Code virtualization software protection system realizing instruction set randomization
A virtualization software and protection system technology, applied in the field of computer software security, can solve problems such as code confusion, poor protection effect, easy to be found and removed, etc., to increase complexity, prolong analysis time, and enhance anti-reverse analysis capabilities Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
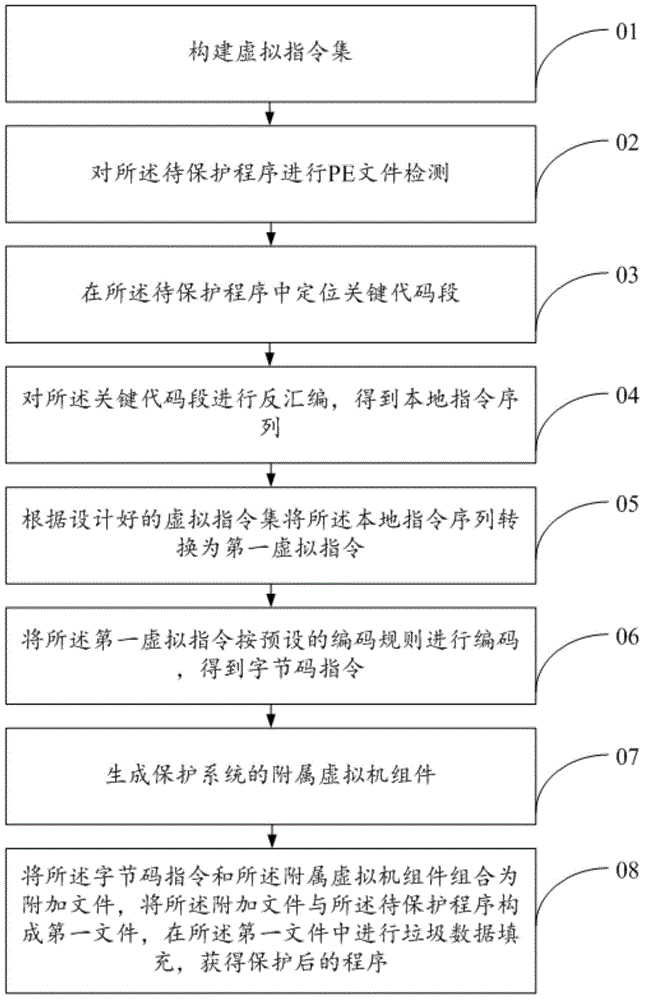
[0041] The present invention provides a code virtualization software protection system with instruction set randomization, said code virtualization software protection system with instruction set randomization, such as figure 1 shown, including:
[0042] 01. Build a virtual instruction set.
[0043] 02. Perform PE file detection on the program to be protected.
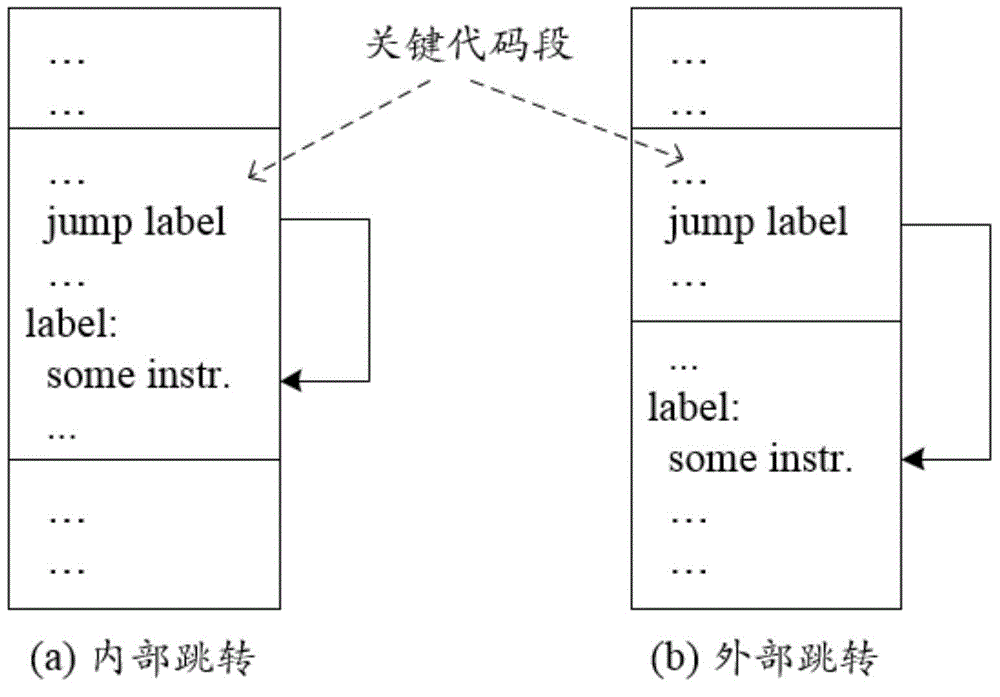
[0044] 03. Locate the key code segment in the program to be protected.
[0045] 04. Disassembling the key code segment to obtain a local instruction sequence.
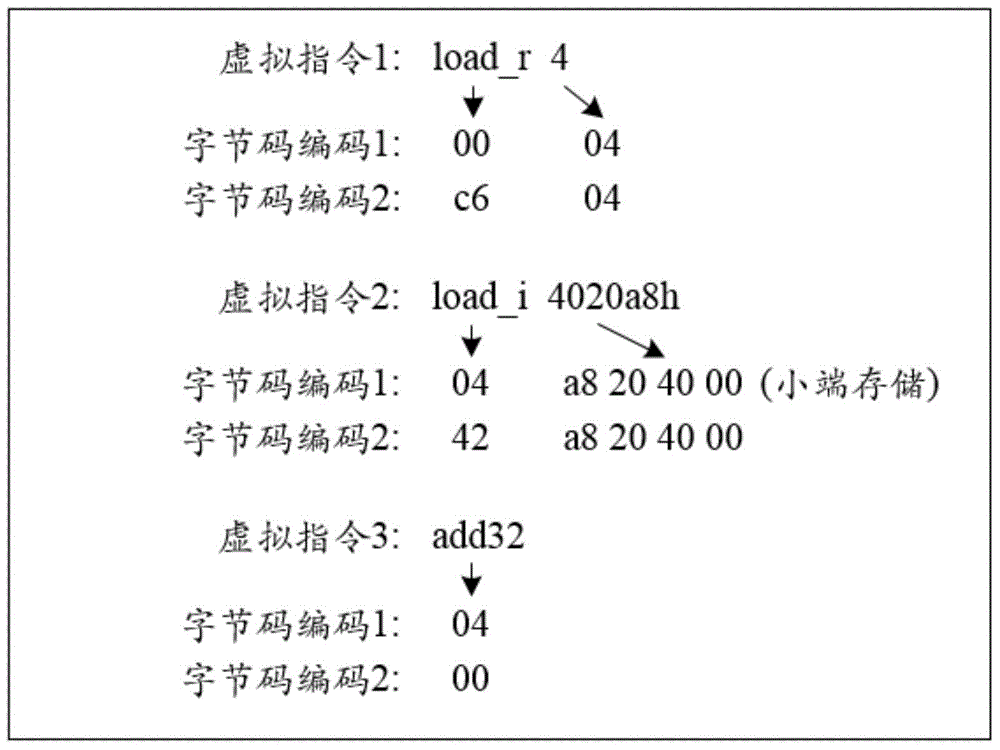
[0046] 05. Convert the native instruction sequence into a first virtual instruction according to the designed virtual instruction set.
[0047] 06. Encode the first virtual instruction according to a preset encoding rule to obtain a bytecode instruction.
[0048] 07. Generate the auxiliary virtual machine components of the protection system.
[0049] 08. Combine the bytecode instruction and the attached virtual machine component into an additional file, fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com