Android malicious act detection method based on Bayesian network
A technology of Bayesian network and detection method, which is applied in the field of Android malicious behavior detection, and can solve problems such as user threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be described in further detail below in conjunction with accompanying drawing
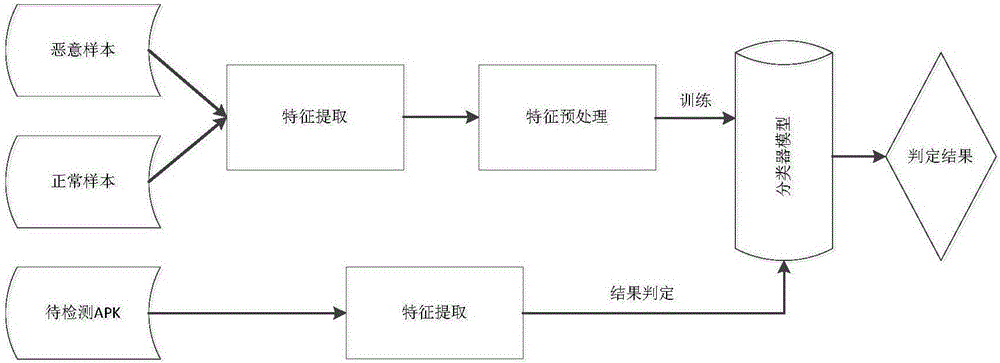
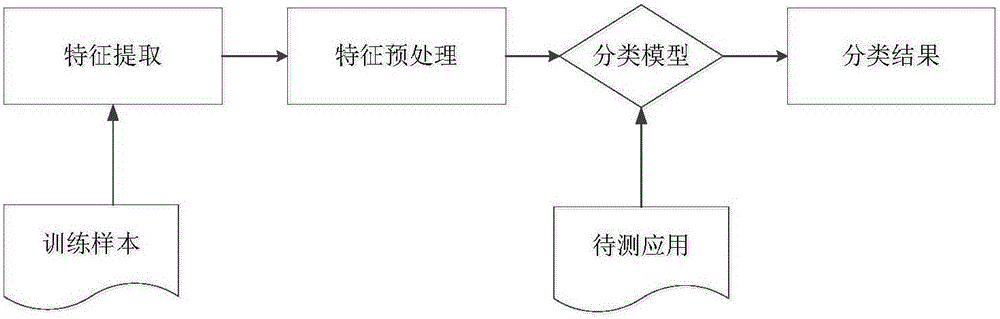
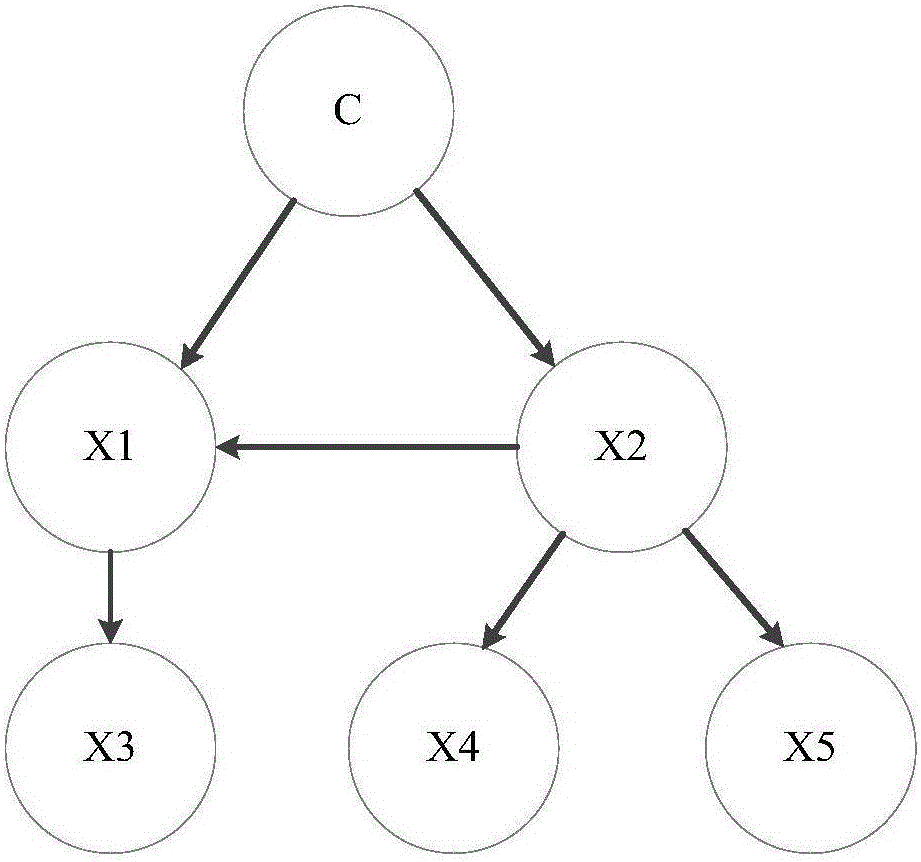
[0042] The invention uses a static analysis method to detect the virus program on the Android platform. The static analysis method mainly obtains the static behavior characteristics of the APK through decompilation technology, and does not actually run the application program. The present invention extracts the characteristics of Android software training samples through static analysis, and then uses data mining technology to dig out the potential relationship between various information, and automatically discovers the laws existing in the sample data by analyzing the sample data, and utilizes the learned predict the unknown data. Machine learning is an important branch of data mining. The purpose of machine learning is to build a model with a better virus detection program based on existing sample data. The purpose of the present invention is to establish a goo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com