PIN code protection method under Android platform
A PIN code and platform technology, applied in the field of information security, can solve problems such as easy interception of PIN codes, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
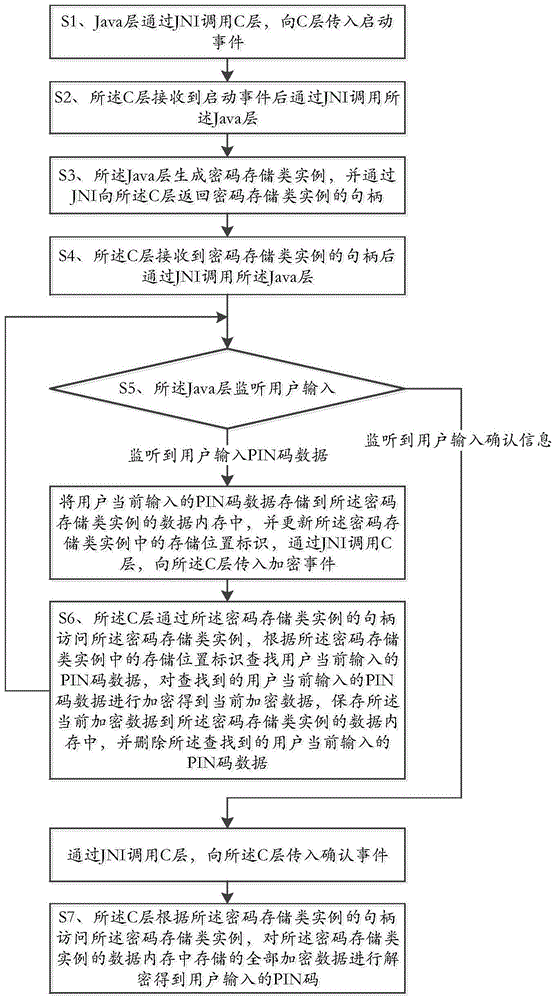
[0038] Embodiment 1 of the present invention provides a PIN code protection method under the Android platform, such as figure 1 As shown, the method specifically includes:
[0039] Step S1, the Java layer calls the C layer through JNI, and transfers the start event to the C layer;
[0040] Step S2, the C layer invokes the Java layer through JNI after receiving the startup event;
[0041] Step S3, the Java layer generates a password storage class instance, and returns the handle of the password storage class instance to the C layer through JNI;
[0042] Step S4, the C layer calls the Java layer through JNI after receiving the handle of the password storage class instance;
[0043] Step S5, the Java layer monitors the user input, if the user input PIN code data is monitored, the PIN code data currently input by the user is stored in the data memory of the password storage class instance, and the password storage class instance is updated storage location identifier, call the ...
Embodiment 2
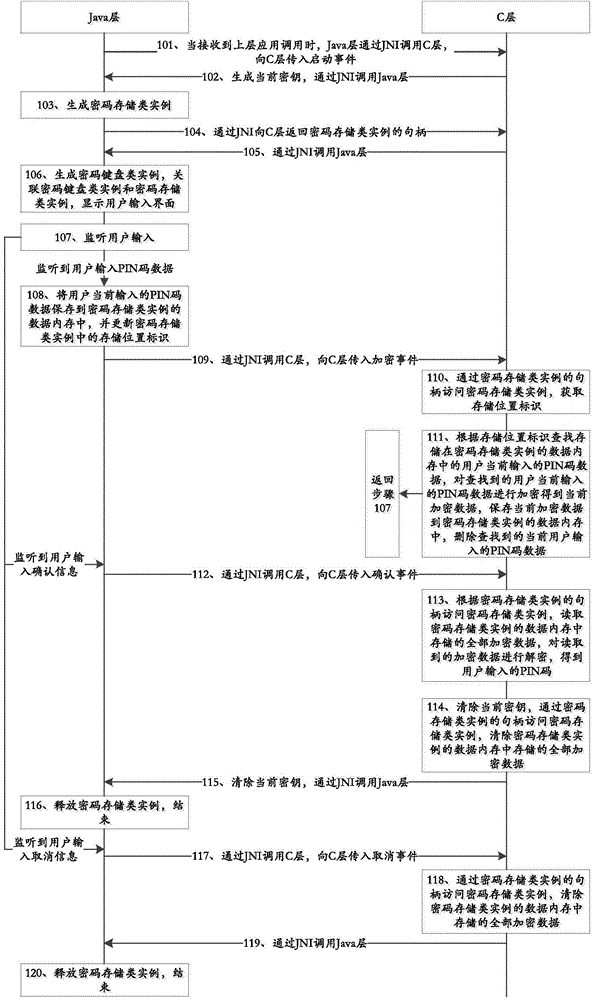
[0052] Embodiment 2 of the present invention provides a PIN code protection method under the Android platform, such as figure 2 As shown, the method specifically includes:
[0053] Step 101, when receiving the upper-layer application call, the Java layer calls the C layer through JNI, and transfers the startup event to the C layer;
[0054] JNI (Java Native Interface, Java native programming interface), which enables Java code running inside the Java virtual machine to interoperate with applications and libraries written in other programming languages such as C, C++, and assembly language.
[0055] Specifically, the event data passed from the Java layer to the C layer can be the corresponding event data passed from the Java layer to the C layer. Layer C can work according to this agreement;
[0056] For example, each event involved in this embodiment is a series of jint type data predefined by the Java layer and the C layer, wherein the start event is defined as the int...
Embodiment 3
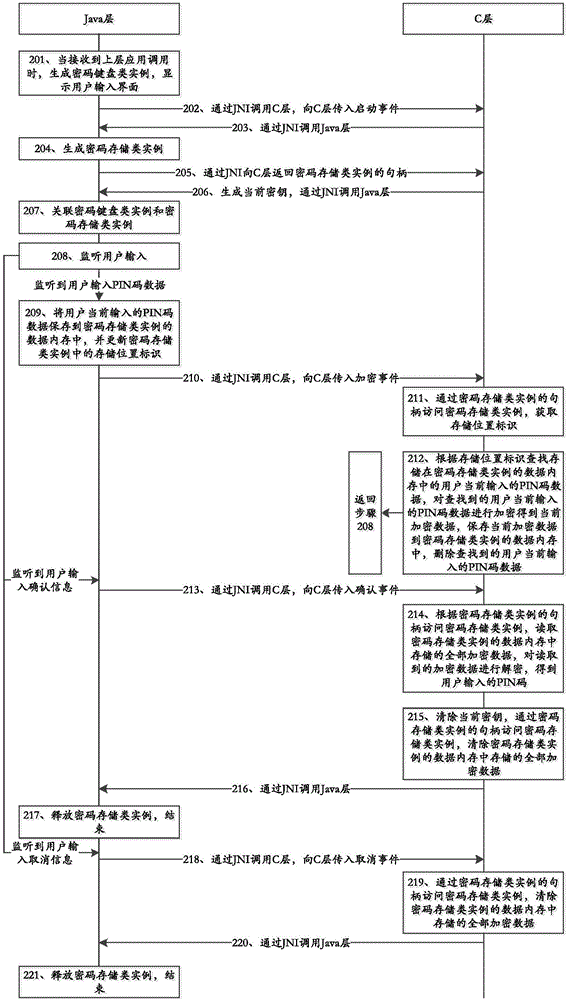
[0095] This embodiment three provides a PIN code protection method under the Android platform, such as image 3 As shown, the method specifically includes:
[0096] Step 201, when receiving an upper-layer application call, the Java layer generates a password keyboard class instance, and displays a user input interface;
[0097] In this embodiment, specifically, the Java layer generates an instance of a password keyboard class by calling an initialization function in the password storage class;
[0098] In this embodiment, the Java layer can display the user input interface by calling the display function in the password keyboard class instance. The input interface usually includes an input box and a keyboard. It is implemented by three parties. When the input box and keyboard are implemented by the system or by a third party, the display function of the password keyboard class instance displays the input interface by calling the display interface of these implementations.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com