Method for encrypting extended file system based on Linux
A file system and encryption method technology, applied in the field of information security, can solve the problems of expansion, unable to use the national secret algorithm, no hardware encryption, etc., to achieve the effect of small space overhead, fewer components, and strong portability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
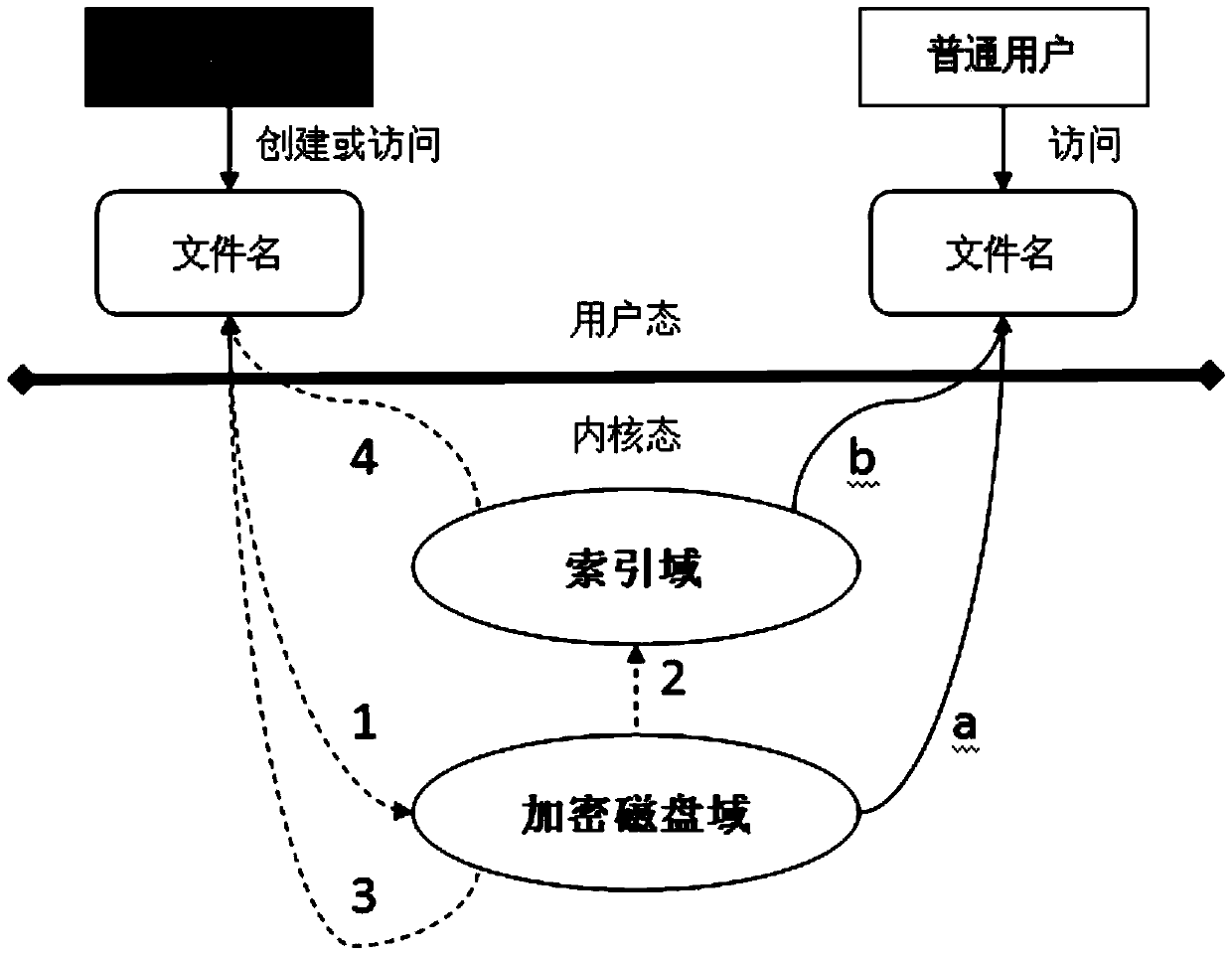
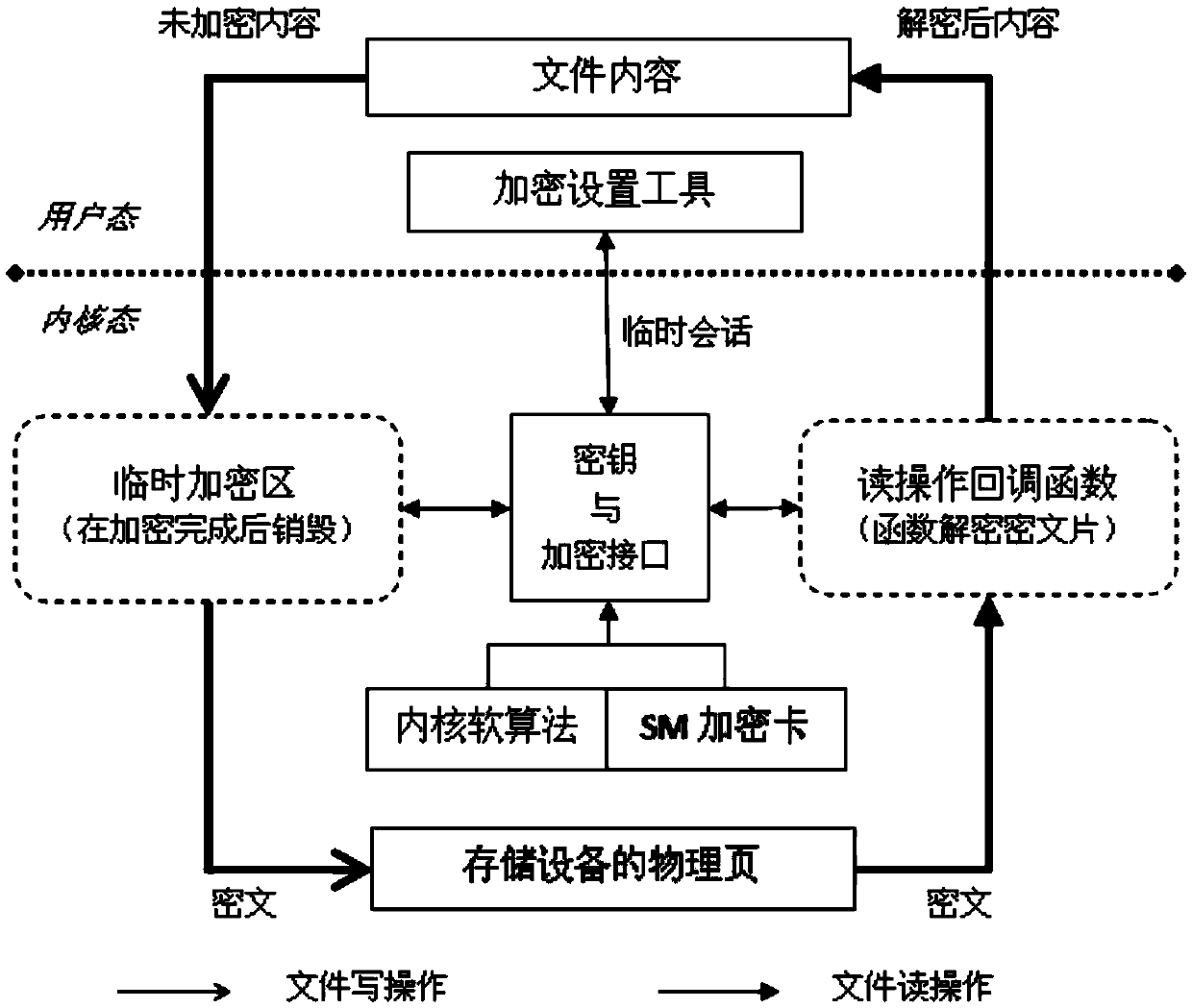
[0022] The present invention comprises two parts:
[0023] 1. Encryption setting tool: It runs in user mode and provides policy setting and key management tools.
[0024] The policy setting tool creates an encrypted path or file based on user input, and binds it with the specified key.
[0025] Key management tool for importing, updating, querying and destroying keys.
[0026] When the tool is running, it will establish a temporary session with the kernel's key module ( / proc / keys).
[0027] 2. The e4crypt kernel module.
[0028] According to the algorithm strategy, the encryption and decryption operations are performed at the bottom layer of the file system, and the temporary page and read callback technology are used to encrypt and decrypt the ciphertext in the physical page respectively.
[0029] Below is the detailed introduction of the inventive method:
[0030] A Linux-based extended file system encryption method, such as figure 1 and figure 2 As shown, it specific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com