System, method and device for acquiring user portrait information
A user and portrait technology, applied in the network field, can solve the problem of high network security risk and achieve the effect of reducing network security risk
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] Embodiment 1: Introduced from the perspective of the overall system.
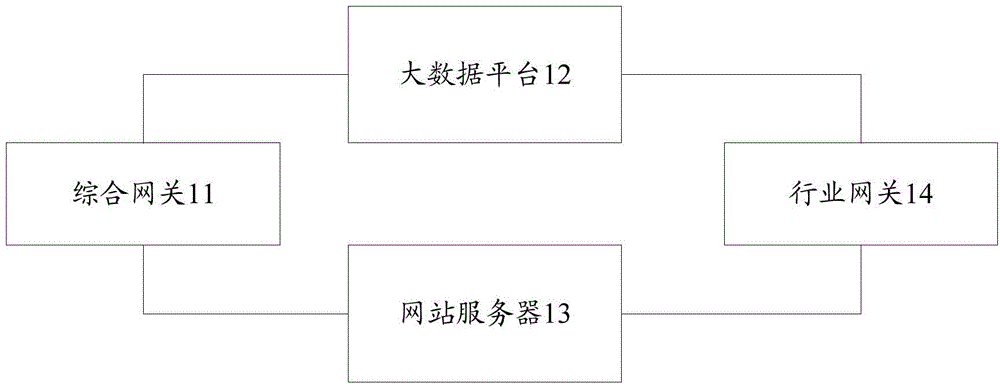
[0032] Such as figure 1 As shown, it is a schematic structural diagram of the user portrait information acquisition system provided by Embodiment 1 of the present invention, including:
[0033] The integrated gateway 11 is used to generate a service flow identifier for a user who needs to visit a website, send the service flow identifier and the user identification information of the user to the big data platform, and send the service flow identifier containing the service flow identifier to the website server. A website access request message, which does not contain user identification information;
[0034] The big data platform 12 is configured to, after receiving the service flow identification and the user identification information of the user sent by the integrated gateway 11, find out the user portrait information corresponding to the user identification information, and store the service flo...
Embodiment 2
[0055] Embodiment 2 is introduced from the method perspective of the corresponding system.
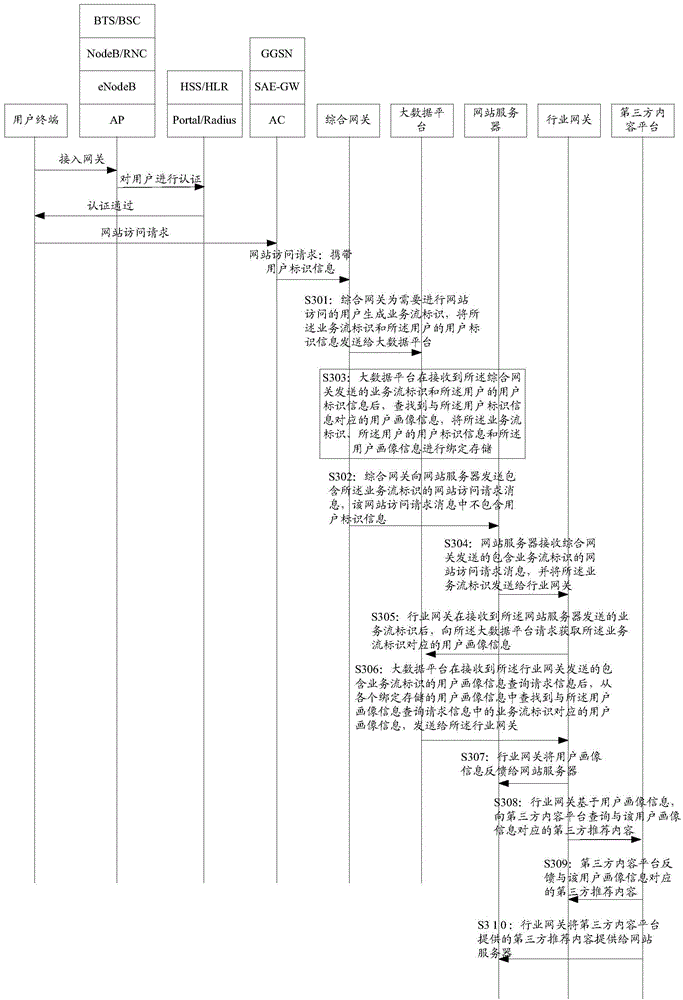
[0056] Such as image 3 As shown, it is a flow chart of the user portrait information acquisition method provided in Embodiment 2 of the present invention, including:
[0057] S301: The integrated gateway generates a service flow identifier for a user who needs to visit a website, and sends the service flow identifier and user identifier information of the user to the big data platform.
[0058] S302: The integrated gateway sends a website access request message including the service flow identifier to the website server, and the website access request message does not include user identification information.
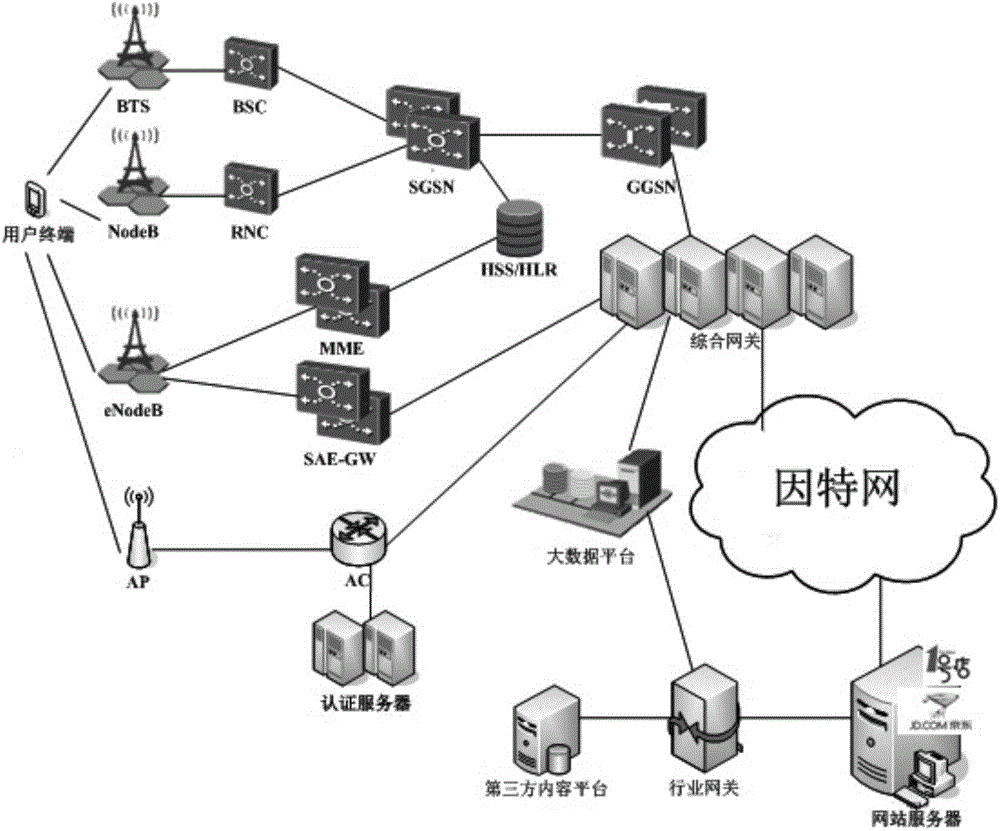
[0059] Such as image 3 As shown in the flow, before S301, the user terminal first sends an access request to various access devices (BTS / BSC in 2G, NodeB / RNC in 3G, eNodeB in 4G, AP in WLAN), and the access device indicates The authentication device (HSS / HLR in the 2 / 3 / 4G ne...
Embodiment 3
[0068] Embodiment 3 and Embodiment 4 are introduced from the integrated gateway side.
[0069] Such as Figure 4 As shown, it is a flow chart of the user portrait information acquisition method provided by Embodiment 3 of the present invention, including:
[0070]S401: The integrated gateway generates a service flow identifier for the user who needs to visit the website;
[0071] S402: The integrated gateway sends the service flow identifier and the user identifier information of the user to the big data platform, and sends a website access request message including the service flow identifier to the website server, and the website access request message does not include Contains user identification information;
[0072] Wherein, the service flow identifier is used to obtain the user portrait information corresponding to the service flow identifier from the big data platform; Portrait information is bound and stored.
[0073] Optionally, in S401, the integrated gateway gen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com