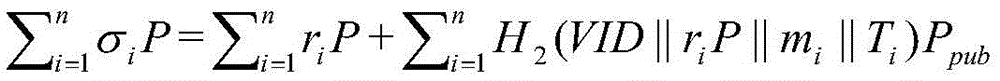Privacy protection batch authentication method without pairing operation in vehicular ad hoc network
An in-vehicle self-organization and privacy protection technology, which is applied to user identity/authority verification and key distribution, can solve the problems of large amount of calculation, reduced calculation efficiency, and reduced scheme calculation efficiency, so as to reduce overhead, improve actual operation efficiency and save money. The effect of signing and verification time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
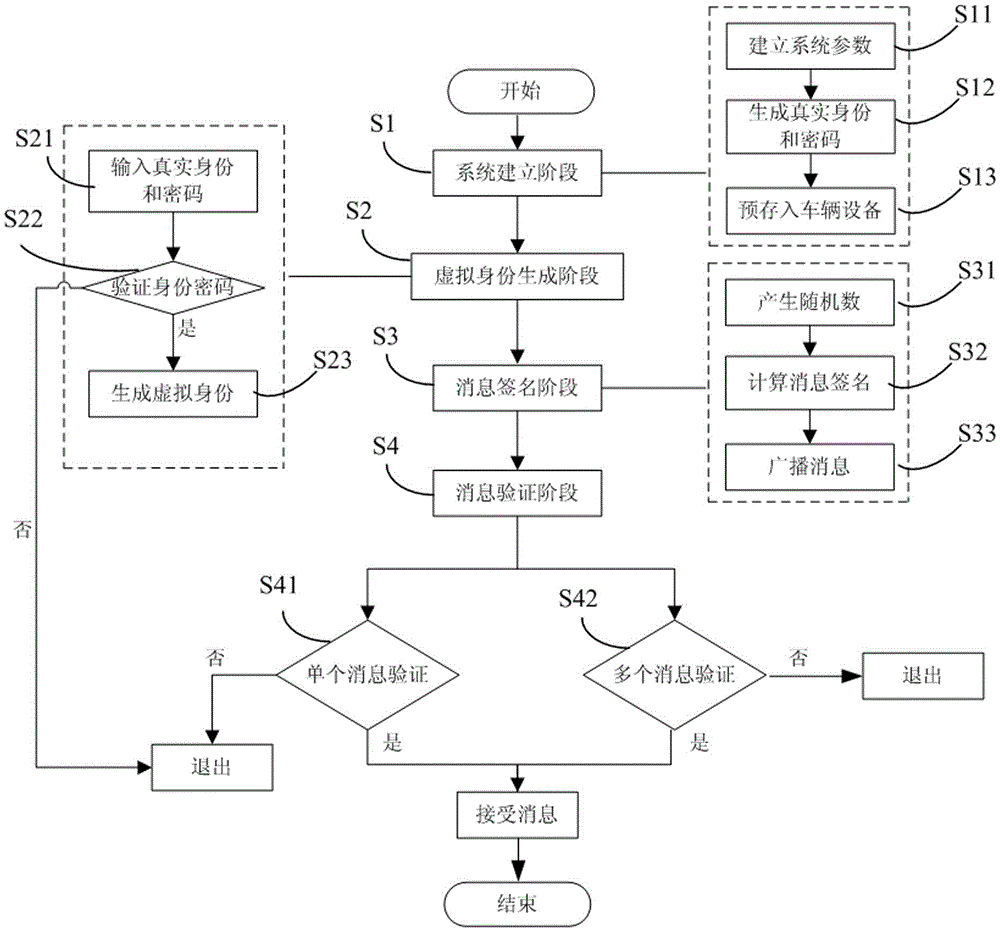
[0031] The following combination figure 1 with figure 2 , a preferred embodiment of the present invention is described in detail.
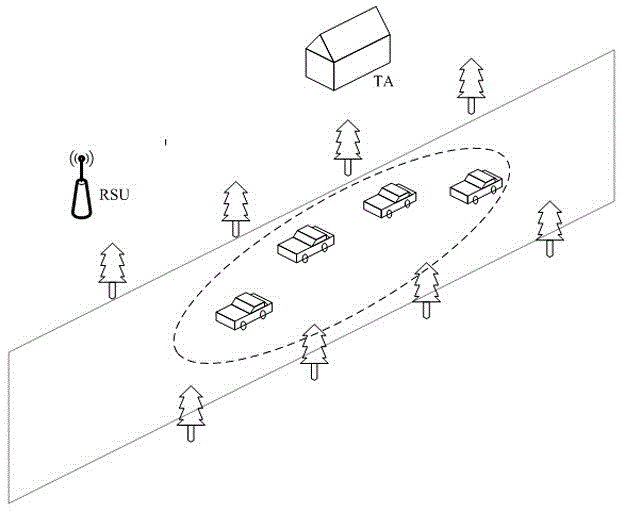
[0032] Such as figure 1 with figure 2 As shown, the privacy protection batch authentication method without pairing operation in the vehicle-mounted ad hoc network provided by the present invention includes:
[0033] S1. System establishment phase: The trusted organization TA in the vehicle ad hoc network establishes system parameters, generates a system master key, and broadcasts it to the roadside unit RSU and all vehicles; and the trusted organization TA generates a key for each vehicle A real identity and corresponding password, which is pre-stored in each vehicle together with the system master key;
[0034] S2. Virtual identity generation stage: verify the real identity and password of the vehicle to broadcast messages in the vehicle ad hoc network, and establish a corresponding virtual identity after passing;
[0035] S3. Message signin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com