Security reinforcement method for virtual machine in desktop cloud environment
A virtual machine, desktop cloud technology, applied in computer security devices, software simulation/interpretation/simulation, program control design, etc., can solve the problem of security without doing any work, unaware of the security risks of virtualization technology, and difficult to find Problems such as deep-level problems of desktop virtualization technology, to achieve the effect of security reinforcement and ensure the security of virtual machines
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
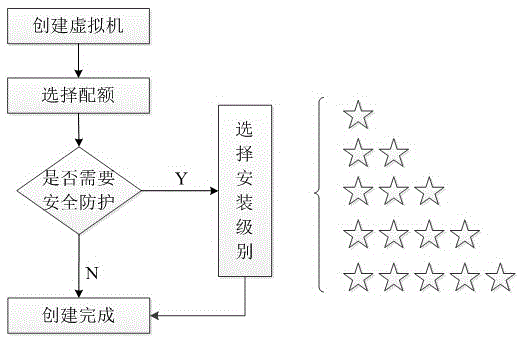
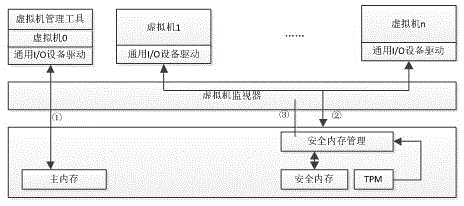
[0029] In the embodiment of the present invention, a virtual machine security hardening method in a desktop cloud environment, the specific implementation mainly includes the following parts:
[0030] 1. Remote desktop protocol port dynamic change method
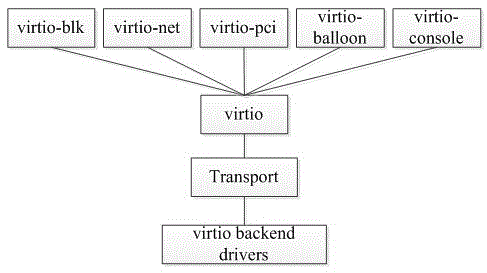
[0031] The SPICE client and server communicate using the SPICE protocol, and are connected through channels, each of which is responsible for a specific type of data transmission and communication. Each channel uses a dedicated TCP connection socket (socket), which can be encrypted (using SSL). On the client, each channel uses a dedicated thread for processing. When the network is busy or there is a QoS (Quality of Service) request, you can set the priority of different threads or dynamically close or open different channels according to the actual situation. to achieve different QoS. Since SPICE uses socket programming, the Token generated when each user logs in is dynamically bound here. The present invention controls u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com