Prepayment method, system, terminal and server
A prepaid, terminal technology, applied in prepaid schemes, transmission systems, digital transmission systems, etc., can solve the problems of low flexibility and reliability, and achieve the effect of improving flexibility and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0067] figure 1 The implementation process of the prepayment method provided by this embodiment is shown. For the convenience of description, only the parts related to this embodiment are shown, and the details are as follows:
[0068] In step 101, a password array is generated according to the password seed and an iterative algorithm, and the last element of the password array is sent to the terminal as a verification password, and the number of elements of the password array is a preset value.
[0069] In specific implementation, step 101 may specifically be: generating a password array according to the password seed and an iterative algorithm in step A1, and sending the last element of the password array to the terminal as a verification password, specifically:
[0070] Generate the first element in the password array according to the hash algorithm and the password seed, iteratively generate other elements of the password array according to the hash algorithm, and send the...
Embodiment 2
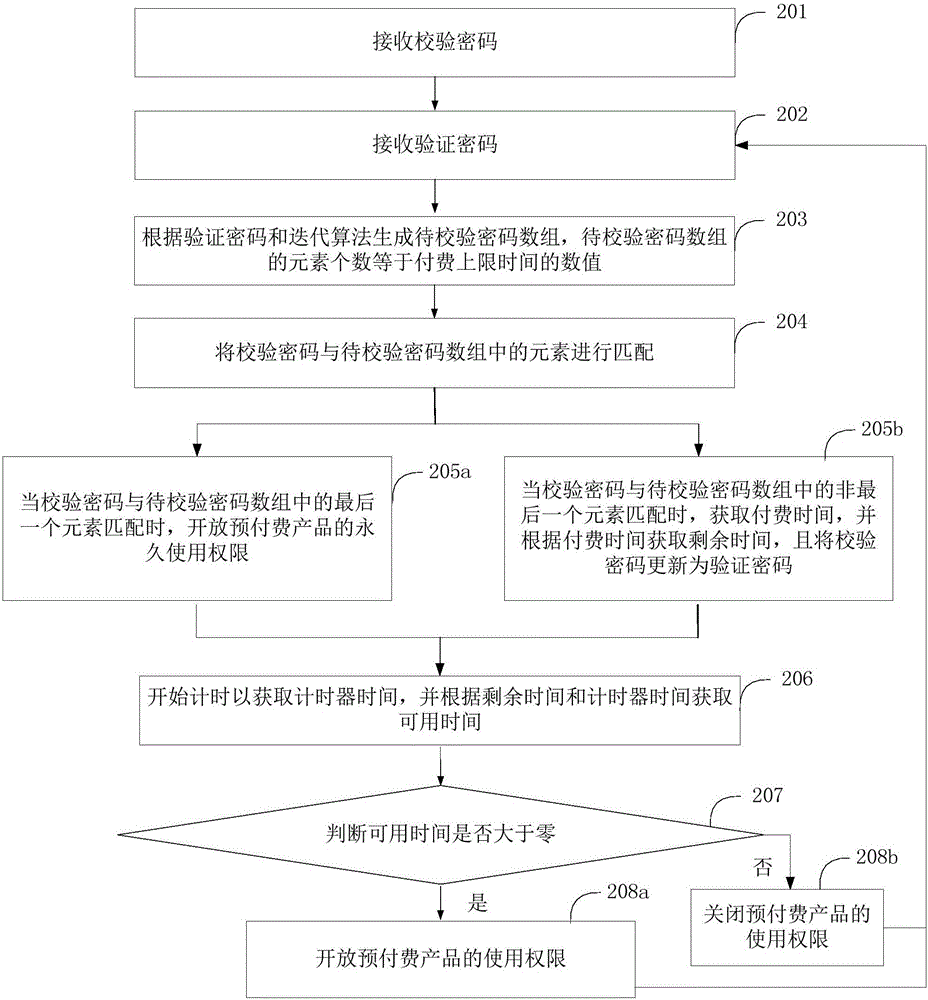
[0091] figure 2 The implementation process of the prepayment method provided by this embodiment is shown. For the convenience of description, only the parts related to this embodiment are shown, and the details are as follows:
[0092] In step 201, a verification password is received.
[0093] In step 202, a verification password is received.
[0094] In step 203, an array of passwords to be verified is generated according to the verification password and an iterative algorithm, and the number of elements in the array of passwords to be verified is equal to the value of the payment upper limit time.
[0095] In a specific implementation, step 203 further includes: receiving a payment upper limit time.
[0096] In step 204, the verification password is matched with elements in the array of passwords to be verified.
[0097] In step 205a, when the verification password matches the last element in the array of passwords to be verified, the permanent use right of the prepaid p...
Embodiment 3
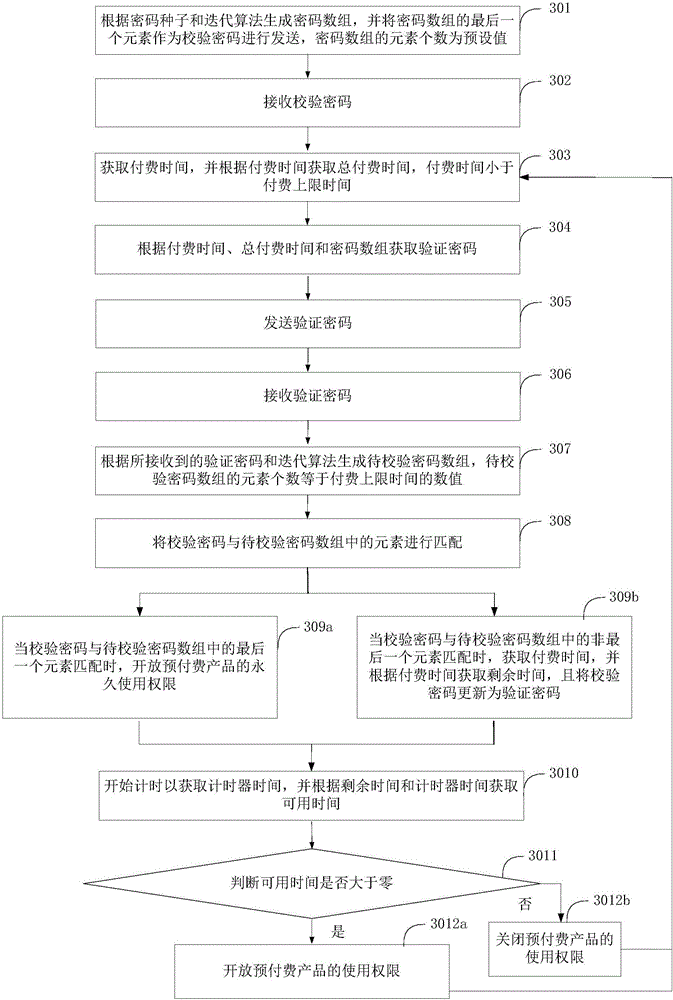
[0113] image 3 The implementation process of the prepayment method provided by this embodiment is shown. For the convenience of description, only the parts related to this embodiment are shown, and the details are as follows:
[0114] In step 301, a password array is generated according to the password seed and an iterative algorithm, and the last element of the password array is sent as a verification password, and the number of elements of the password array is a preset value.
[0115] In a specific implementation, generating a password array according to the password seed and an iterative algorithm in step 301, and sending the last element of the password array as a verification password may be specifically: generating the password array according to the hash algorithm and the password seed The first element generates other elements of the password array iteratively according to the hash algorithm, and sends the last element of the password array as the verification passwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com