Malicious Code Integrity Analysis Method Based on Environment Reconstruction
A malicious code and analysis method technology, applied in the field of malicious code integrity analysis based on environment reconstruction, can solve problems such as low analysis efficiency, path explosion, memory leak, etc., to improve analysis efficiency, reasonably trigger, and reduce time overhead. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
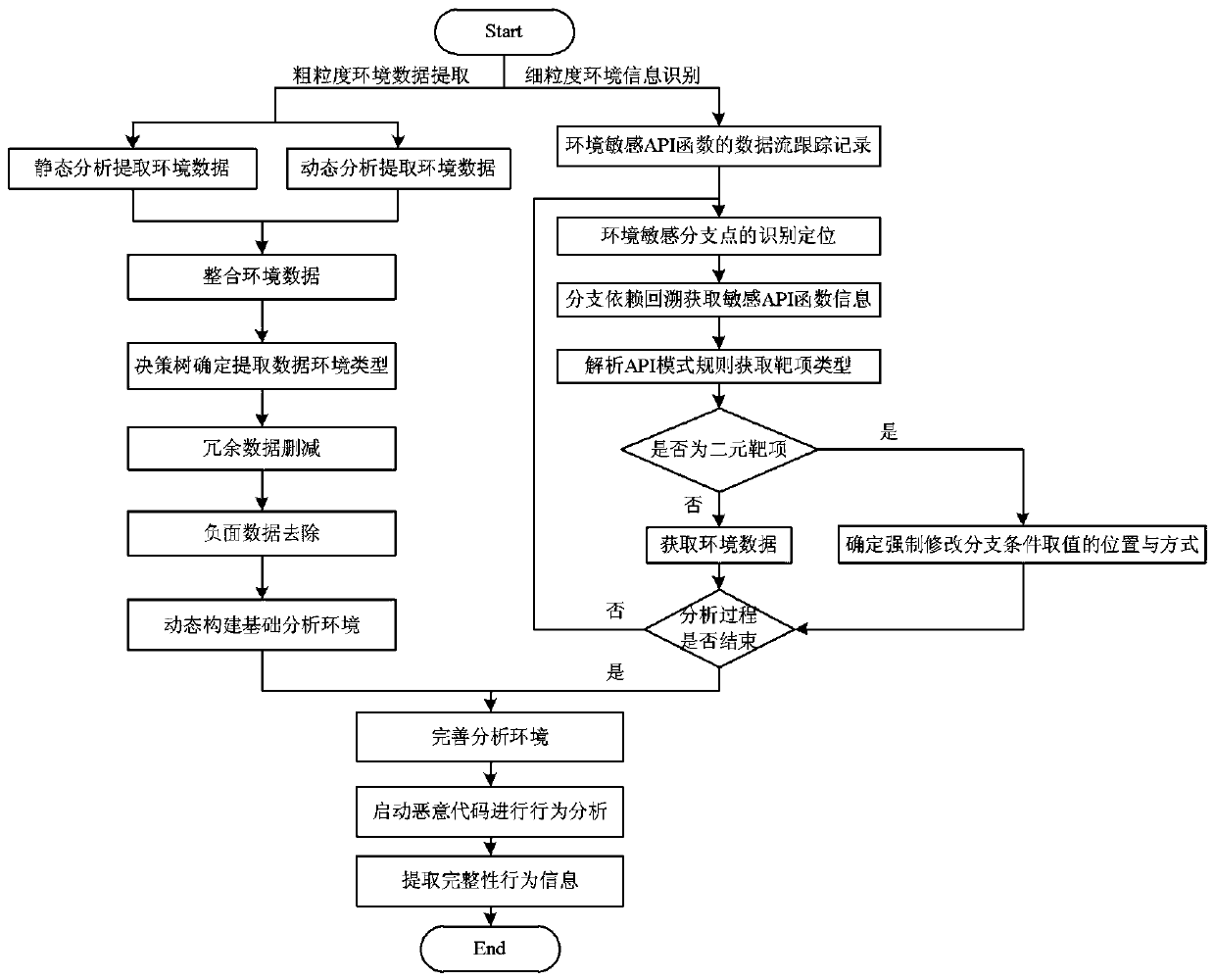
[0036] Embodiment: The present invention proposes a malicious code integrity analysis method based on environment reconstruction. The analysis idea is: use the dynamic binary analysis platform Pin and the decompilation tool IDA to obtain the environment information that is perceived and sought during the execution of the malicious code, and use the Based on the obtained environmental information, the optimal execution environment for malicious code is constructed, and finally the malicious code is put into the dynamically constructed environment to run to achieve integrity analysis. Under the guidance of the above general idea, the analysis process is as follows figure 1 shown.
[0037]In the process of analyzing the integrity of the malicious code, the present invention adopts the combination of coarse-grained environment data extraction and fine-grained sensitive environment identification to jointly determine the execution environment required for triggering the hidden beh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com