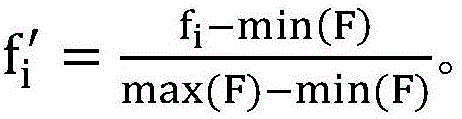Privacy protection method and system for bypass attacks in smart home environment
A smart home, bypass attack technology, applied in the field of privacy protection, can solve the problems of user leakage, reducing the effect of privacy protection, and interfering with the real behavior of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
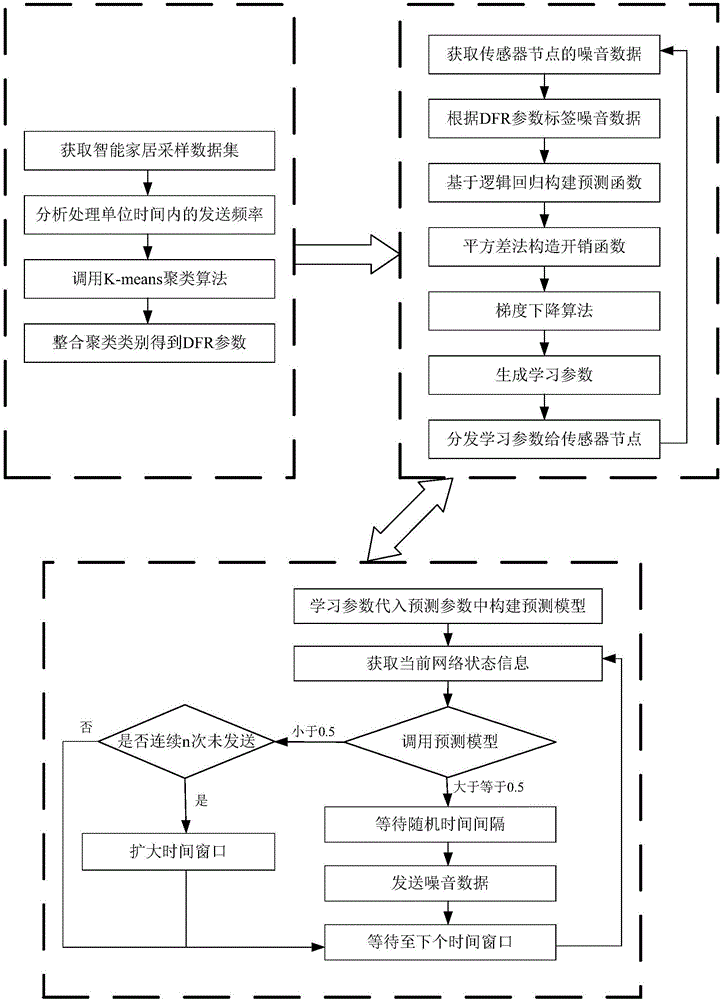
[0095] Embodiment 1: as figure 1 As shown, the present invention provides a privacy protection method to deal with side-channel attacks in smart home environment, ①, analyze the data: analyze and collect sample data, and the analysis results will be used to guide the aggregation node label noise data; ②, semi-supervised learning : The aggregation node labels the noise data sent by the sensor nodes, and then calls the learning algorithm to learn to generate new learning parameters; ③. The sensor node user substitutes the learning parameters into the prediction model, and judges whether to send noise data according to the current network status. Its specific implementation process includes:
[0096] Step 1. Considering that people's living habits in different regions will be different, smart home suppliers extract sample data according to users in different geographical locations, where sample data refers to data generated by real smart home scenarios; sensor nodes obtain smart ...
Embodiment 2
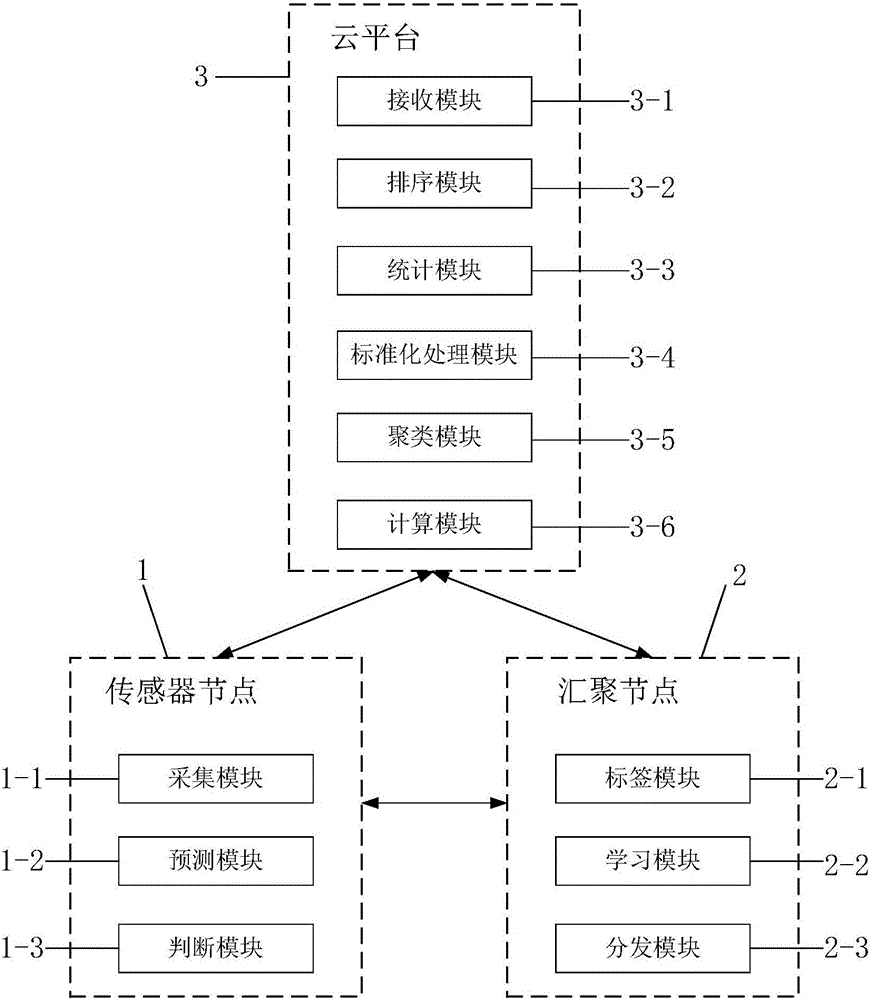
[0131] Embodiment 2: as figure 2 As shown, the present invention provides a privacy protection system for dealing with bypass attacks in a smart home environment, including: a plurality of sensor nodes 1, a convergence node 2 and a cloud platform 3;
[0132] The sensor node 1 includes an acquisition module 1-1, a prediction module 1-2 and a judgment module 1-3; the acquisition module 1-1 is used to obtain sampling data, noise data and current network status information of the smart home for subsequent operations; Data includes sensor type and sensor send time;
[0133] The cloud platform 3 is connected to all sensor nodes 1, and is used to sort the sensor types and sensor sending times, cluster the sending frequency of each type of sensor in unit time, and calculate the average sending frequency of each cluster category, Get the DFR parameters; where:
[0134] Cloud platform 3 includes receiving module 3-1, sorting module 3-2, statistical module 3-3, standardization process...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com