Voice encryption system based on smartphone and realization method thereof
A technology for voice encryption and smartphones, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as increased user costs and inconvenience for users, and achieve the effects of increased additional costs, high security levels, and guaranteed useability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
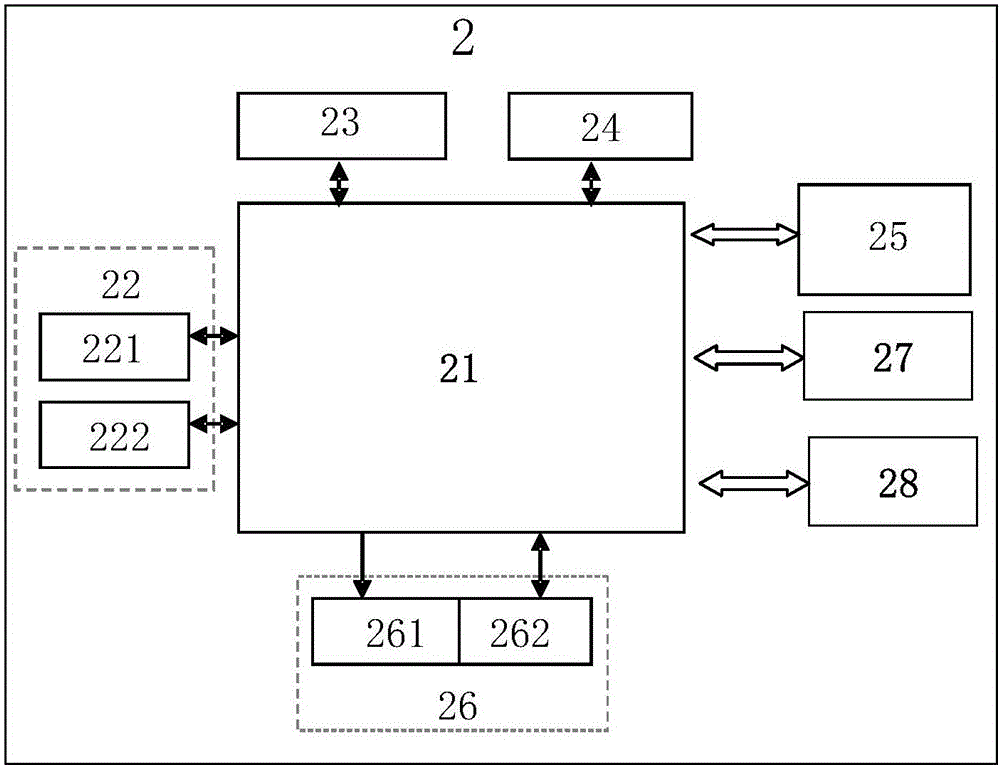
[0051] Embodiments of the present invention provide a smart phone-based voice encryption system, see figure 1 , the voice encryption system includes: a password module 1 and a voice communication device 2.
[0052]Wherein, the cryptographic module 1 adopts common commercial cryptographic algorithms such as SHA1, SHA-256, RSA1024, RSA2048, DES, and AES algorithms. The cryptographic module 1 provides encryption and decryption application operations for data, realizes key management, and ensures the validity and security of keys.
[0053] Voice call device 2 includes: system control module 21, user account management module 22, call record management module 23, local information management module 24, data sending and receiving module 25, voice control module 26, user interface control module 27 and user setting management module 28.
[0054] The system control module 21 realizes data communication with the password module 1; the system control module 21 realizes data communicat...
Embodiment 2
[0068] Embodiments of the present invention provide a method for implementing a voice encryption system based on smart phones, see the following description for details:
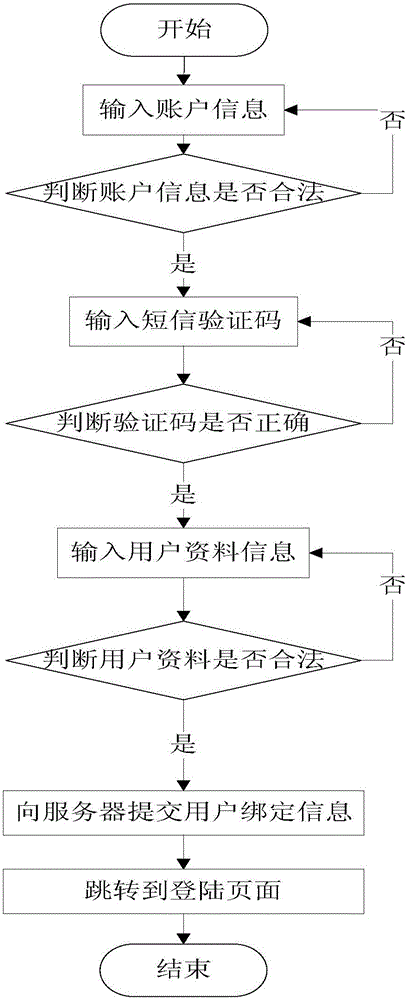
[0069] see figure 1 and image 3 , the process of binding the user account of the voice encryption system in the present invention is: the system control module 21 realizes the input of the user account by calling the user interface control module 27, calls the account binding module 221 to judge the legitimacy of the user account input, calls the account binding Fixed module 221 sends verification short message to user account by server, calls user interface control module 27 to realize the input of short message verification code, calls account binding module 221 to judge the correctness of the short message verification code of input, realizes by calling user interface module 27 User information input, call the account binding module 221 to judge the validity of the input user information, call the data ...
Embodiment 3
[0087] Embodiments of the present invention provide a method for implementing a voice encryption system based on smart phones, see the following description for details:
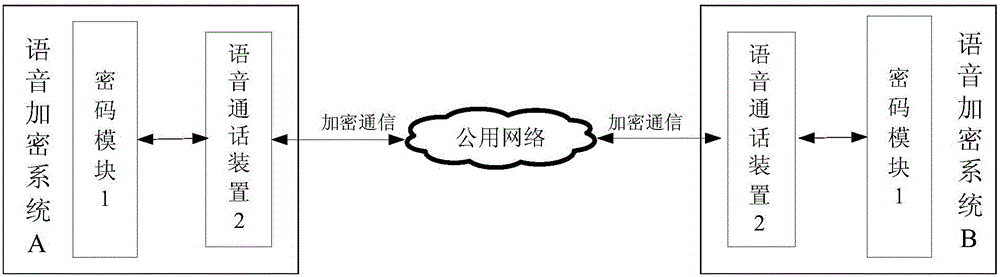
[0088] In actual application, the function of encrypted voice calls is realized through two sets of voice encryption systems. The voice encryption system A is used as the calling party, and the voice encryption system B is used as the called party as an example to illustrate the encrypted voice call process. The system control module 21 of the voice encryption system A is marked as the first system control module, and the system control module 21 of the voice encryption system B is marked as the second system control module. The data sending and receiving module 25 of the voice encryption system A is marked as the first data sending and receiving module, and the data sending and receiving module 25 of the voice encryption system B is marked as the second data sending and receiving module. The encryption modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com