Method for accessing shared memory
A shared memory, visitor technology, applied in specific access rights, inter-program communication, instruments, etc., can solve data security and data consistency issues, access efficiency bottlenecks and other issues, to ensure security and consistency, ensure The effect of accessing efficiency and avoiding efficiency loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
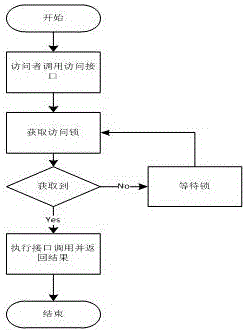
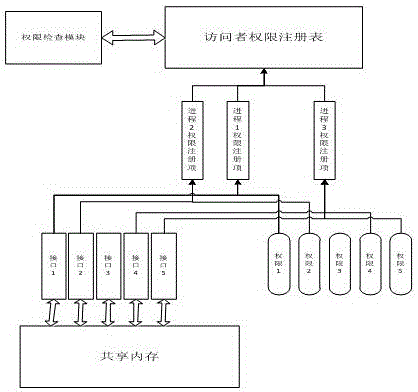
[0029] Embodiment 1, the present embodiment is a kind of method that shared memory is accessed, and in this method, by initializing program, establishes an authority registry for each visitor in shared memory in advance, records the access authority of shared memory, as: Define read / write permissions.
[0030] Shared memory operation (retrieval / storage, etc.) interface, such as: define the read interface / write interface.
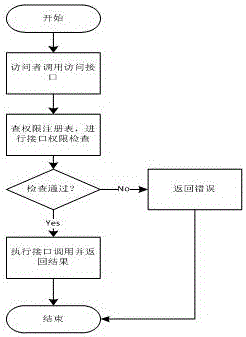
[0031] The authority registration list of each accessor specifies the access authority of each process in the list.
[0032] Visitor permission checking and access control. Control the access behavior of visitors according to the permissions granted by the permission registration list. Visitors can only perform authorized access operations and call corresponding operation interfaces; when visitors perform unauthorized operations or call unauthorized access interfaces, corresponding errors will be returned.
[0033] There are many ways to implement the acc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com