Effective novel anti-counterfeiting method based on physical unclonable function
A new method and physical technology, applied in the anti-counterfeiting field of products, can solve problems such as insufficient security, difficulty in resisting clone attacks, and difficult implementation, and achieve the effect of ensuring security, low price, and small size
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The drawings are for illustrative purposes only, and should not be construed as limitations on this patent; in order to better illustrate this embodiment, some parts in the drawings will be omitted, enlarged or reduced, and do not represent the size of the actual product;
[0034] For those skilled in the art, it is understandable that some well-known structures and descriptions thereof may be omitted in the drawings. The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
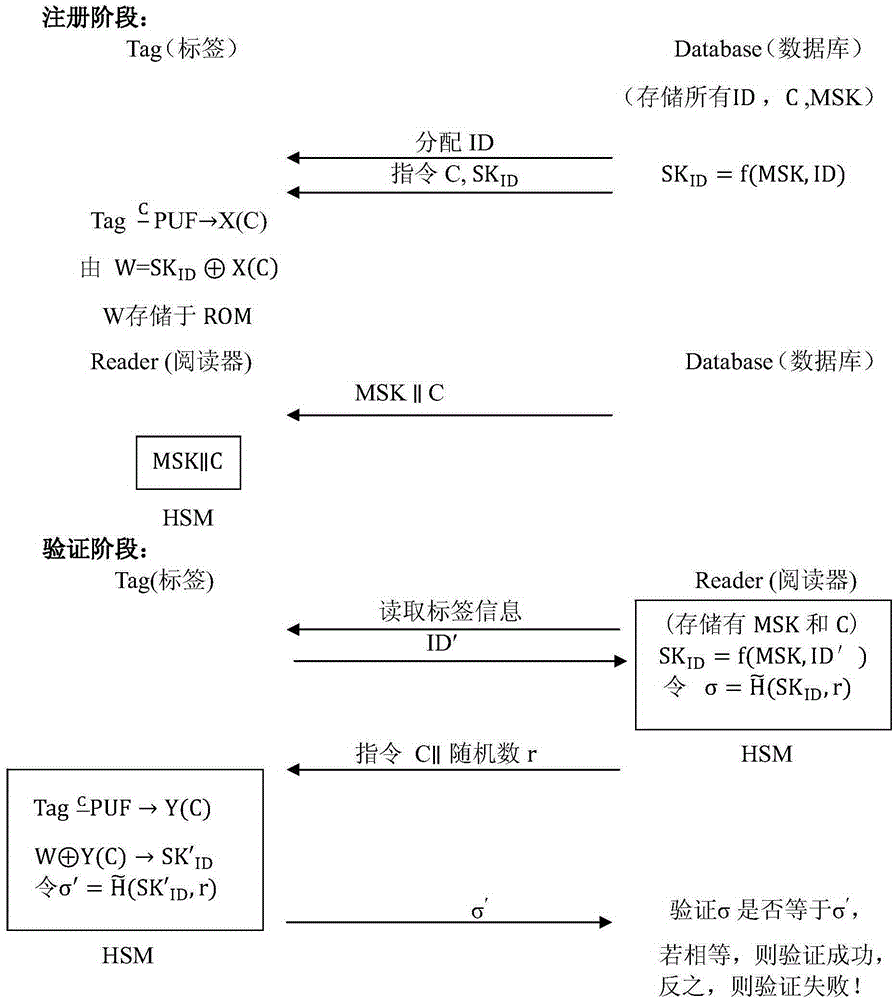
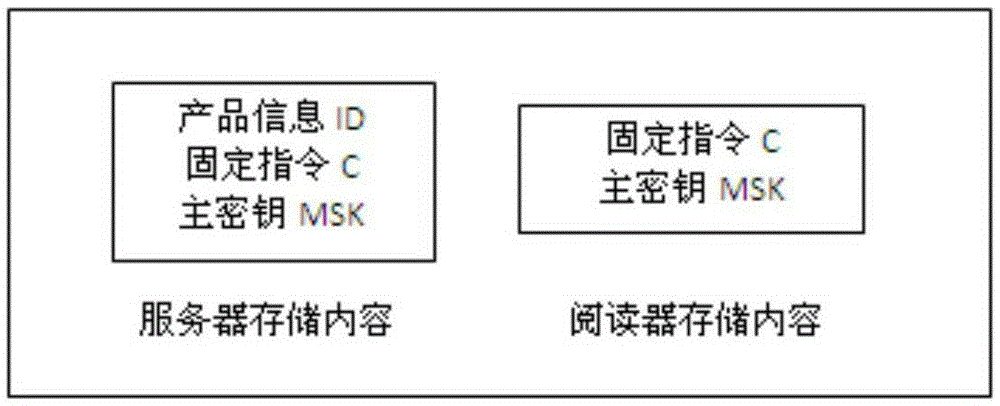
[0035] The present invention uses PUF technology to resist the cloning attack of the label, uses the message verification code technology to complete the certification of product legitimacy, and uses the storage of auxiliary data to reduce the storage complexity of the electronic tag end, and uses the reader to store the master key and instruction C To achieve offline verification, each electronic tag contains at...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com