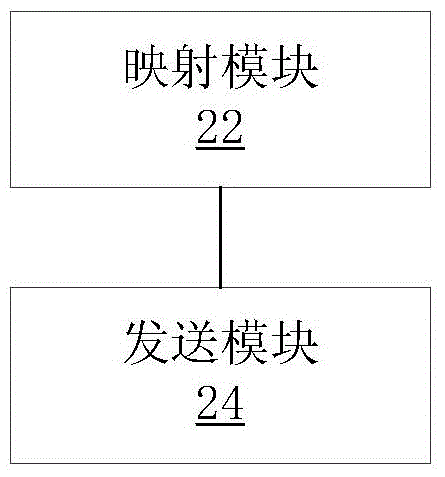
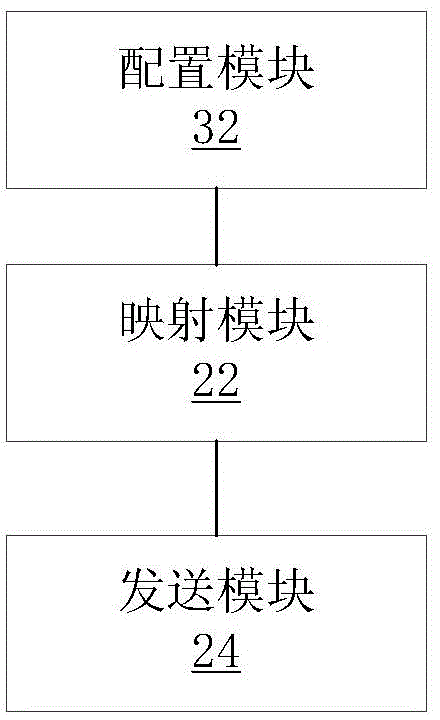
Method and device for sending access control list (ACL)
An access control list and sending method technology, applied in the field of communication, can solve the problem of very high performance requirements of network equipment, and achieve the effect of reducing upgrade and maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
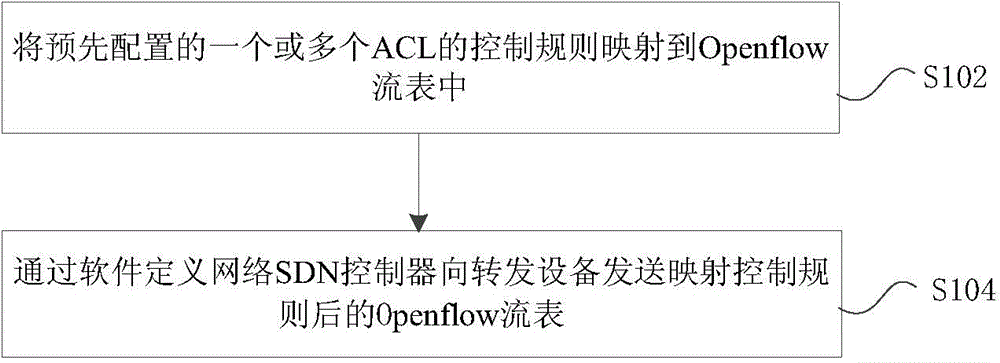
[0060] Embodiment 1: ACL rules with time period characteristics are involved, and complex ACL time period characteristics are placed in the ACL application server for processing; the steps of the SDN-based access control list implementation method include:
[0061] Step S202: configure the ACL through the man-machine interface provided by the ACL application;
[0062] Wherein, the configuration name may be the ACL of TEST, and the ACL number assigned to TEST by the ACL application is 1.
[0063] Step S204: configuring ACL rules;
[0064]Among them, you can configure an ACL rule with time period characteristics in TEST. The rule defines that packets with source IP address 192.168.1.12 are allowed to be forwarded from 9:00 to 17:00 every day, and packets with source IP address 192.168.1.12 are prohibited from being forwarded at other times.
[0065] Step S206: the ACL application processes the time period characteristics of each ACL rule;
[0066] Among them, when the time is ...
Embodiment 2
[0068] Embodiment 2: involves merging ACL rules; the ACL application server simplifies the implementation complexity of the forwarding device and maintains the versatility of the forwarding device by processing complex, proprietary ACL rule merging algorithms and saving the original ACL configuration data . After the merging process, the number of flow entries sent to the forwarding device is reduced, saving the storage space of the flow table of the forwarding device. The steps of the method include:
[0069] Step S302: configure the ACL through the man-machine interface provided by the ACL application.
[0070] The ACL named TEST is configured, and the ACL number assigned to TEST by the ACL application is 1.
[0071] Step S304: configuring ACL rules;
[0072] Among them, two ACL rules are configured in TEST. Rule 1 defines that packets whose source IP address belongs to network segment 192.168.0.0 (mask 255.255.255.0) are prohibited from being forwarded, and rule 2 define...
Embodiment 3
[0076] Embodiment 3: ACL associated with the port; multiple ACLs can exist on each forwarding device, and different ACLs are applied in different occasions. The ACL rules in different ACLs are allowed to be the same, and multiple rules in each ACL match priority. According to the requirements of these basic ACL functions, Openflow technology can be used to combine multiple ACLs into one flow table. Each ACL rule corresponds to a flow entry. Write the ACL number in the metadata (metadata) to achieve. The matching sequence requirements for multiple ACL rules are implemented by setting different priorities for flow entries. The steps of the method include:
[0077] Step S402: configure the ACL through the man-machine interface provided by the ACL application;
[0078] Among them, configure the ACL named TEST1, the ACL number assigned to TEST1 by the ACL application is 1, configure the ACL named TEST2, and the ACL number assigned to TEST2 by the ACL application is 2;
[0079] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com