Self-adaptive trojan communication behavior detection method on basis of dynamic feedback
A dynamic feedback and detection method technology, applied in electrical components, transmission systems, etc., can solve the problems of high concealment Trojan horse failure, short analysis time, detection method does not have self-adaptive ability, etc., to achieve self-adaptive mechanism, The effect of removing redundancy and facilitating misreporting of information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
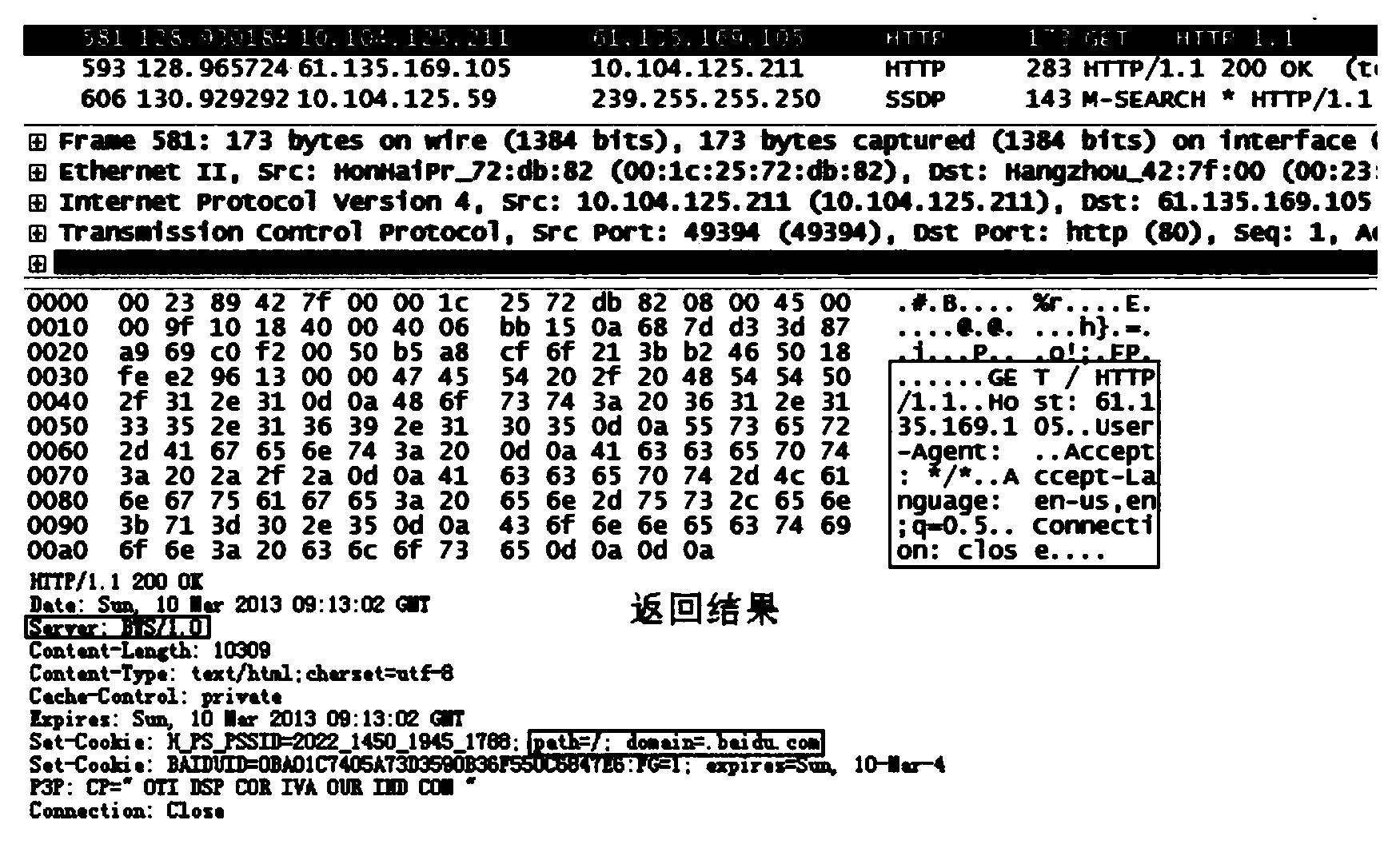
[0041] Embodiment 1: a kind of adaptive Trojan horse communication behavior detection method based on dynamic feedback, at first, the warning information of detection is described through standardization, is stored in the original warning table of database; Utilizes the convenience of database, the warning information is merged, Correlation, storing the processed alarm information, and on this basis, different types of associated alarm information are established as attack track events and stored in the attack event table. The processed alarm information can effectively remove redundancy and facilitate the reduction of false alarm information. The logical structure diagram of the fusion processing of alarm information is attached figure 1 .
[0042] There are the following definitions:
[0043] Definition 1: (F,D V ) is called the Trojan horse communication data flow detection model.
[0044] Definition 2: The feature set F of network communication behavior is represented ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com