Secure mobile communication architecture with dynamic two-way authentication and implementation method thereof
A mobile communication and two-way authentication technology, applied in the field of mobile information security, can solve the problems of phishing, counterfeiting, man-in-the-middle attacks, etc., to save costs, eliminate counterfeiting, and defend against hacker login attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
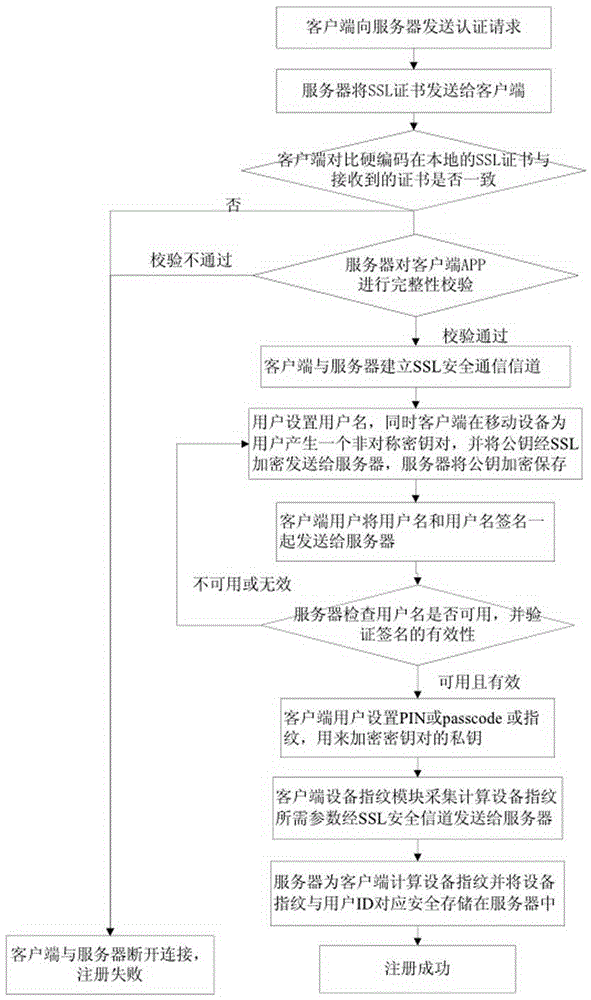
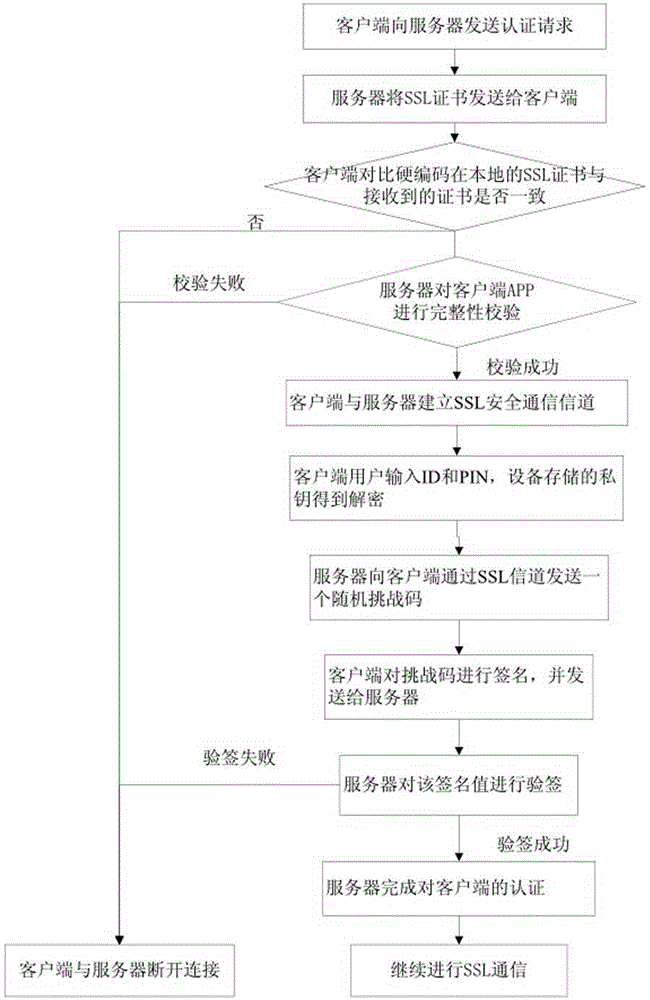
[0071] Embodiment 1, the mobile banking of a certain bank is due to the user blindly trusting the problematic server-side certificate, and the server is attacked by hacker phishing or man-in-the-middle. Communication, in the present invention, the server uses a self-signed certificate, and its certificate verification process is different from the ordinary certificate verification process, and there will be no situation where the user ignores the dangerous server-side certificate reminder, and the hacker cannot successfully communicate with the server without the private key of the server-side certificate. There will be no phishing attack or man-in-the-middle attack when the client terminal establishes a connection.
Embodiment 2
[0072] Example 2, a counterfeit client terminal appeared in an application APP, and the hacker forged a fake client terminal that was very similar to the real APP client terminal, and asked the user to enter the account password to log in, thereby defrauding the user of the account number and password of the application. At this time, the secure mobile communication architecture of dynamic two-way authentication described in the present invention can be used to communicate with the client terminal server. Even if the user steals the user account number and password, without the user's device, the private key of the device cannot be obtained, and it cannot be successfully completed. The challenge-response process between the server and the client terminal makes it impossible to use the user's account and password to perform harmful operations.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com