Hard disk firmware attack preventing system and method
A hard disk and firmware technology, applied in the field of information security, to achieve the effect of a wide range of firmware attack behavior characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the accompanying drawings and preferred embodiments.
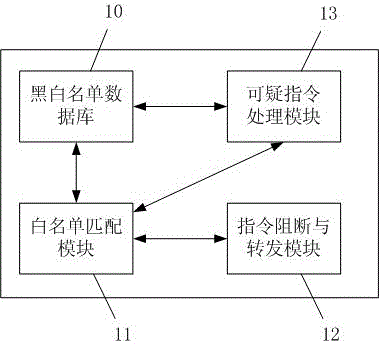
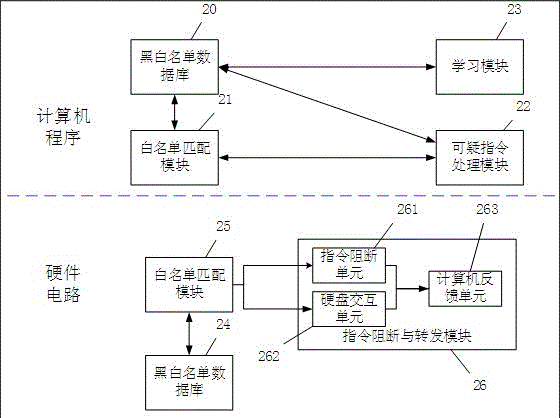
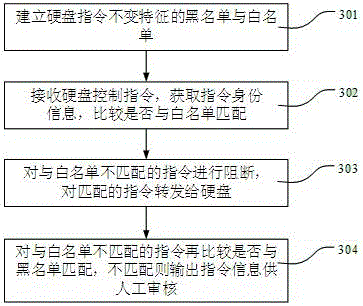
[0027] Such as figure 1 Shown is a schematic diagram of the system structure of the present invention. include:
[0028] The black and white list database 10 stores the blacklist and whitelist of the invariant characteristics of the hard disk instructions; the whitelist matching module 11 receives the hard disk control instructions sent by the computer, obtains the instruction identity information of the received instructions, and compares the instruction invariant characteristics of the above-mentioned instructions Whether it matches the invariant feature of the instruction in the whitelist; the instruction blocking and forwarding module 12 is connected with the whitelist matching module 11, and directly returns the result data to the computer for the above-mentioned unmatched hard disk control instruction, and directly returns the result da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com