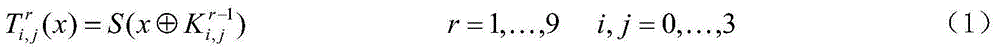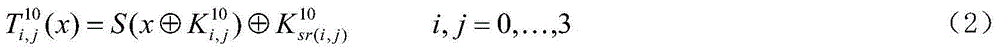White-box cryptograph non-linear encoding protection method based on table lookup
A non-linear coding and white-box cipher technology, which is applied in the field of non-linear coding protection of white-box ciphers based on look-up tables, can solve the problems of unable to extract the key and small amount of calculation, and achieve strong confidentiality and security, and computing small effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
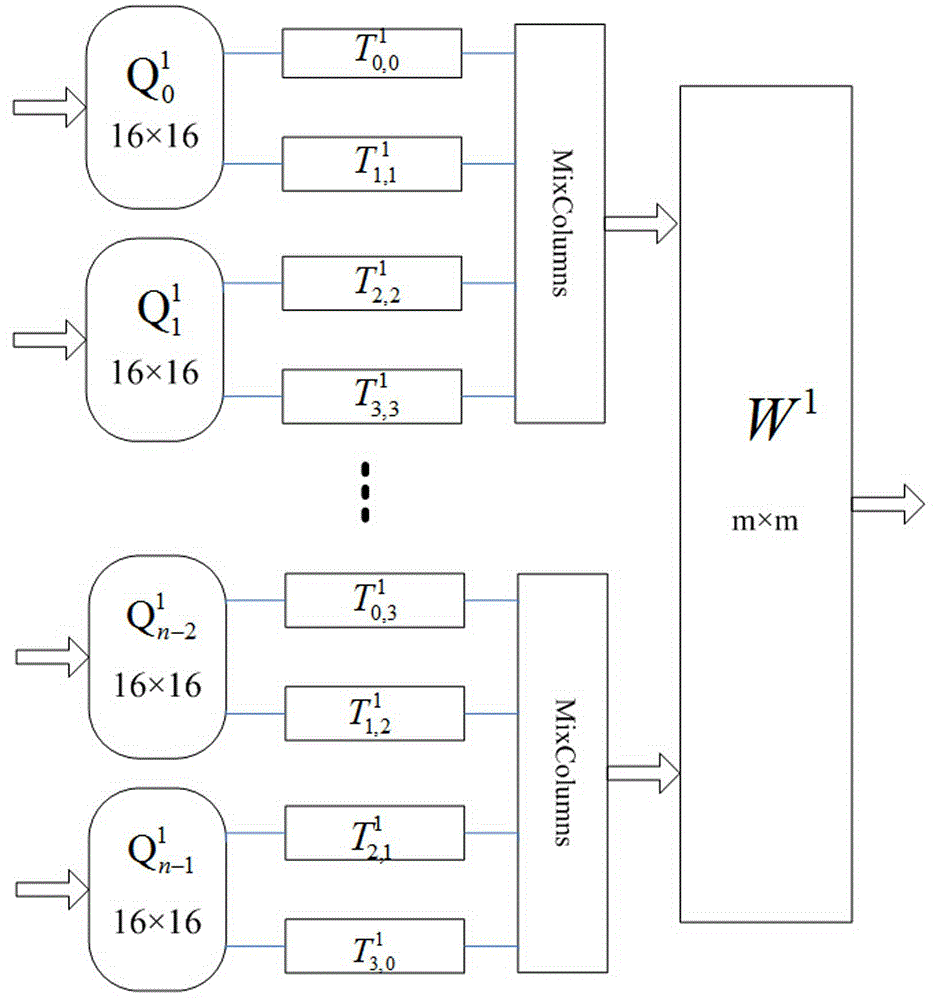
[0025] A non-linear encoding protection method of white-box cipher based on look-up table:
[0026] 1) Divide the m sensitive variables in the original cryptographic algorithm into n groups of 16 bits each, and pass through non-linear scrambling;
[0027] 2) the output of the Q transformation in step 1) is used as the input of the internal scrambling of the original cryptographic algorithm SP structure, wherein through T transformation and MixColumns transformation successively;
[0028] 3) Take all the outputs in step 2) and go through W 1 transform;
[0029] 4) The output of step 3) is taken as the final output of the current round of iterative process, and sent to the next round of iterative steps of the cryptographic algorithm until the end of the last round, thereby obtaining the ciphertext of the white-box cipher.
[0030] In step 1), the Q transform is an external nonlinear scrambling of 16-bit input and 16-bit output with good cryptographic properties constructed b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com