Client login method and system through regional information sharing
A technology for sharing an area and a login method, applied to a system implementing the above method, can solve the problems of complicated operation, leakage, insufficient confidentiality and security of account numbers and passwords, etc., through the client login field of shared area information, and achieve convenient operation. , to ensure the effect of safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
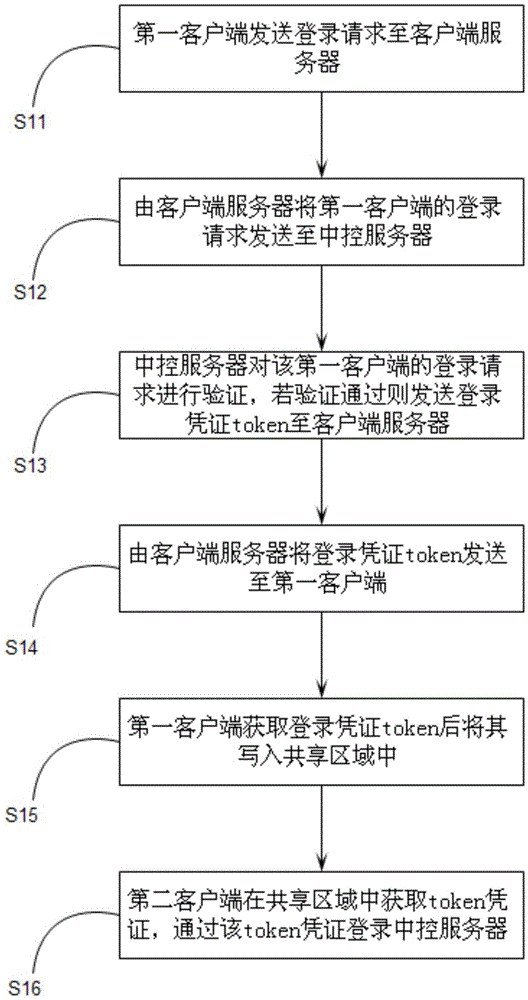
[0037] See figure 1 , Which is a step flowchart of the client login method through shared area information in Embodiment 1 of the present invention.
[0038] The present invention provides a client login method through sharing area information, which specifically includes the following steps:
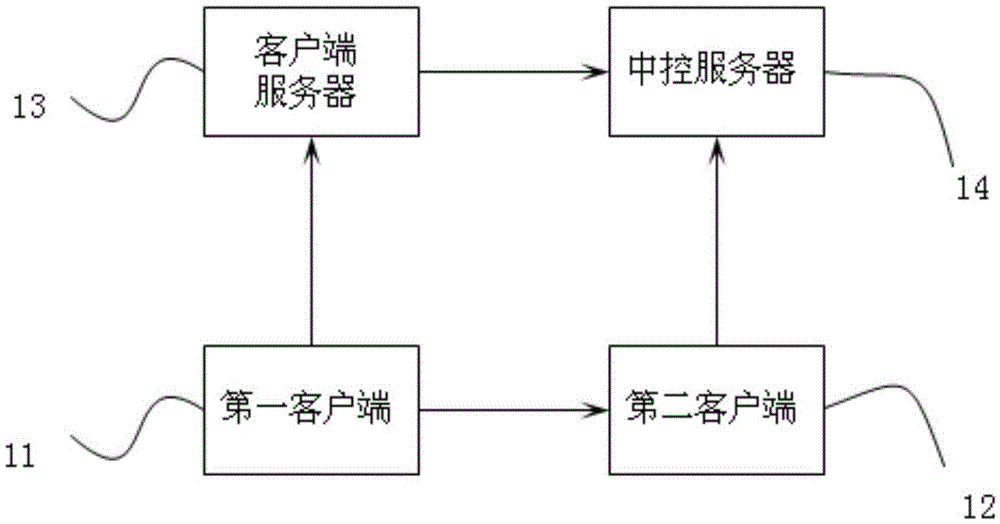
[0039] S11: The first client sends a login request to the client server.
[0040] S12: The client server sends the login request of the first client to the central control server.
[0041] S13: The central control server verifies the login request of the first client, and if the verification passes, sends the login credential token to the client server.
[0042] S14: The client server sends the login credential token to the first client.
[0043] S15: After obtaining the login credential token, the first client writes it into the shared area.
[0044] S16: The second client obtains the token certificate in the shared area, and logs in to the central control server through the token certificate.
[0...
Embodiment 2
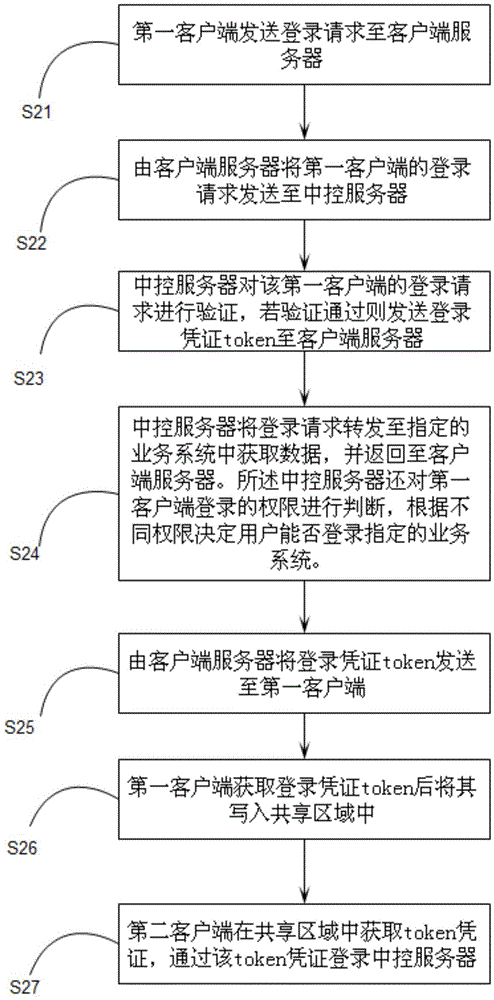
[0058] The present invention provides another client login method through sharing area information, which specifically includes the following steps:
[0059] S21: The first client sends a login request to the client server.
[0060] S22: The client server sends the login request of the first client to the central control server.
[0061] S23: The central control server verifies the login request of the first client, and if the verification passes, sends the login credential token to the client server.
[0062] S24: The central control server forwards the login request to the designated business system to obtain data, and returns it to the client server. The central control server also judges the login authority of the first client, and determines whether the user can log in to the designated business system according to different authority. At the same time, the central control server also performs data storage and extraction through the database and processing through the distribute...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com