SSH protocol-based session analysis method and system
An analysis method and protocol technology, which is applied in the field of computer networks, can solve problems such as poor scalability and concurrency performance to be improved, and achieve the effects of saving cache space, saving memory space, and simplifying the processing flow
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
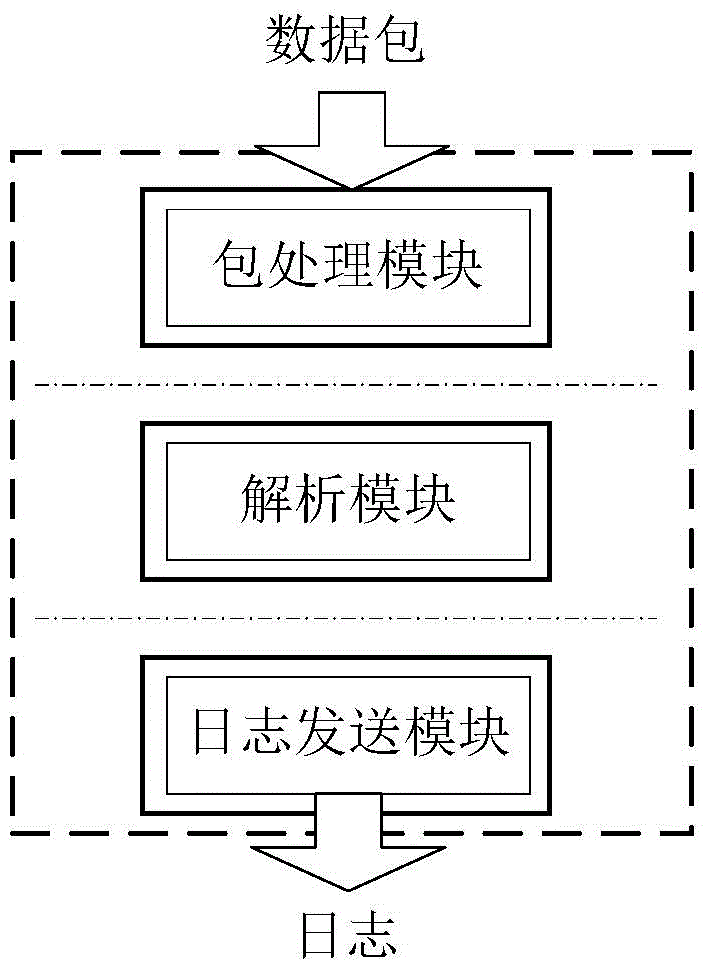
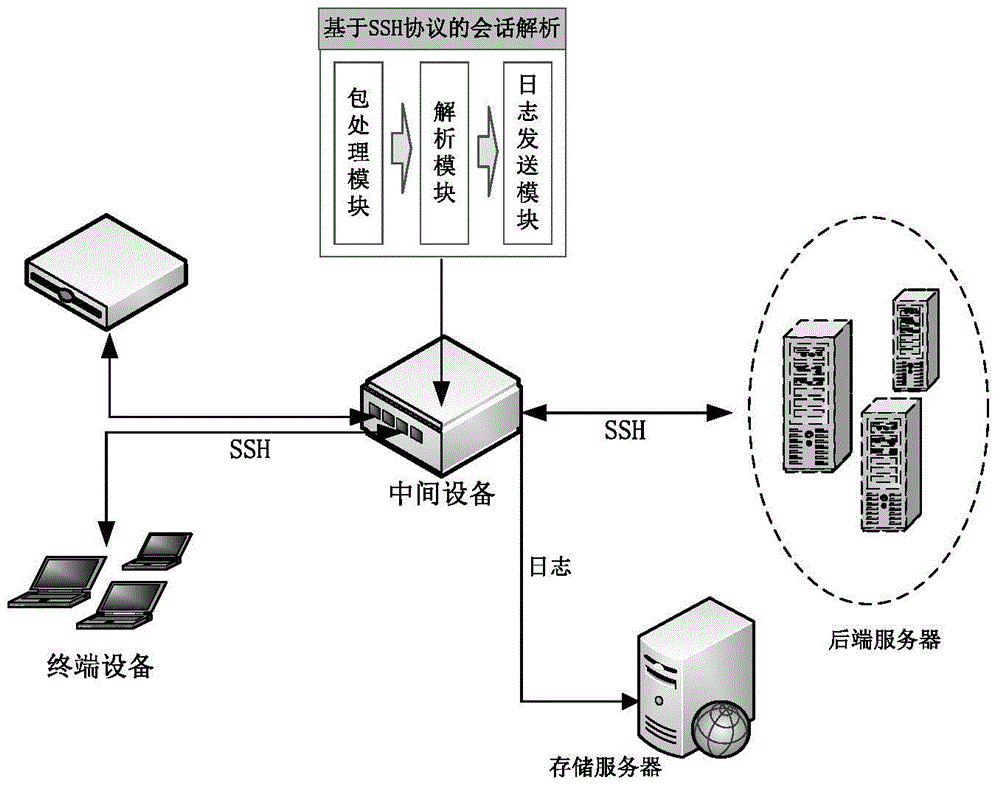
[0047] In order to realize the above method, the present invention provides an analysis system, such as Figure 1-a and 1-b as shown, Figure 1-a It is a schematic diagram of the logical structure of the three modules, Figure 1-b It is a schematic diagram of the application scene of the analysis system; the three modules involved in the present invention include: a packet processing module, an analysis module and a log sending module.
[0048]The packet processing module is used to process the received data packet. The relationship between the received data packet and the message is a many-to-many mapping, that is, it is possible that a data packet contains one or more messages, or a message may exist in Among multiple data packets, if such data packets are directly parsed, it is easy to omit the content of the message, resulting in incomplete parsing. Therefore, the data packet needs to be processed before parsing. For a data packet containing multiple messages, the message...
Embodiment 2
[0074] In order to meet the needs of some enterprises or institutions for business auditing, the present invention proposes a session parsing method based on the SSH protocol.
[0075] A kind of session parsing method based on SSH protocol provided by the present invention comprises the following steps, and what described method handles is the plain text SSH packet:
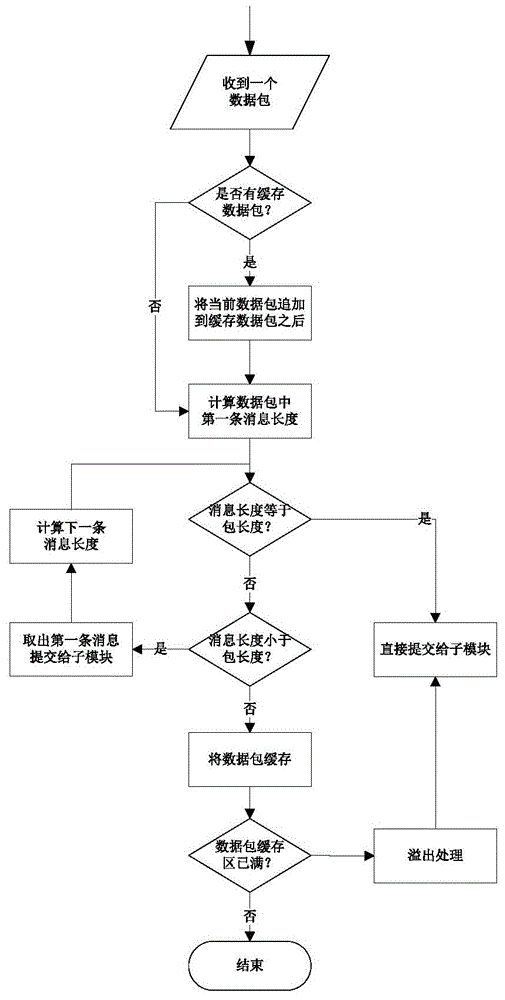
[0076] After each SSH packet arrives, it is submitted to the packet processing module. The data packet before processing may contain an incomplete message, may also contain a complete message, and may contain multiple messages. The packet processing module generates a complete message by splitting and splicing the data packet for the protocol Parse module parsing.
[0077] Among them, the process of packet splitting is actually the process of extracting messages from the packet, and using the message header address and message length to represent a message; while the process of packet splicing is realized by cac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com