Write-in method of key/value database memory log
A database and memory technology, applied in the direction of electrical digital data processing, special data processing applications, instruments, etc., can solve problems such as loss, achieve the effect of improving concurrency, rationally utilizing hardware resources, and reducing random IO
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
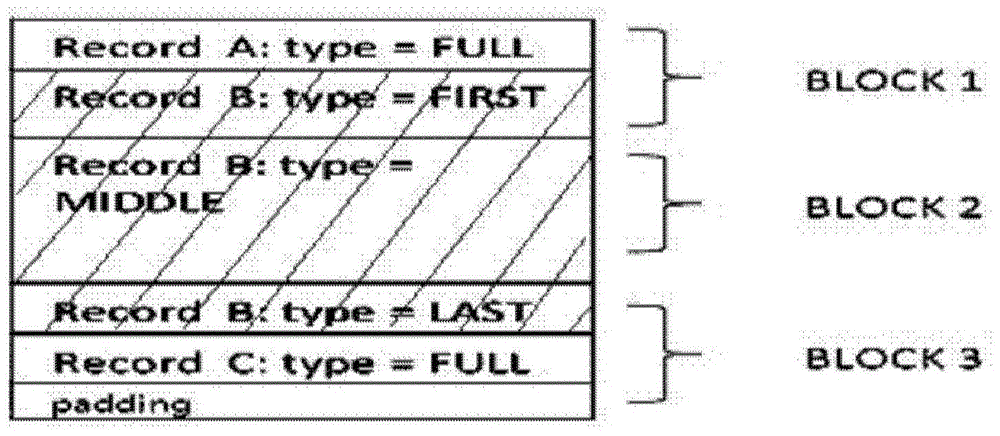
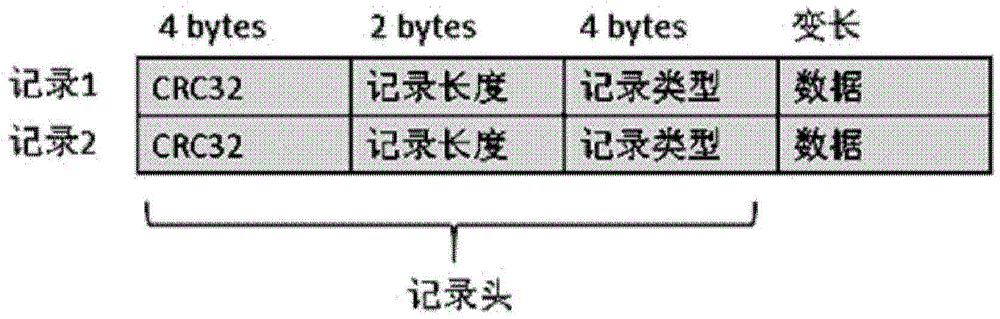
[0023] The main function of the log file (Log file) in the system is to prevent data loss when the system crashes and recovers. Since all write operations in the prior art need to be written to the log first, the writing of the log has become the performance of the entire system. where the bottleneck is.
[0024] In order to improve the writing speed of the log file, the present invention attempts to decompose the operation of writing into the log file into multiple files written at the same time through the Hash algorithm, but in actual use, it is found that the writing efficiency of the database does not improve, but greatly reduce. The analysis shows that after the log file is hashed, it will be written into different...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com