White-box cryptography system for confusing wheel boundary and method
A technology of white-box cipher and wheel boundary, applied in the information field, can solve the problem of difficult concealment of linear diffusion operation, and achieve the effect of increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
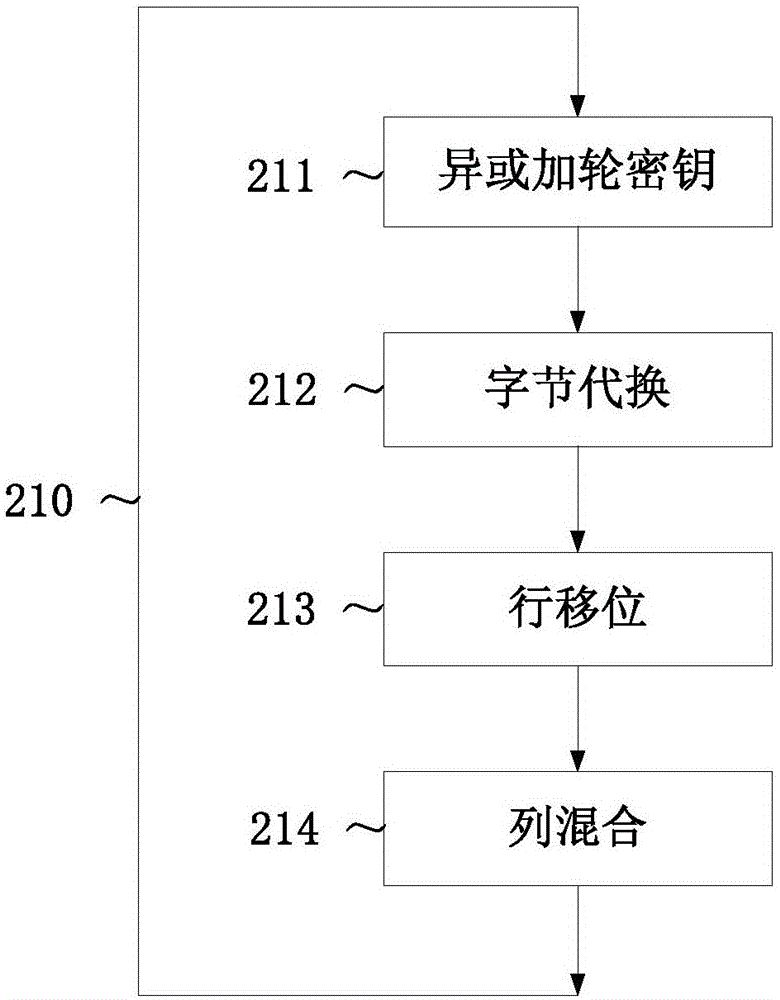
[0032] The specific implementation of the present invention will be described below by taking the block cipher AES128 (hereinafter referred to as AES) as an example. Of course, the present invention can also be applied to white-box implementations of other block ciphers, and even more generally to all white-box cryptosystems that need to obfuscate round boundaries.
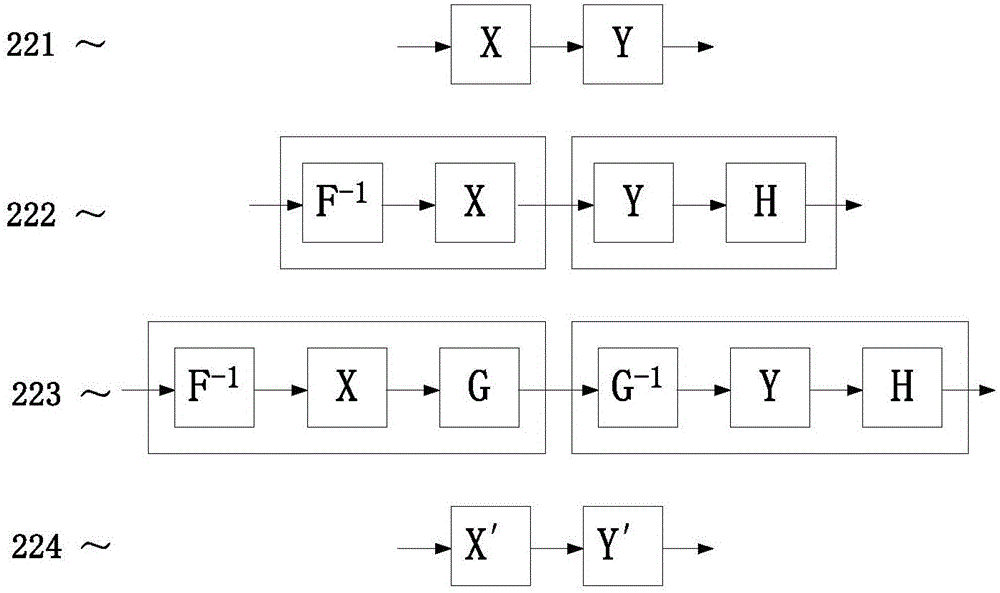
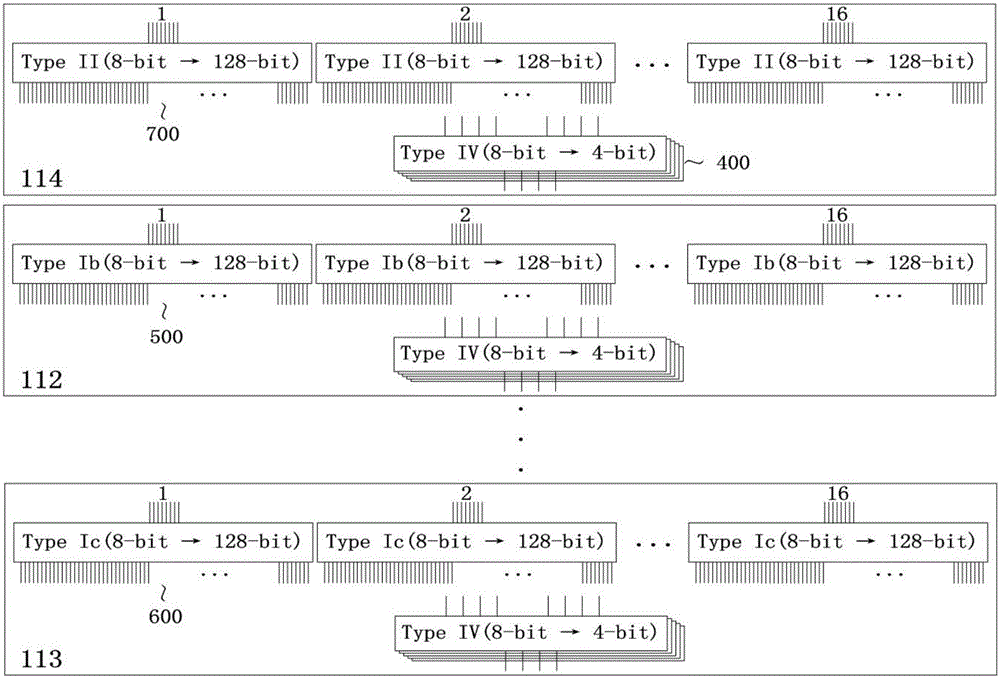
[0033] The summary process is as follows: First, we follow the "Chow1" method, use the lookup table to realize the basic operation of each round of AES, and hide the key in the lookup table. In order to achieve the purpose of confusing the round boundary in the next step, we will "Chow1" The lookup table is improved, and the row shift operation is also implemented in the lookup table; after implementing AES with a lookup table, we can divide these lookup tables into lookup table groups with similar structures, and randomly increase the number of mixed bijections (equivalent to randomly adding sets of obfuscated lo...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap