File secure loading implementation method and apparatus
An implementation method and file technology, applied in the network field, can solve problems such as extended processing time, long download time, waste of resources, etc., and achieve the effect of shortening the time of elimination and cleaning, improving speed and efficiency, and reducing the possibility of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
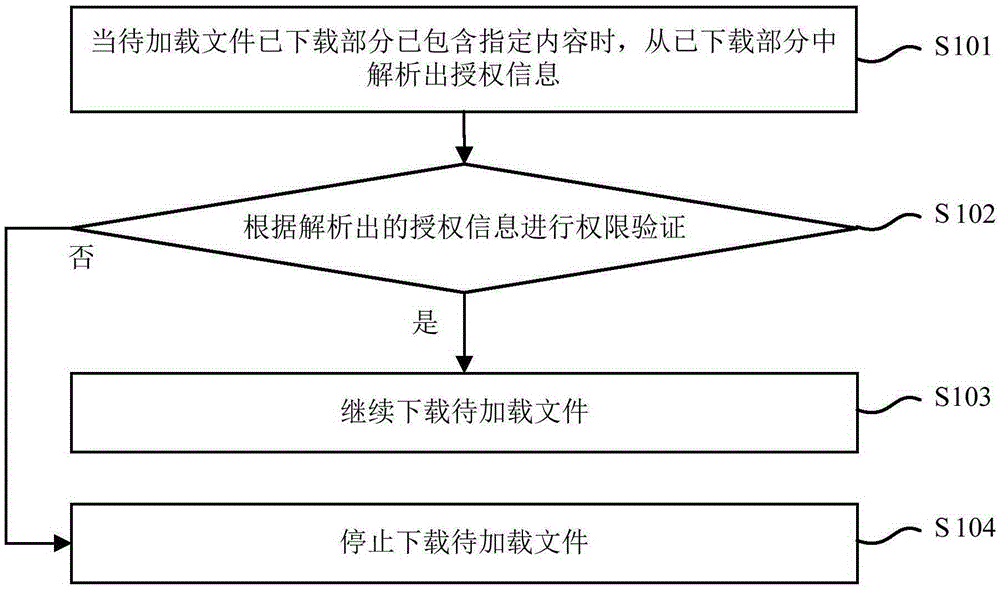
[0074] Embodiment 1 of the present invention provides a method for implementing secure file loading, the process of which is as follows figure 1 shown, including the following steps:
[0075] Since files in wmi format have a feature, they need to be encrypted as a whole and authorized, but in fact, the authorization information is usually in the file header or a certain position in the file, and when downloading the file, the download method is used to download the file. The completed part can be parsed without waiting for the entire download to be completed. Therefore, as long as the part containing the authorization information in the file to be loaded is downloaded, security verification can be performed.
[0076] Step S101: When the downloaded part of the file to be loaded contains specified content, parse out the authorization information from the downloaded part.
[0077] When the downloaded part of the file to be loaded includes the file header of the file to be loaded...
Embodiment 2
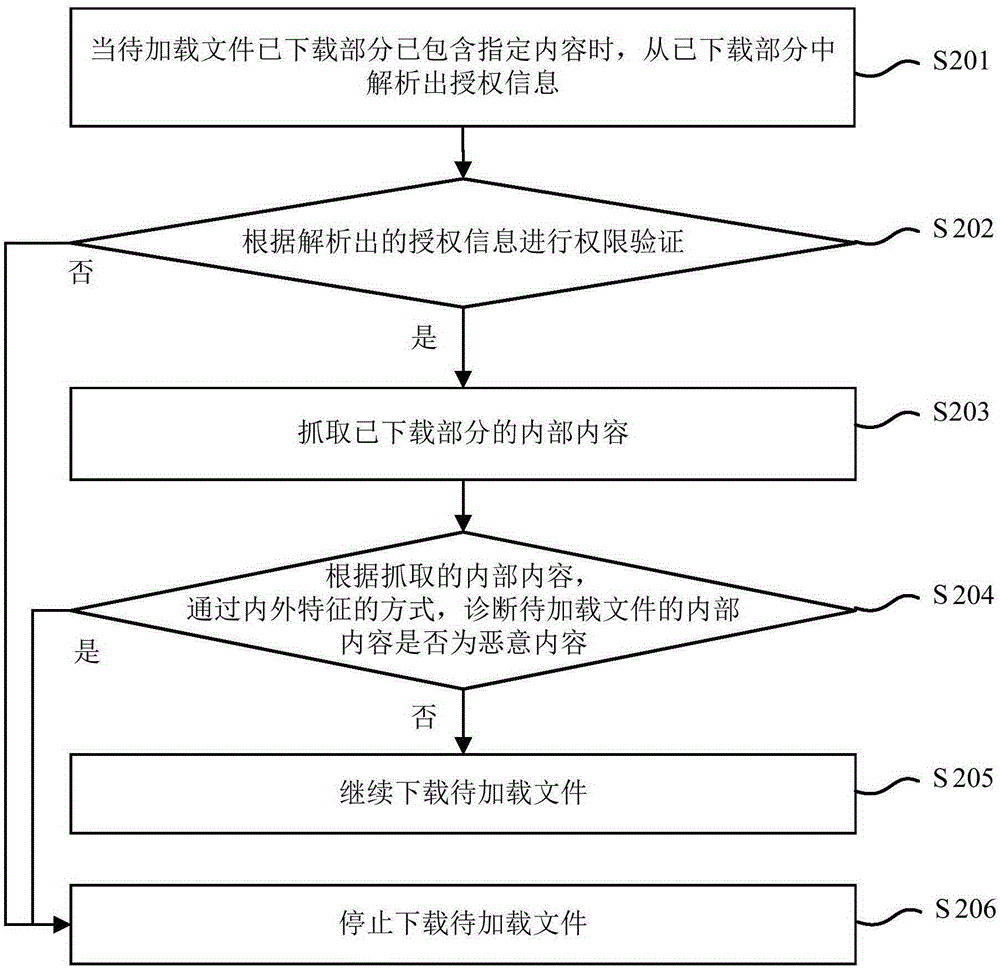
[0096] Embodiment 2 of the present invention provides a method for implementing secure file loading, the process of which is as follows figure 2 shown, including the following steps:
[0097] Step 201: When the downloaded part of the file to be loaded contains specified content, parse out the authorization information from the downloaded part.
[0098] Refer to step S101, which will not be repeated here.
[0099] Step S202: Permission verification is performed according to the parsed authorization information.
[0100] When the verification is passed, step S203 is executed; when the verification is not passed, step S206 is executed.
[0101] Refer to step S102, which will not be repeated here.
[0102] Step S203: Capture the internal content of the downloaded part.
[0103] After the above-mentioned security judgment based on the authorization information, since the file to be loaded is also in the process of downloading, it is also possible to go to the background to che...
Embodiment 3
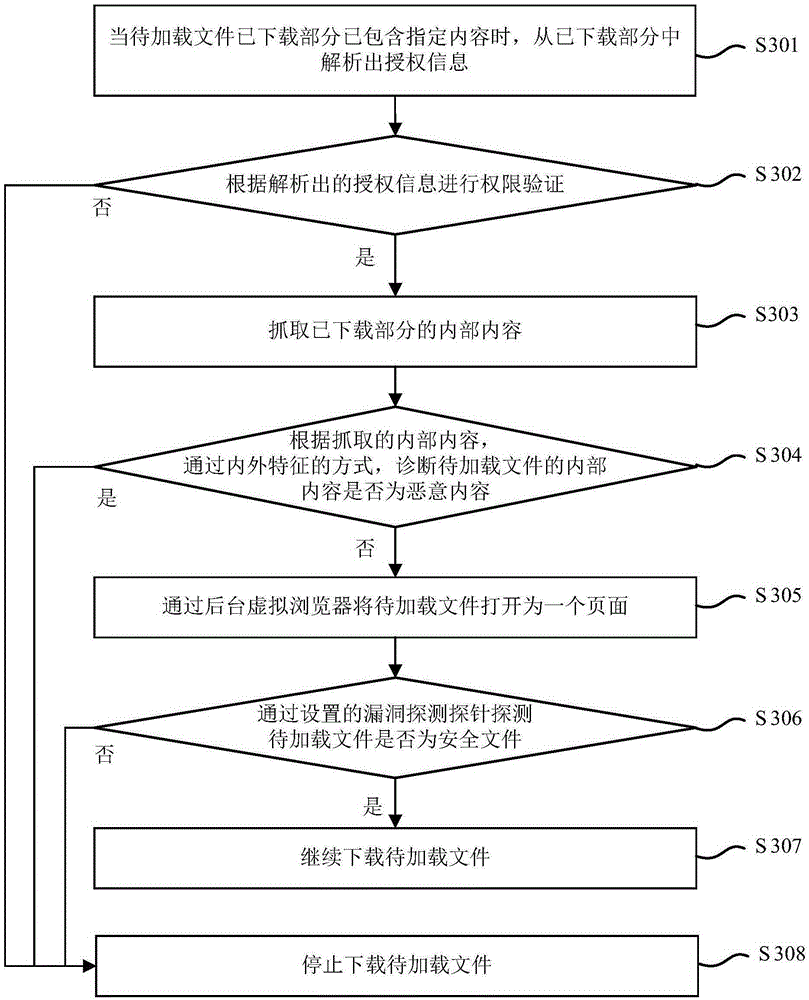
[0115] Embodiment 3 of the present invention provides a method for implementing secure file loading, the process of which is as follows image 3 shown, including the following steps:
[0116] Step 301: When the downloaded part of the file to be loaded contains specified content, parse out the authorization information from the downloaded part.
[0117] Refer to step S101, which will not be repeated here.
[0118] Step S302: Permission verification is performed according to the parsed authorization information.
[0119] When the verification is passed, step S303 is executed; when the verification is not passed, step S308 is executed.
[0120] Refer to step S102, which will not be repeated here.
[0121] Step S303: Capture the internal content of the downloaded part.
[0122] Refer to step S203, which will not be repeated here.
[0123] Step S304: According to the captured internal content, diagnose whether the internal content of the file to be loaded is malicious content ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com