Identity authentication method, identity authentication device and identity authentication system
An identity verification method and identity verification technology, applied in user identity/authority verification, transmission systems, digital transmission systems, etc., can solve problems such as insufficient security and easy cracking, and achieve high security and increase the difficulty of cracking Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
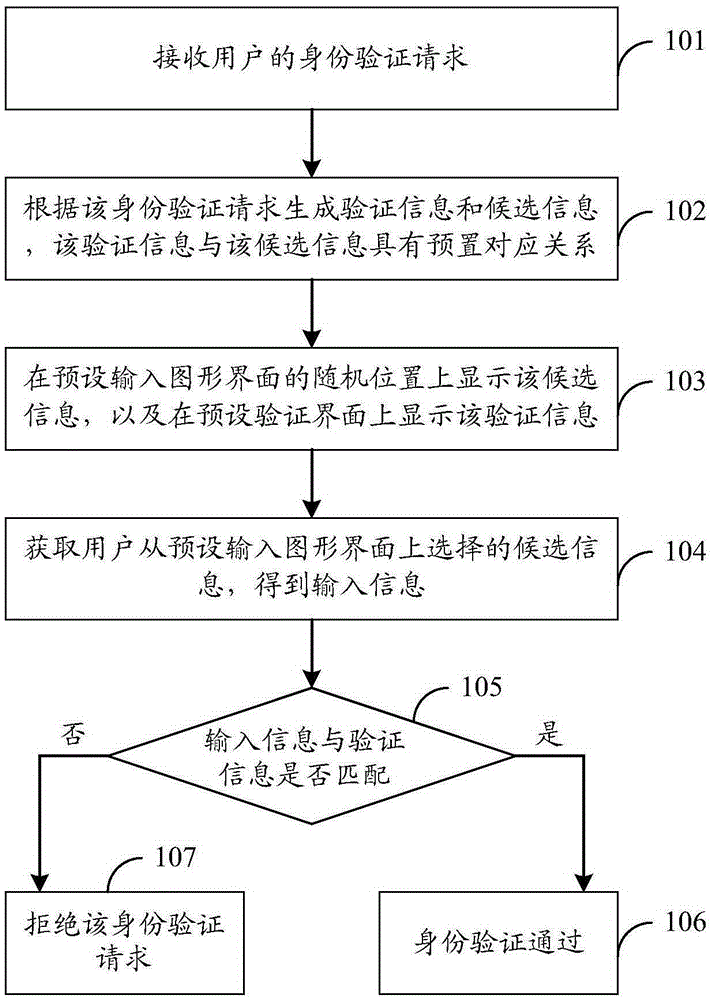
[0045] This embodiment will be described from the perspective of an identity verification device. Specifically, the identity verification device may be integrated into a terminal, a server, or other devices that require identity verification.
[0046] An identity verification method, characterized in that it includes: receiving a user's identity verification request; generating verification information and candidate information according to the identity verification request, and the verification information has a preset corresponding relationship with the candidate information; Display the candidate information at a random position on the preset verification interface, and display the verification information on the preset verification interface; obtain the candidate information selected by the user from the preset input graphical interface to obtain input information; determine whether the input information and the verification information are match; if it matches, it is deter...
Embodiment 2
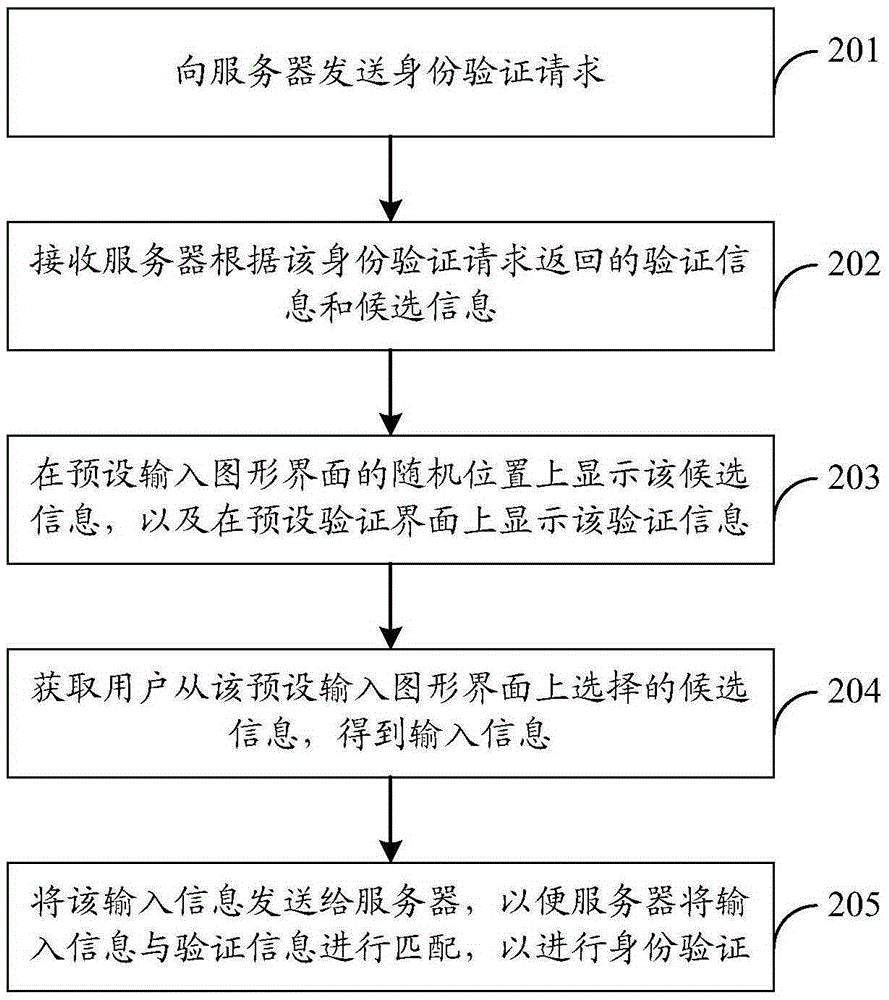
[0087] If the identity verification device of Embodiment 1 is integrated in the server, when displaying candidate information and verification information, it can be displayed specifically through the terminal, that is, another identity verification method can be provided in the embodiment of the present invention, which will be described below.
[0088] This embodiment will be described from the perspective of an identity verification triggering device. The identity verification triggering device may be integrated in a terminal, for example, installed in the terminal in the form of a client or other software.
[0089] An identity verification method includes: sending an identity verification request to a server; receiving verification information and candidate information returned by the server according to the identity verification request; displaying the candidate information at a random position on a preset input graphical interface, and displaying the candidate information ...
Embodiment 3
[0110] According to the methods described in Embodiments 1 and 2, examples will be given below for further detailed description.
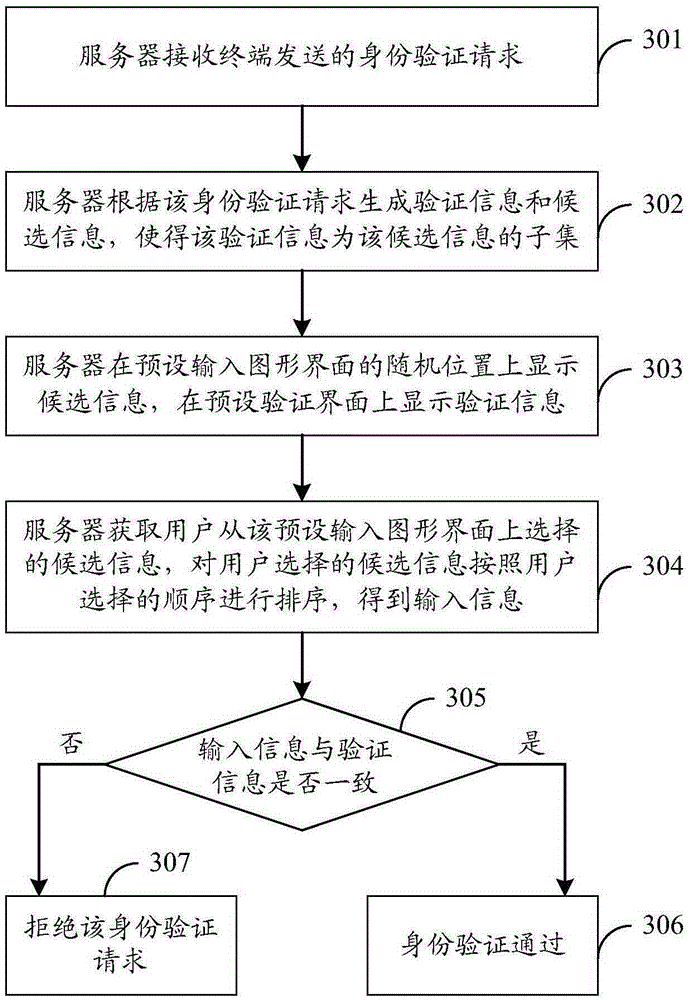
[0111] In this embodiment, it will be described in detail by taking an example in which the identity verification device is integrated in a server and the verification information is a subset of candidate information.
[0112] Such as Figure 3a As shown, an authentication method, the specific process can be as follows:
[0113] 301. The server receives the identity verification request sent by the terminal.
[0114] Wherein, the identity verification request can be sent by the user by triggering the identity verification trigger key, for example, the user can click or slide a trigger key such as "login", "obtain verification code", "unlock" or "verify" to trigger the identity verification request, and so on.
[0115] 302. The server generates verification information and candidate information according to the identity verification request, so t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com