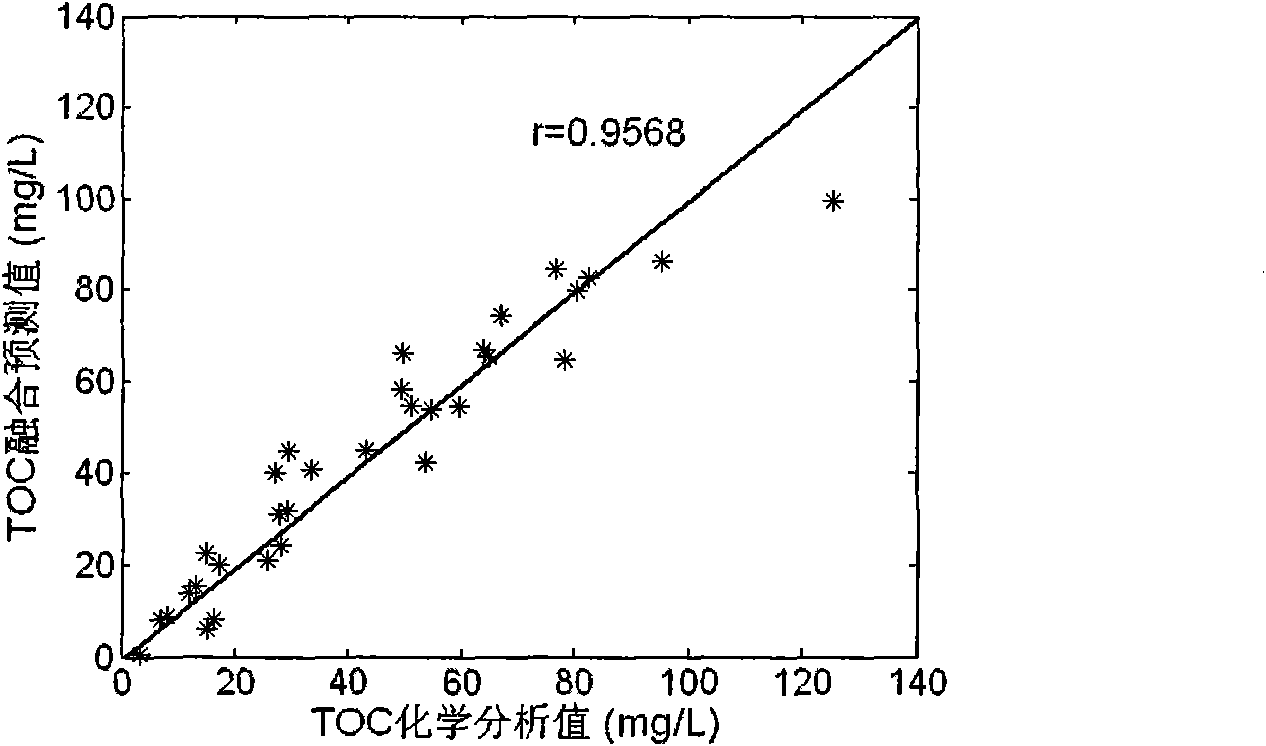
The invention discloses an analytical method of multi-source spectrum fusion water quality. The method takes an ultraviolet / visible absorption spectrum signal and a multi-dimensional fluorescence emission spectrum signal of a water sample to be tested as input, and respectively adopts independent component pretreatment method to extract characteristic signals, remove interference information and obtain characteristic signals of the spectrums. According to the contribution of the characteristic signals of the spectrums to a water quality analyzing model, and aiming at avoiding information hiding, the combined characteristic signal number of the two types of spectrums is determined, the characteristic signals are combined into a spectrum characteristic signal federated data set, and the optimal spectrum configuration combination is solved. Based on an improved support vector machine algorithm, a Boosting method is adopted for modeling, and the optimal spectrum fusion water quality analyzing model is obtained by combining a plurality of modeling results. Based on the spectrum characteristic signal federated data set, the computation model is adopted to compute the comprehensive organic substance pollution index value of the water sample to be tested. The method has the remarkable advantages of high analyzing accuracy, high analysis speed, no pollution of chemical agent, simple operation and maintenance and the like.
Owner:ZHEJIANG UNIV
Method for rapidly detecting hogwash oil by synchronous fluorescence spectrum
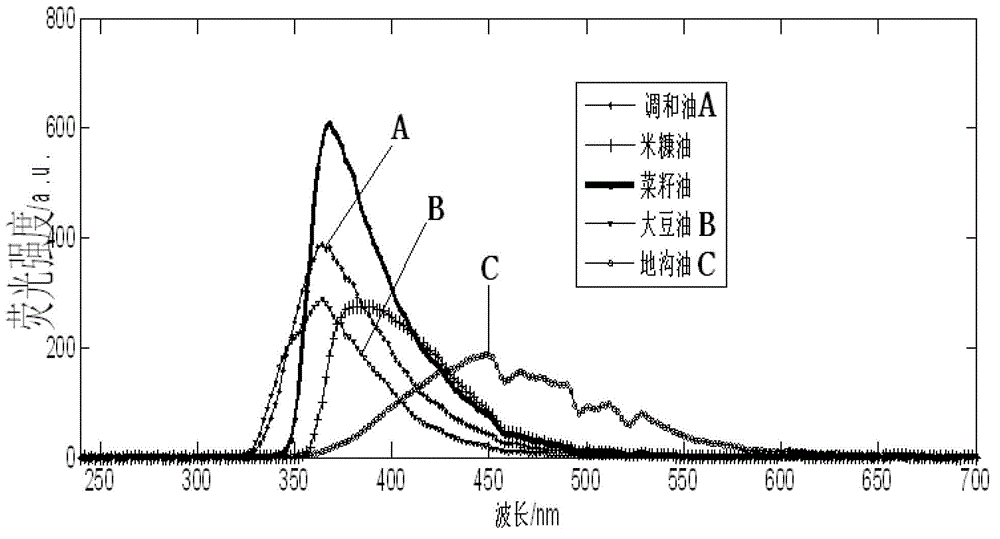
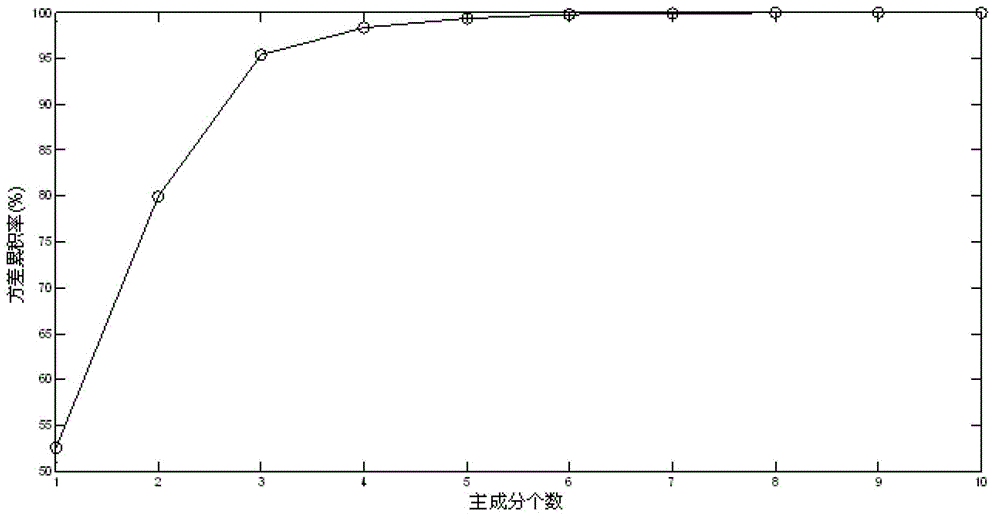
InactiveCN102749315AThe result is accurateGood reproducibilityFluorescence/phosphorescenceFluorescenceSynchronous fluorescence
The invention relates to a method for rapidly detecting hogwash oil by synchronous fluorescence spectrum. The method is characterized by comprising the following steps of: preparing a sample; acquiring the synchronous fluorescence spectrum; establishing a model; and judging the unknown sample. Compared with the prior art, the method for rapidly detecting the hogwash oil by the synchronous fluorescence spectrum is based on a support vector machine algorithm, adopts the synchronous fluorescence spectrum technology, and establishes the judgment model judge the hogwash oil without pretreatment of the sample; no other chemical reagents are consumed during testing, the testing time is only 2-3 minutes, and the testing result is accurate and has good repeatability.
Owner:CHUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com