Method for providing security for common intermediate language-based program
A universal intermediate language and security technology, which is used in the field of providing security for programs based on universal intermediate language, and can solve problems such as source code leaks, program analysis difficulties, and the inability of technology to become a fundamental solution.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Hereinafter, the present embodiment will be described in detail with reference to the drawings.
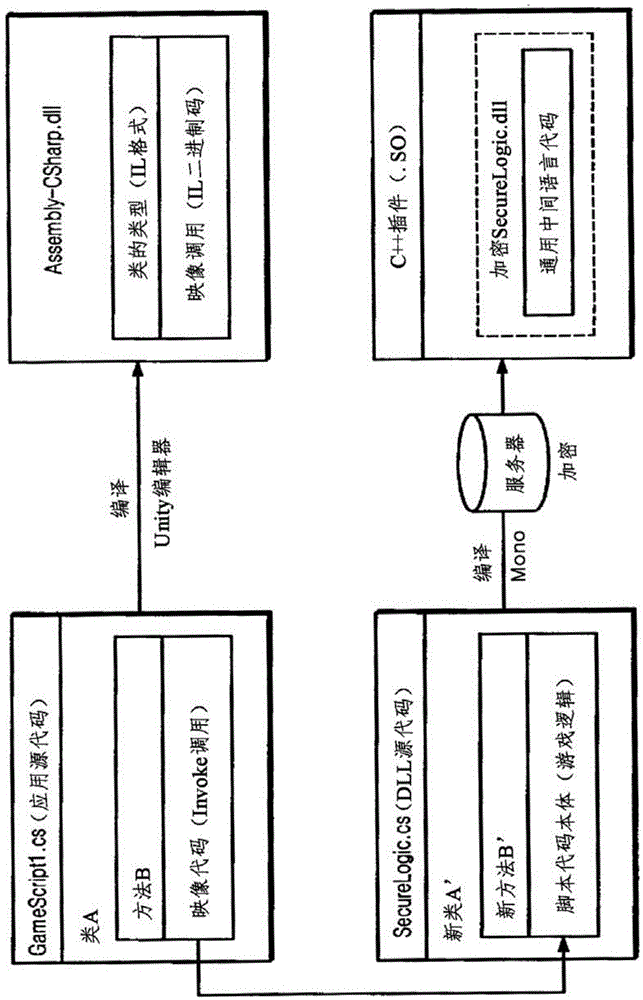
[0027] Embodiments of the present invention relate to a common intermediate language code application, a DLL containing the application's key algorithm or logic, and a plug-in containing the encryption DLL and providing security functions. The plug-in should be a local code made by C / C++, such as Android NDK (Native Development Kit, native development kit) and XCode. If the plug-in is made in a language that creates common intermediate language code (eg, C# and Java), the plug-in itself may be hacked and thus the security functions provided by the plug-in may be disabled.
[0028] The following examples are directed at applications made in the Unity-based C# language and plug-ins made in C / C++ with native code support. However, the technical idea of the present invention should not be limited thereto.
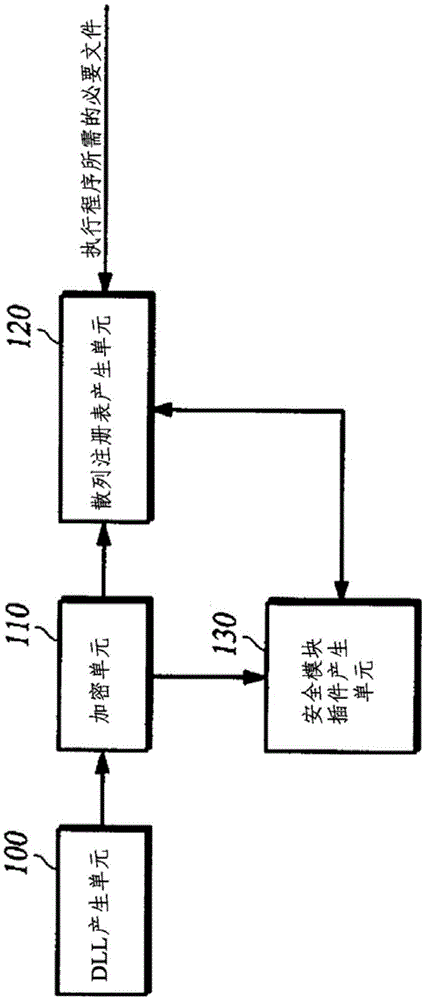
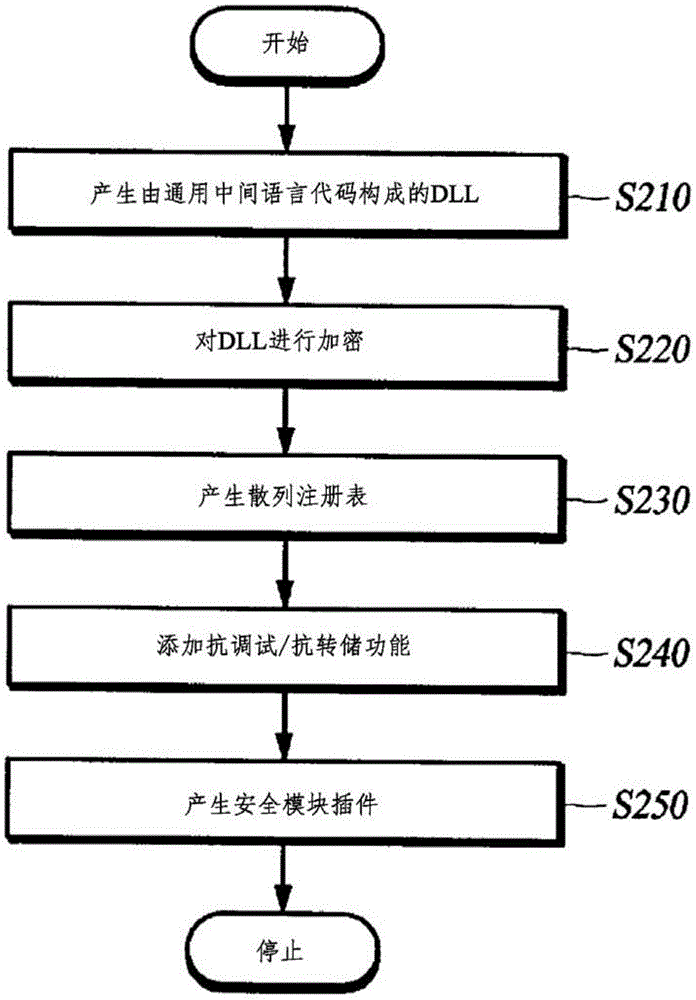
[0029] figure 1 is a configuration diagram of an apparatus for gen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com