Network session statistical characteristic based large-scale network scanning detection method
A statistical feature and network session technology, applied in the field of Internet security, to achieve the effect of automatic detection function, high efficiency, and resource saving
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described in detail below in conjunction with accompanying drawings and examples.
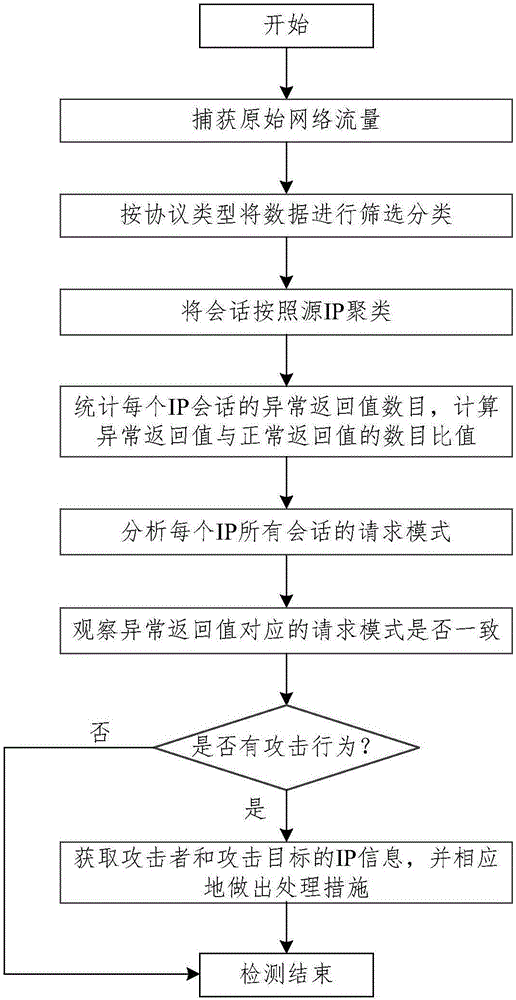
[0027] The present invention summarizes the behavior characteristics of hackers scanning for different protocols through analysis, and focuses attention on the return value and request mode in the traffic. Aiming at these two points, a large-scale scanning detection method based on the statistical characteristics of network sessions is proposed. By comparing the definition of the abnormal return value with the request mode, it is judged whether the traffic conforms to the characteristics of the attack behavior, so as to identify the possible attack behavior. At the same time, the characteristics reflected in the request time of network scanning are added to the detection mechanism, which improves the accuracy of the analysis results.
[0028] Firstly, the captured raw traffic is classified according to the network protocol, and then the attack chara...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com