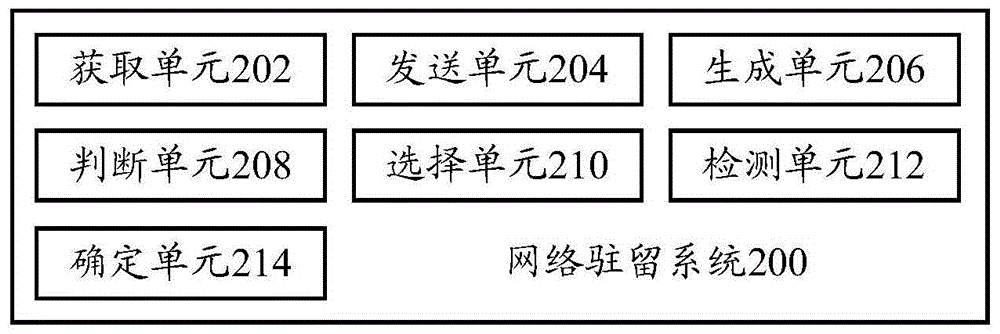
Network residing method, network residing system and terminal
A terminal and network technology, applied in the field of communication, can solve the problems of inability to judge the authenticity of the network, misleading users to stay in the terminal, and users unable to use the operator's services normally.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0104] In the 2G network, the mobile subscriber directory number (MDN, MobileDirectoryNumber) is the number dialed when the calling subscriber calls a mobile subscriber, and the IMSI (InternationalMobileSubscriberIdentification, International Mobile Station Identity) is the number that uniquely identifies a mobile subscriber in the mobile network , taking the CDMA (CodeDivisionMultipleAccess: code division multiple access communication technology) network 2G stage as an example, when the terminal is powered on and registered, the CAVE algorithm is used, and the parameters IMSI, ESN (UIMID), SSD-A (shared encrypted data) and RAND (random data) are entered. ), calculate AUTHR (calculation result). The terminal sends registration signaling, including authentication data: RAND, AUTHR. Among them, the CAVE algorithm is a cellular authentication and voice encryption (CellularAuthenticationVoiceEncryption) algorithm, which is an authentication encryption algorithm authorized by a CDM...
Embodiment 2
[0106] After entering the 3G evolution stage, there are two different technical routes for 3G evolution, one is 1xEV-DO (EvolutionDataonly: the first stage of CDMA2000 evolution), the other is 1xEV-DV (EvolutionDataandVoice: the second stage of CDMA2000 evolution), 1xEV-DO The access authentication method adopts the CHAP (Challenge Handshake Authentication Protocol) authentication based on the MD5 (Message Digest5) algorithm, and a new authentication device is added in the 1xEV-DO network to support the MD5 algorithm.
Embodiment 3
[0108] After entering the LTE (LongTermEvolution, long-term evolution) 4G era, the authentication vector includes RAND (a 128-bit random number), XERS (a 64-bit expected response), AUTH (authentication token), KASME (access security management entity K value), using the Milenage algorithm based on AES-128 cyclic shift + XOR to realize the authentication process.
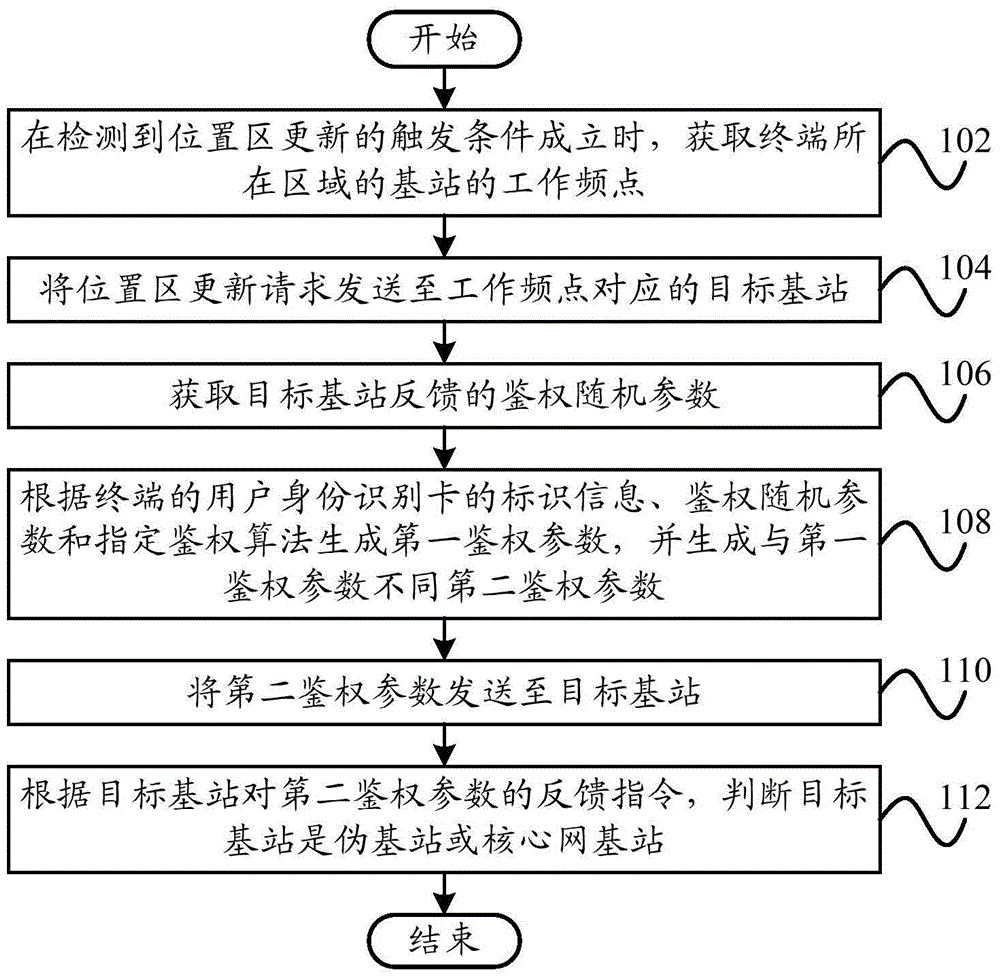
[0109] Figure 6 A schematic flowchart of a network residency solution according to an embodiment of the present invention is shown.
[0110] Such as Figure 6 As shown, the network residency scheme according to the embodiment of the present invention: step 602, the terminal searches for the operating frequency point of the base station after powering on; step 604, sends the location area update request to the target base station; step 606, obtains the authentication information fed back by the target base station Authorization random parameter; Step 608, generate the first authentication parameter according to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com