Dynamic behavior analysis method for mobile intelligent terminal software based on support vector machine algorithm
A mobile intelligent terminal and behavior analysis technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as large impact, and achieve efficient detection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
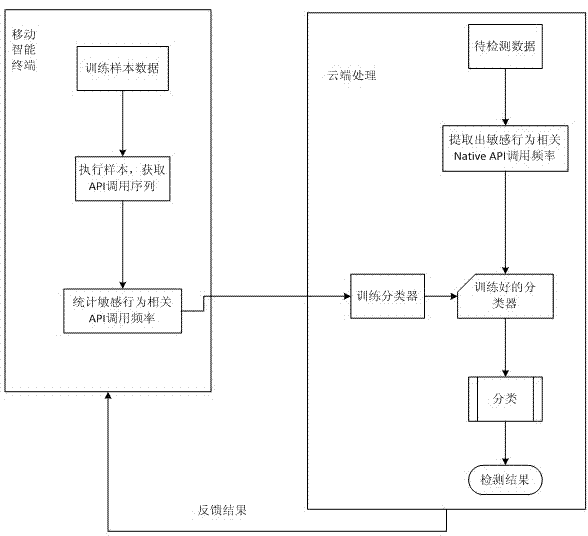
[0018] combine figure 1 , the present invention relates to a dynamic behavior analysis method of mobile intelligent terminal software based on SVM algorithm, the steps are as follows:
[0019] In the first step, the terminal executes the software, and captures the API functions called when the software is running.
[0020] The second step is to analyze the Native API call sequence related to 5 sensitive behaviors. The 5 sensitive behaviors are privileged behavior, process behavior, file behavior, network behavior and terminal memory operation behavior, and count the Native API functions related to these 5 sensitive behaviors. frequency of calls.
[0021] The third step is to use the call frequency as the dynamic behavior feature of the software, send it to the cloud to use the SVM algorithm to model and train the classifier, and finally use the learned classifier to detect malicious software behavior.
Embodiment 2
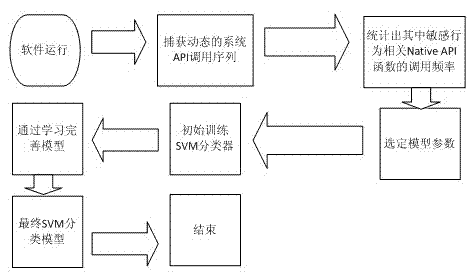
[0023] combine figure 2 , a dynamic behavior analysis method for mobile intelligent terminal software based on the SVM algorithm, the steps are as follows:
[0024] The first step is to run the sample software, use HOOK API technology to capture the system API function call sequence of the software, and count the call frequency of 5 sensitive behavior-related Native API functions. These five sensitive behaviors are privileged behavior, process behavior, file behavior, network behavior and terminal memory operation behavior.
[0025] 1. Find out the entry addresses corresponding to the system calls of the five sensitive behaviors in the system.
[0026] 2. Use HOOK technology to intercept system calls through the entry address, and capture the respective API call sequences. The key code is as follows:
[0027] size_t hook_sysread(int fd, ehar*buf, size_t count)
[0028] {
[0029] / / Add statistics function
[0030] return orig_read(fd,buf,count);
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com