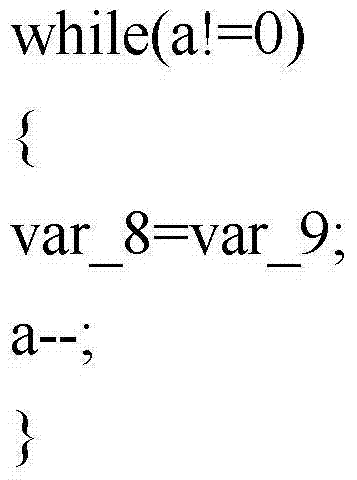Method and device for detecting loophole of source code
A detection device and detection source technology, applied in the computer field, can solve problems such as analysis and high false alarm rate, and achieve the effects of improving comprehensiveness, reducing false alarm rate, and improving integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be described in further detail below with reference to the accompanying drawings.
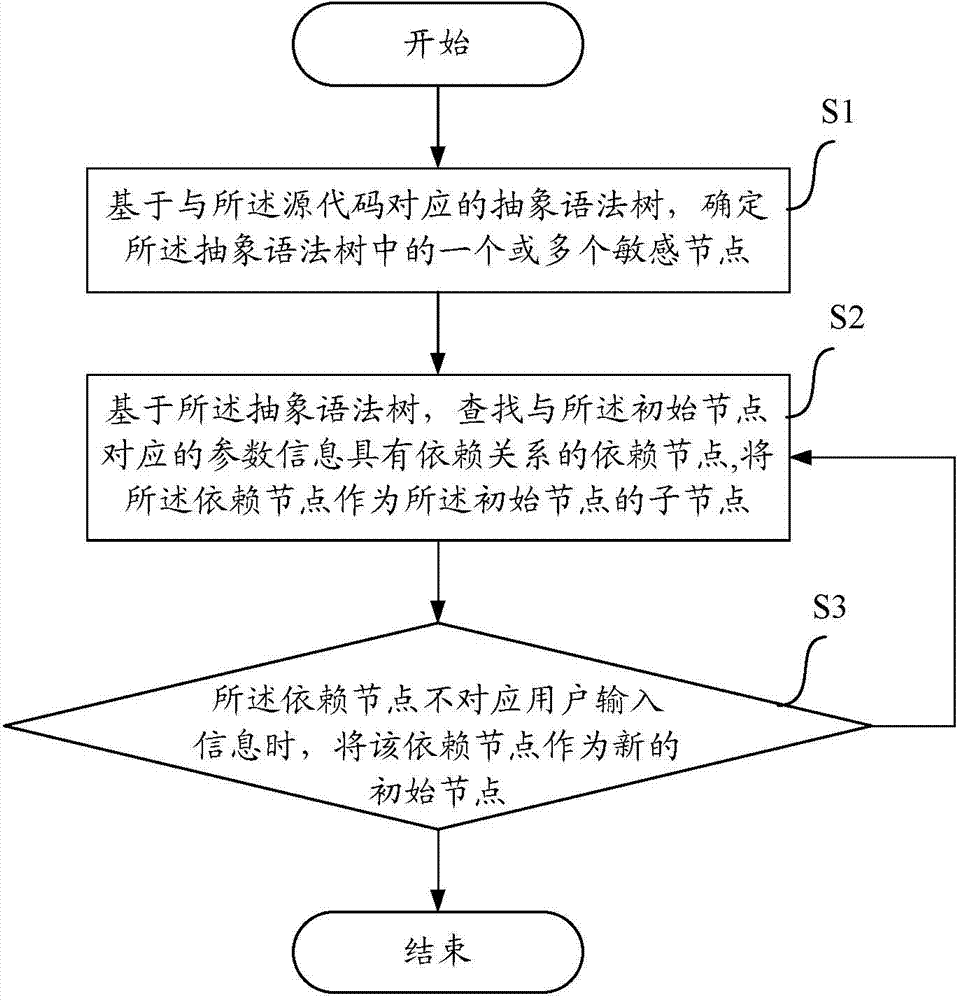
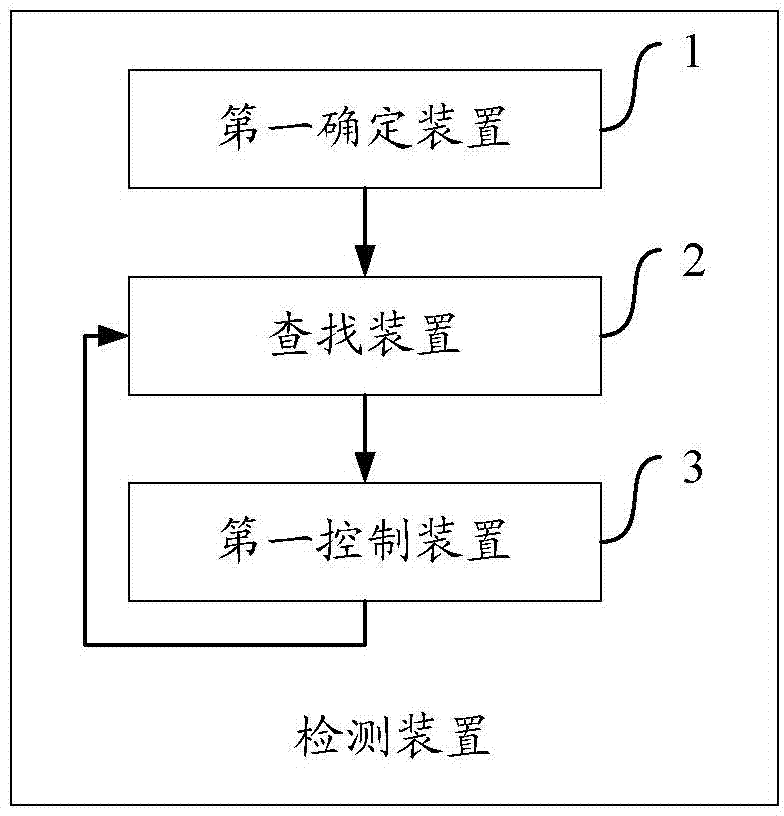
[0022] figure 1 A flow chart of a method for detecting source code vulnerabilities according to the present invention is illustrated. The method according to the present invention comprises step S1, step S2 and step S3.
[0023] Therein, the method according to the present invention is implemented by means of a detection device included in a computer device. Preferably, the source code is a website source code.
[0024] The computer equipment includes an electronic device that can automatically perform numerical calculation and / or information processing according to pre-set or stored instructions, and its hardware includes but is not limited to microprocessors, application-specific integrated circuits (ASICs), programmable gates Arrays (FPGA), digital processors (DSP), embedded devices, etc.
[0025] Wherein, the computer equipment includes network equipmen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com