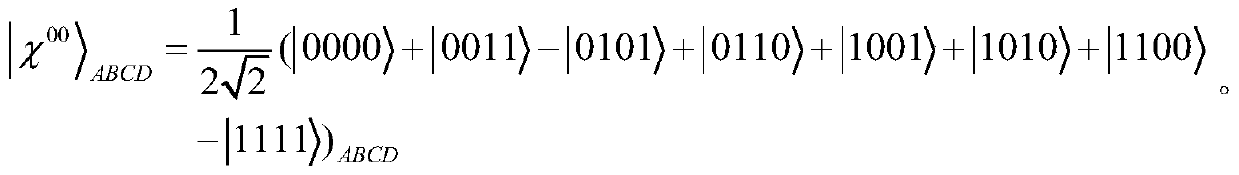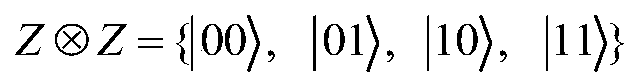Two-Party Quantum Key Agreement Protocol Based on Four-Particle χ State
A quantum key agreement and four-particle technology, applied in the field of two-party quantum key agreement agreement, can solve the problems of low qubit efficiency, inability to resist Trojan horse attacks and delayed photon Trojan horse attacks, etc., and achieve the effect of high qubit efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] 1. Preliminary knowledge
[0024] As we all know, {|0>,|1>} forms the Z basis, and {|+>,|->} forms the X basis, where The four Bell states are defined as follows:
[0025]
[0026]
[0027] They form a set of completely orthogonal basis of four-dimensional Hilbert space, namely Bell basis. The χ state is the maximum entangled state of four particles, and they can form a set of completely orthogonal basis of 16-dimensional Hilbert space. In the protocol of the present invention, we use the following χ state as the quantum information source, namely
[0028]
[0029] According to the expression, if for the χ state |χ 00 > ABCD Bell measurements are performed on particles A and B, and on particles C and D basis measurement, the system collapses to the state |φ with probability 1 / 4 + > AB |00> CD ,|ψ - > AB |01> CD ,|ψ + > AB |10>CD and |φ - > AB |11> CD .
[0030] 2. The two-party quantum key agreement protocol based on the four-particle χ sta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com