Image encryption method based on two-dimensional compression perception and chaotic system
An encryption method and chaotic system technology, applied in the field of information security, can solve problems such as poor anti-noise ability, fast reconstruction speed, low reconstruction accuracy, etc., and achieve good robustness, resistance to noise interference, and small key consumption Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described below in conjunction with the embodiments and drawings, but the protection scope of the present invention should not be limited thereby.
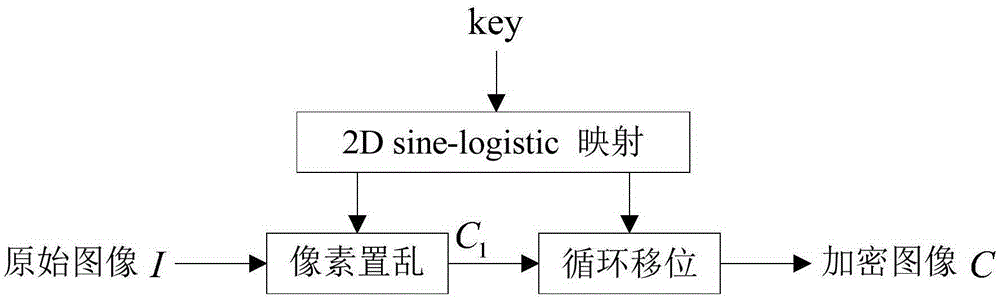
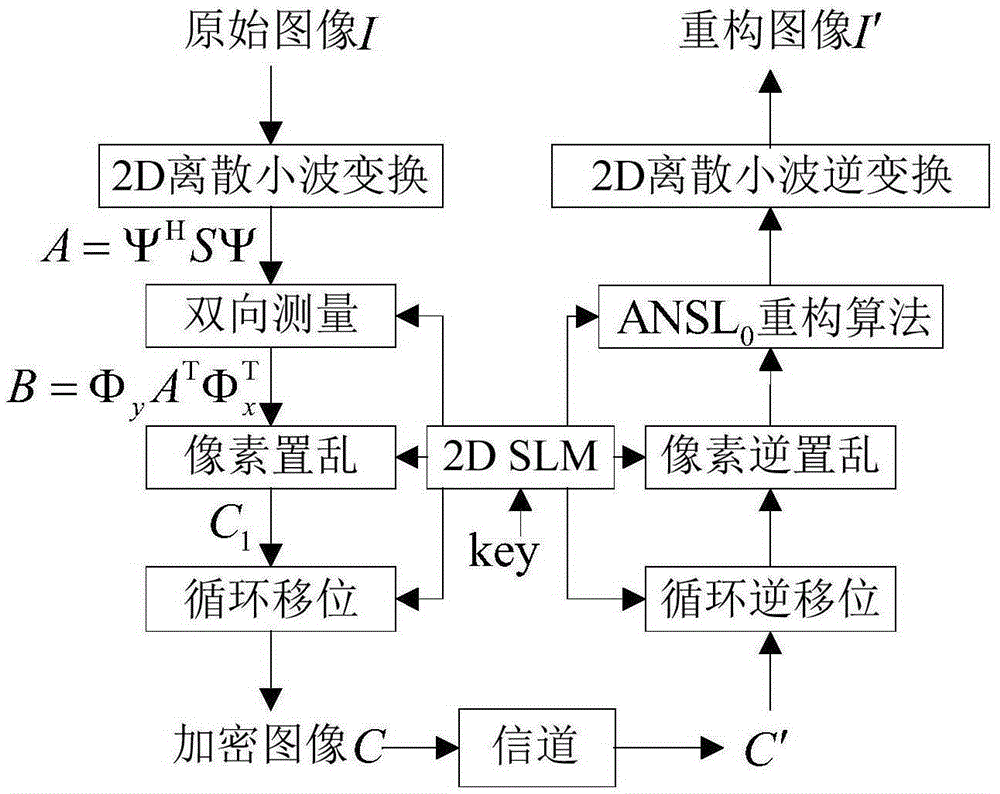
[0040] This implementation scheme is divided into two steps: the first step is based on the generation of the measurement matrix controlled by the chaotic system to realize the measurement encryption to obtain the measured value; the second step is to implement scrambling and diffusion controlled by the chaotic system according to the ring range to obtain the ciphertext. The specific steps of this embodiment are as follows:
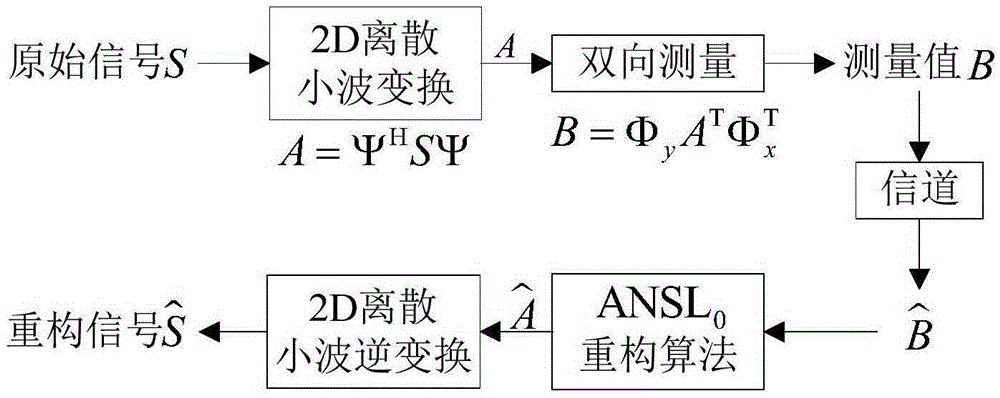
[0041] Step 1: Select the discrete symlet8 wavelet to construct the sparse basis Ψ, and perform two-dimensional discrete wavelet sparse on the image I(x, y) with a size of N×N, and obtain
[0042] A=Ψ T I(x,y) T Ψ(11)
[0043] Take the initial value of x 01 ,y 01 The two-dimensional sine-logistic chaotic map of the following iterations
[0044]
[0045] Amon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com