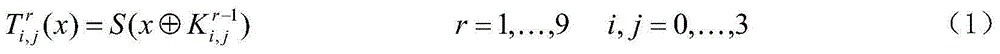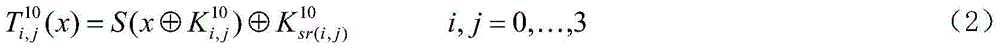White-box password nonlinear coding protection method based on combination of table look-up and disturbance scrambling
A non-linear encoding and perturbation scrambling technology, applied in the field of information security, can solve problems such as small amount of calculation and inability to extract keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
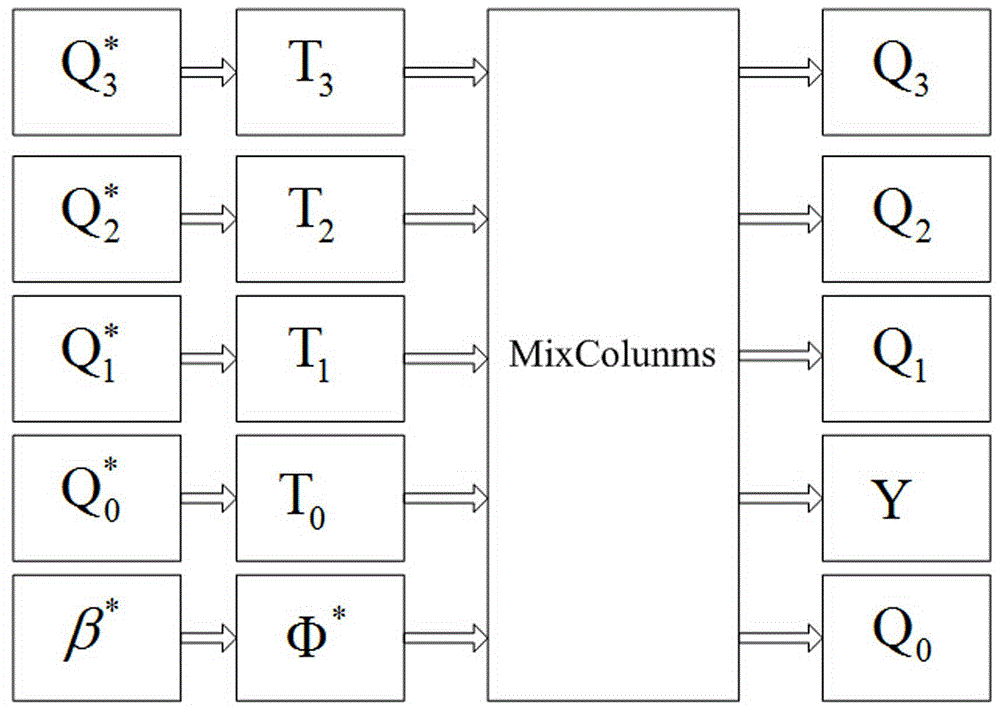
[0026] A white-box cipher non-linear encoding protection method based on a combination of table lookup and disturbance scrambling, comprising the following steps:
[0027] 1) The 32-bit sensitive variable during the operation of the cryptographic algorithm is divided into four groups on average, each group is 8 bits, namely (x 0,0 ,x 0,1 ,x 0,2 ,x 0,3 ), and in turn through non-linear scrambling;
[0028] 2) Add disturbance information (β * ,Y,Φ * ), here we choose to add only one set of disturbance information as an illustration, and calculate β * =F(x 0,0 ,x 0,1 ,x 0,2 ,x 0,3 ) as an initial disturbance item, wherein F is a mapping from 32 bits to 8 bits;
[0029] 3) Pass the output of step 1) and step 2) sequentially through T 3 , T 2 , T 1 , T 0 ,Φ * transform;
[0030] 4) Modify the column confusion transformation (MixColumns) operation. The modified MixColumns operation still has the same effect on the original 4 input blocks, and the disturbing informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com