Postprocessing method for quantum key distribution
A quantum key distribution and key technology, applied in the field of Internet communication, can solve problems such as security risks, achieve the effect of improving correctness and security, and ensuring absolute security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Embodiments of the present invention are described in detail below, examples of which are shown in the drawings, wherein the same or similar reference numerals designate the same or similar elements or elements having the same or similar functions throughout. The embodiments described below by referring to the figures are exemplary only for explaining the present invention and should not be construed as limiting the present invention.
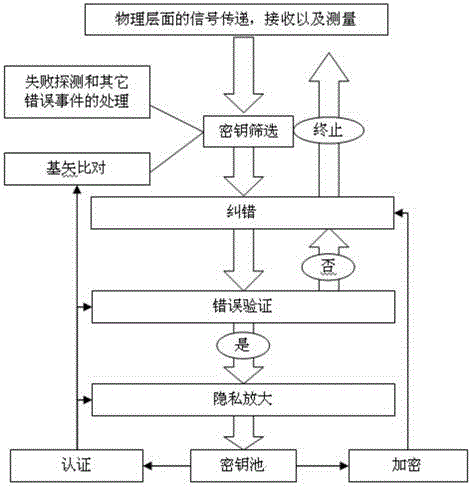
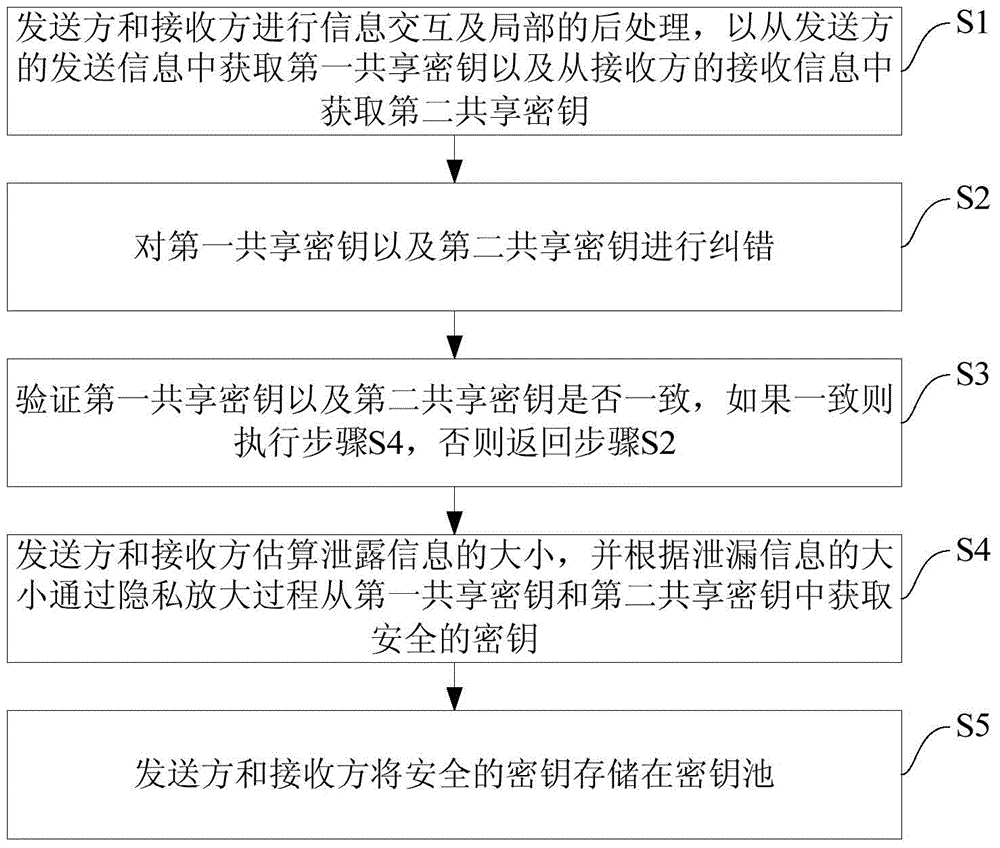
[0025] The post-processing method of quantum key distribution according to the embodiment of the present invention will be described below with reference to the accompanying drawings.
[0026] Specifically, in the quantum key distribution protocol, after signal transmission, reception and measurement at the physical level, the sender and receiver will generate corresponding information. Since these information are not correspondingly equal, and there are information leaks and errors, post-processing is required to process these informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com