City intelligent transportation shared payment and identity safety certification method
A technology for intelligent transportation and security authentication, applied in payment architecture, time register, instruments, etc., can solve the problems of patent application and application technology disclosure that have not solved similar technical problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
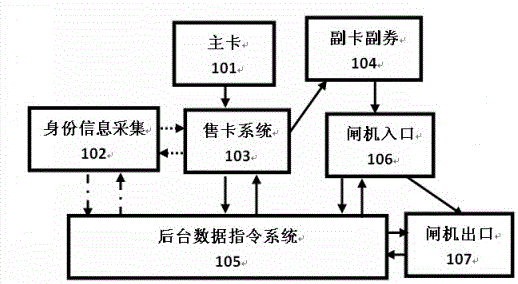
[0034] Embodiment 1 has the following business implementation steps:
[0035] Read the main card information and pre-stored amount, or further remind the main card pre-stored amount to authorize the number of one-time-use supplementary card and auxiliary coupons, and remind the main card user if the number of accompanying persons is enough to swipe all on their behalf.
[0036] Set the number of supplementary cards and supplementary coupons. After confirmation, the user will obtain the used supplementary card and supplementary coupons.
[0037] When the shared card vending system is integrated with the gate, the gate will start to release the users of the secondary card and the secondary coupon through the gate.
[0038] When the shared card vending system is set separately from the gate, the gate will read the information of the auxiliary card and the auxiliary coupon to confirm that it is valid, and then start to release the user of the auxiliary card and auxiliary coupon th...
Embodiment 2
[0042] The second embodiment has the following business implementation steps:
[0043] Read the information of the supplementary card and the supplementary coupons to confirm that the pre-stored limit of the main card is valid.
[0044] When the balance of the main card is less than the minimum set limit value, it may prompt that it cannot be used, or further prompt the user of the one-time supplementary card and supplementary coupon to select the destination to determine that it is within the valid balance value.
[0045] The gate is activated to release the secondary card and secondary coupon users through the gate.
[0046] After the user of the supplementary card and supplementary coupon arrives at the station, the gate reads the information of the supplementary card and supplementary coupon.
[0047] After the background system confirms that the payment is deducted from the main card, it starts to release the users of the supplementary card and supplementary coupons thro...
Embodiment 3
[0048] The third embodiment has the following business implementation steps:
[0049] Read the pre-stored amount of the main card, and the user submits fingerprints or ID documents for reading; or further submits it to the back-end system for security identification and authentication. When it is judged to be a normal information person, the front-end is instructed to output a supplementary card and a supplementary coupon; when it is judged to be a blacklist information person, The alarm is activated.
[0050] The user obtains the supplementary coupon for the supplementary card; or after the authorization of the main card is activated, the user obtains the supplementary coupon for the supplementary card.
[0051] When the shared card vending system and the turnstile are set together, the turnstile starts to release the auxiliary card and auxiliary coupons using the user to pass through the gate; when the shared card vending system and the turnstile are set separately, the turn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com