Method for guaranteeing secure transmission of wireless data based on fountain codes
A wireless data transmission and wireless data technology, applied in the direction of digital transmission system, transmission system, electrical components, etc., can solve the problems of unguaranteed security and difficult realization of dynamic wireless network, etc., and achieve the effect of reasonable design and simple operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific implementation examples.
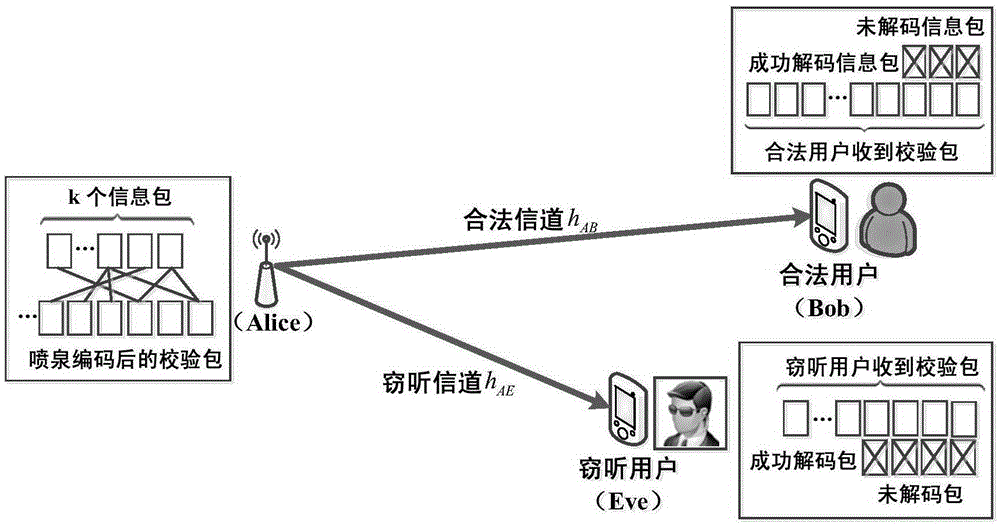
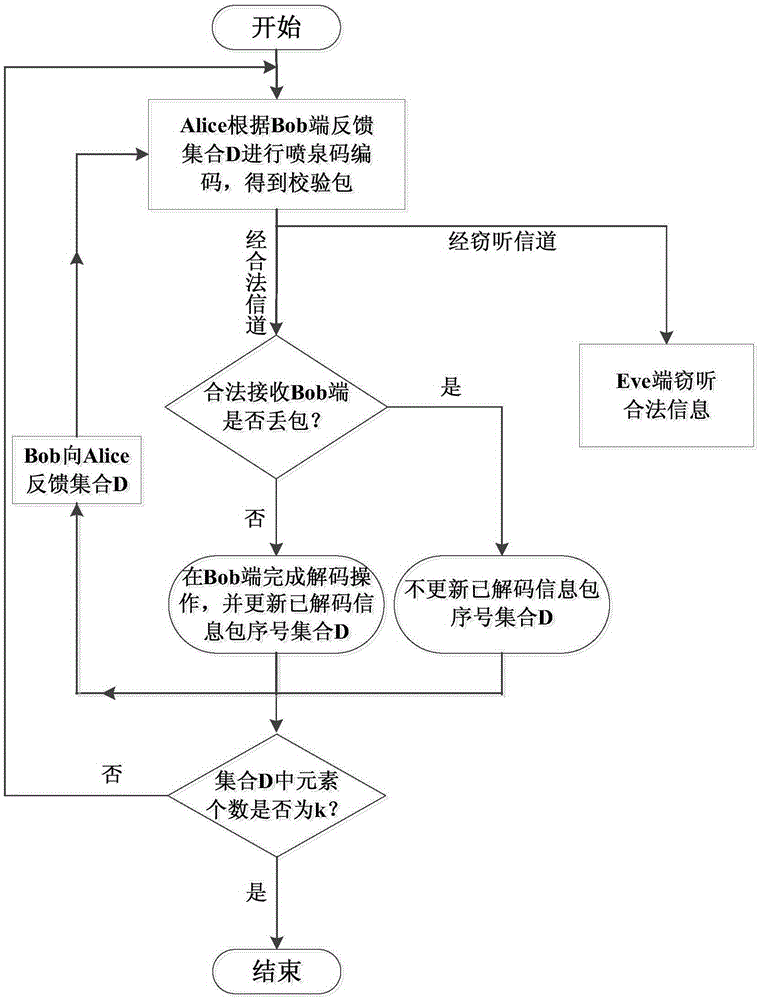
[0033] Fountain code uses a linear encoding and decoding method, which allows the sending end to continuously generate encoding symbols, and does not stop encoding and sending until it receives feedback from the user that it has been correctly received. It is a channel encoding that increases transmission reliability. The sender does not need to know the channel state information of the legal receiver, but it can still ensure reliable data transmission. When the sending end of wireless transmission uses fountain code encoding, it will stop encoding and sending until it receives feedback from the legal receiving end that it has received correctly.
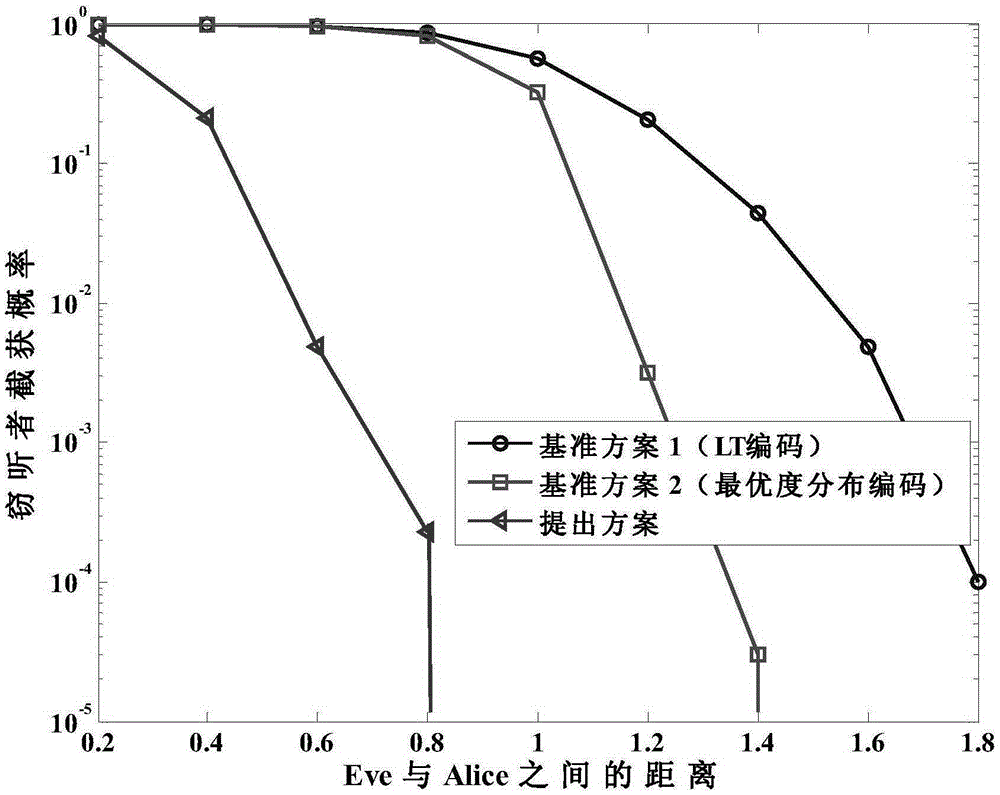
[0034] The core idea of the present invention is that in the process of wireless data transmission, the sending end uses the fountain code encoding method to encode k informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com