Wireless network access method
A wireless network access, wireless network technology, applied in the direction of access restriction, wireless communication, electrical components, etc., can solve problems affecting network experience and security, technical insufficiency, troublesome use, etc., to prevent network security problems, The effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
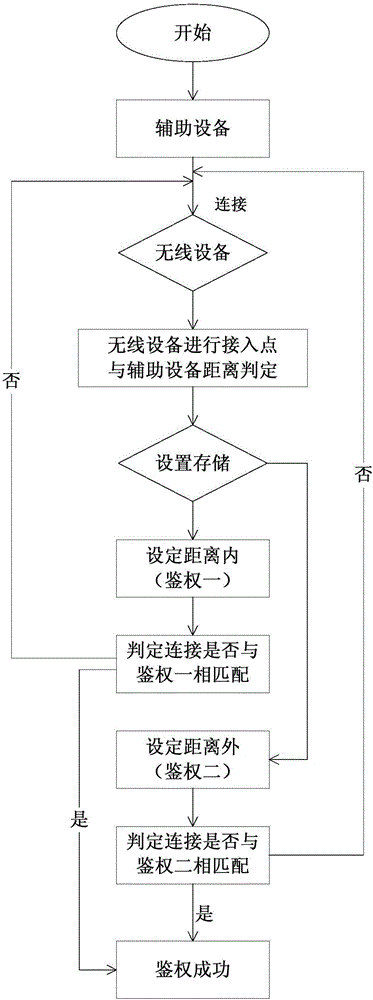
[0027] The steps for changing the network authentication method include:
[0028] The auxiliary device searches for the SSID name of the wireless device, and enters the authentication to connect.
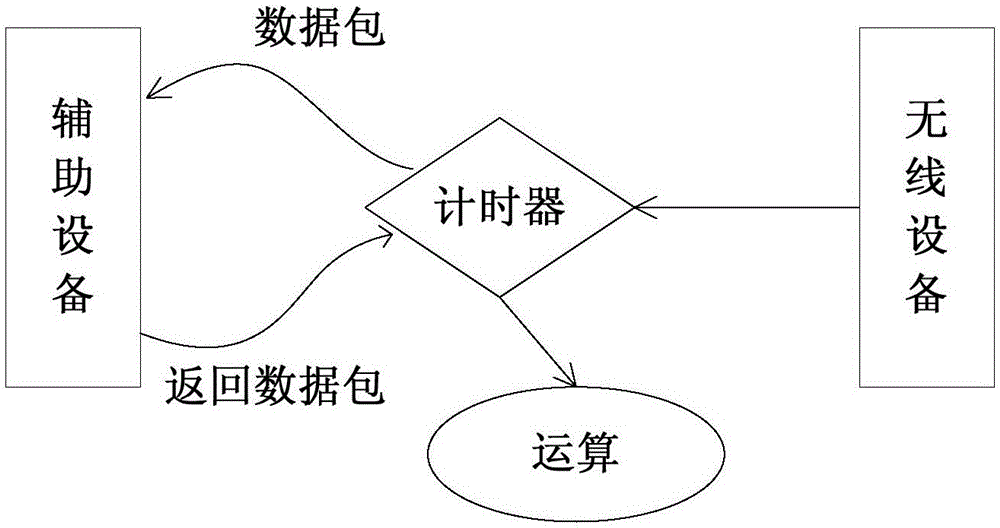
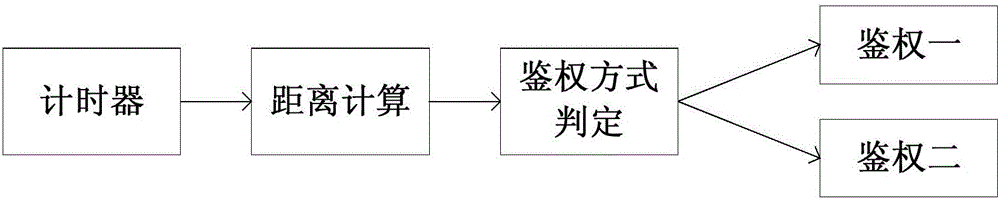
[0029] The wireless device determines the distance between the access point and the auxiliary device, and obtains the distance between the two. In the process of distance determination, the wireless device transmits data packets to the auxiliary device and starts the timer. After the auxiliary device receives the data packet, it returns the data packet. After the wireless device receives the data packet, the timer stops. The distance between the transmission time and the transmission speed of the data packet is calculated.
[0030] The obtained distance is compared with the set distance stored in the wireless device to determine which way to access. It is concluded that the distance between the auxiliary device and the wireless device is within the set distance, then the authentication m...
Embodiment 2
[0036] The steps for changing the network authentication method include:
[0037] The auxiliary device searches for the SSID name of the wireless device, and enters the authentication to connect.
[0038] The wireless device determines the distance between the access point and the auxiliary device, and obtains the distance between the two. In the process of distance determination, the distance between the auxiliary device and the wireless device is calculated by the signal attenuation of the RSSI propagating in the air and the transmission medium.
[0039] The obtained distance is compared with the set distance stored in the wireless device to determine which way to access. It is concluded that the distance between the auxiliary device and the wireless device is within the set distance, then the authentication method matching judgment is performed to determine whether the connection and the authentication one match, if they match, the authentication succeeds, and if they do not matc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com