Photo naming method and naming system
A naming system and photo technology, applied in still image data retrieval, special data processing applications, instruments, etc., can solve the problem of non-targeted security loopholes in photo encryption, and achieve the effect of avoiding leaks, filling security loopholes, and strong pertinence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
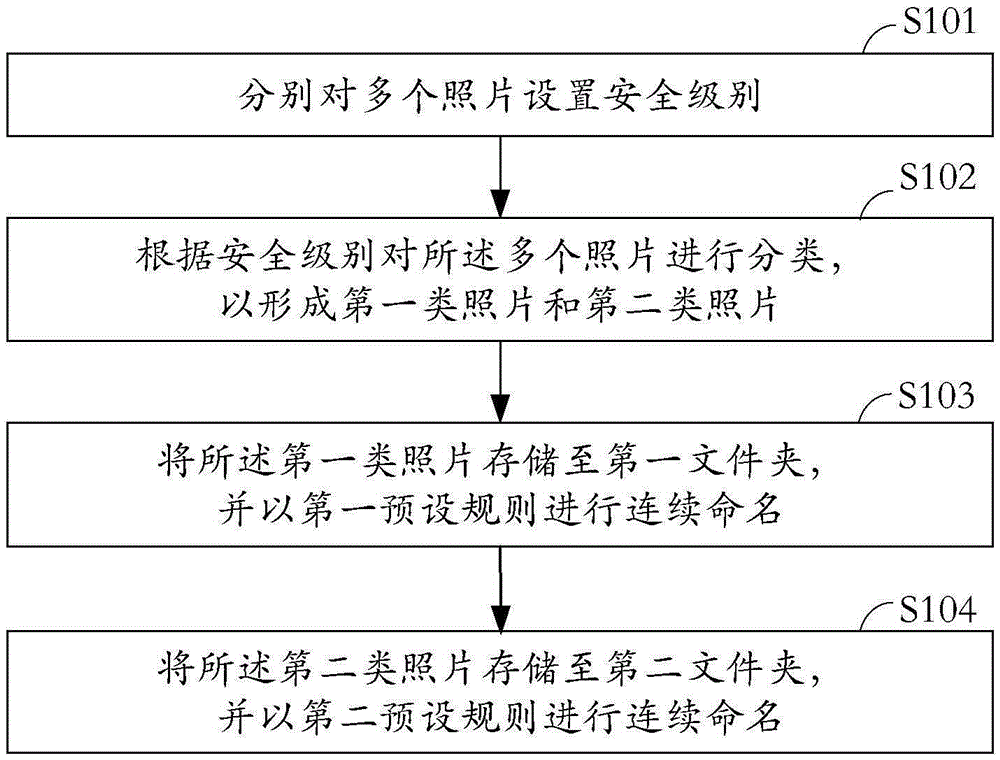
[0029] see figure 1 , which is a schematic flowchart of a method for naming photos provided by an embodiment of the present invention. The naming method of the photos is mainly implemented in terminal devices such as smart phones and digital cameras, and will not be enumerated here.
[0030] The naming method of the photos, including:
[0031] In step S101, security levels are respectively set for a plurality of photos.
[0032] Wherein, the security level includes: a high security level and a low security level.
[0033] The selection rules for the setting include one or a combination of the following methods:
[0034] (1) Locate the shooting location, such as the first meeting room of a building in Nanshan District, Shenzhen City, Guangdong Province. The photos taken at this location are all of high security level;
[0035] (2) Set the shooting time, such as 2015-09-18 9:00~11:00, the photos taken during this time period are all of high security level;
[0036] (3) Loca...
Embodiment 2
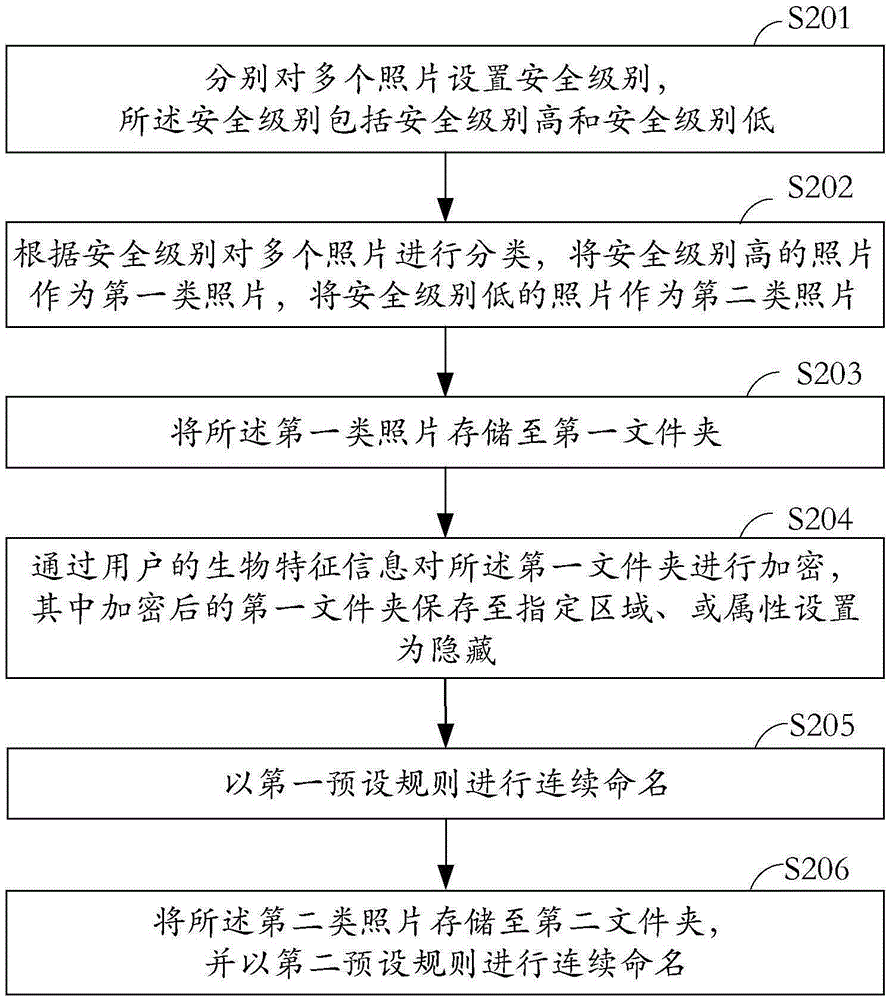
[0050] see figure 2 , which is a schematic flowchart of a method for naming photos provided by an embodiment of the present invention. The method for naming photos is mainly implemented in smart phones.
[0051] The naming method of the photos, including:
[0052] In step S201, security levels are respectively set for a plurality of photos, and the security levels include high security level and low security level.
[0053] The selection rules for the setting include one or a combination of the following methods:
[0054] (1) Locate the shooting location, and the photos taken at this location are all of high security level;
[0055] (2) Set the shooting time, and the photos taken during this time period are all of high security level;
[0056] (3) Locate the keyword, if the captured content is a document, whether the full text of the search contains the keyword, if included, the security level is high;
[0057] (4) Collect the characteristics of the portrait, and the pho...
Embodiment 3
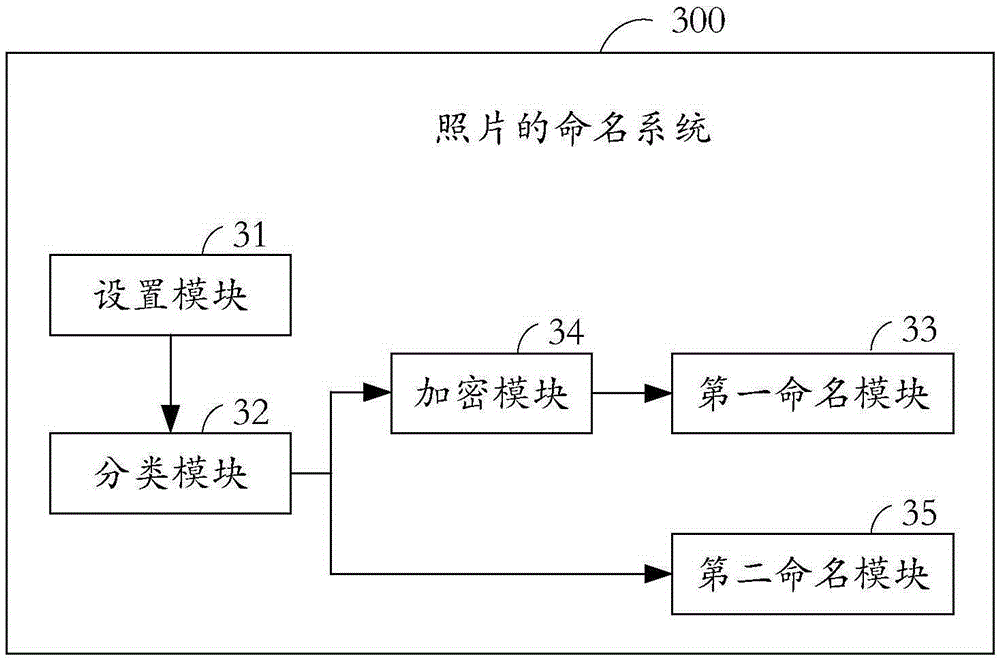
[0080] see image 3 , is a block diagram of a photo naming system provided by an embodiment of the present invention. The photo naming system is mainly implemented in terminal devices such as smart phones and digital cameras, and will not be listed here.
[0081] The photo naming system 300 includes: a setting module 31 , a classification module 32 , a first naming module 33 , an encryption module 34 , and a second naming module 35 .
[0082] The setting module 31 is connected to a memory (not shown) in the terminal device, such as a gallery or a photo folder, and is used to set security levels for multiple photos therein.
[0083] Wherein, the security level includes: a high security level and a low security level.
[0084] The selection rules for the setting include one or a combination of the following methods:
[0085] (1) Locate the shooting location, such as the first meeting room of a building in Nanshan District, Shenzhen City, Guangdong Province. The photos taken a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com