Power-grid industrial control protocol vulnerability mining system and method based on fuzzy test
A technology for fuzzing testing and industrial control protocols, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as loophole mining of power grid industrial control protocols, and achieve the effect of fast and effective identification, easy implementation, and simplified testing process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be described in further detail below in conjunction with the accompanying drawings.
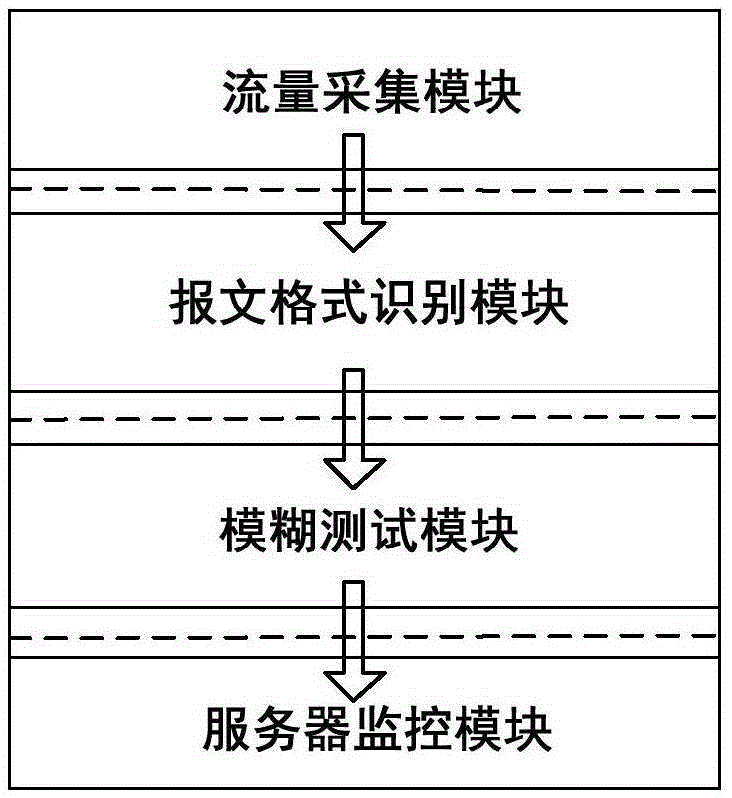
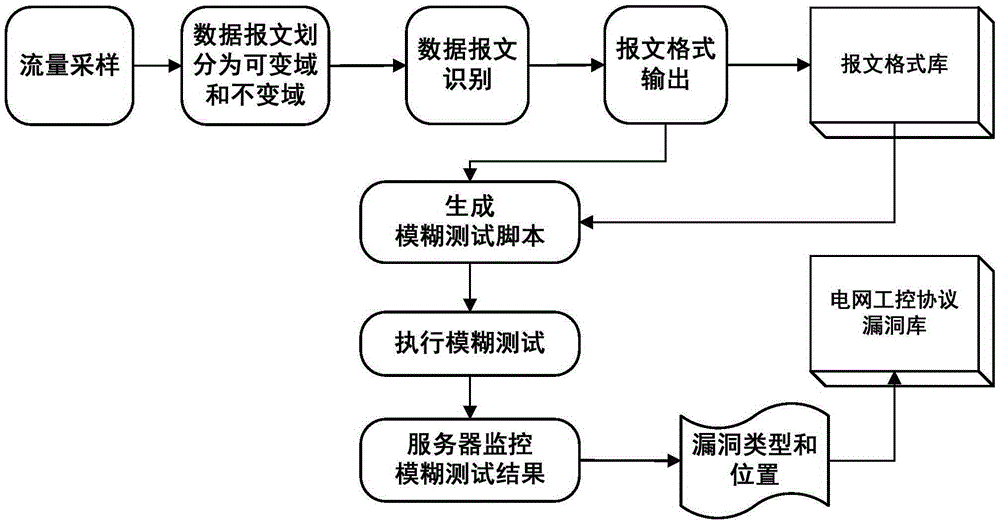
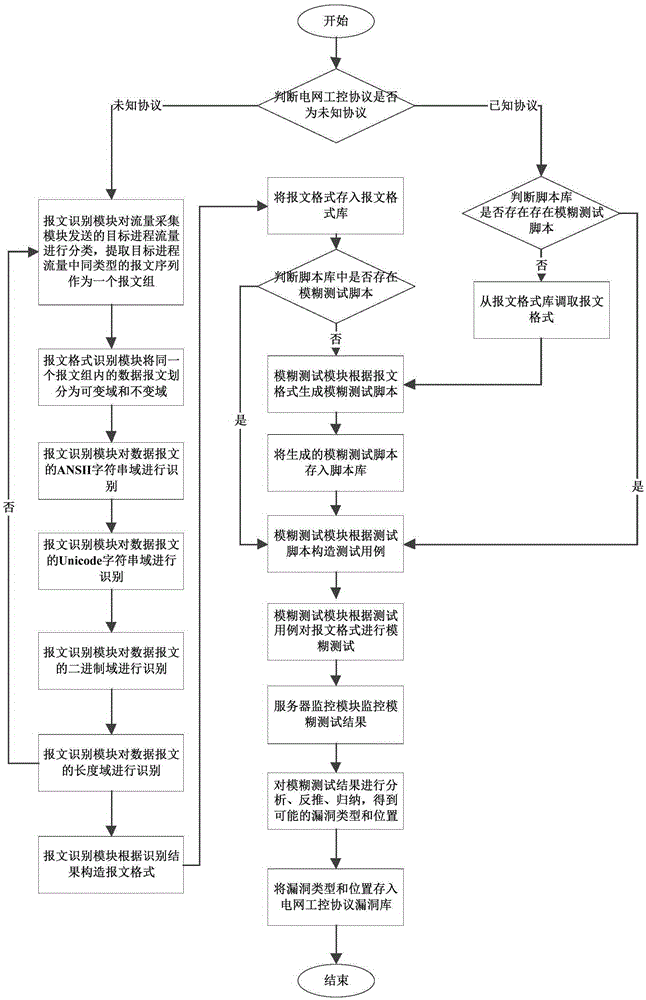
[0047] The present invention provides a system for mining loopholes in power grid industrial control protocols based on fuzzy testing, such as figure 1 and figure 2 , the system includes a flow collection module, a message format recognition module, a fuzzy testing module and a server monitoring module; the flow collection module, the message format recognition module, the fuzzy testing module and the server monitoring module are connected in series in sequence.
[0048] The flow collection module collects data packet flow and filters the collected data packet flow, and then sends the filtered target process flow to the message format identification module.
[0049] The power grid industrial control LAN includes Ethernet, which includes shared Ethernet and switched Ethernet.
[0050] For shared Ethernet, the flow collection module collects data packet flow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com