Hacking defending implementation method and device
An implementation method and a technology of the number of logins, applied in the field of network security, can solve the problems of reduced accuracy of account theft detection, poor network security, and inability to effectively detect account theft behavior, so as to improve security reliability, improve accuracy, and avoid defense failures. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
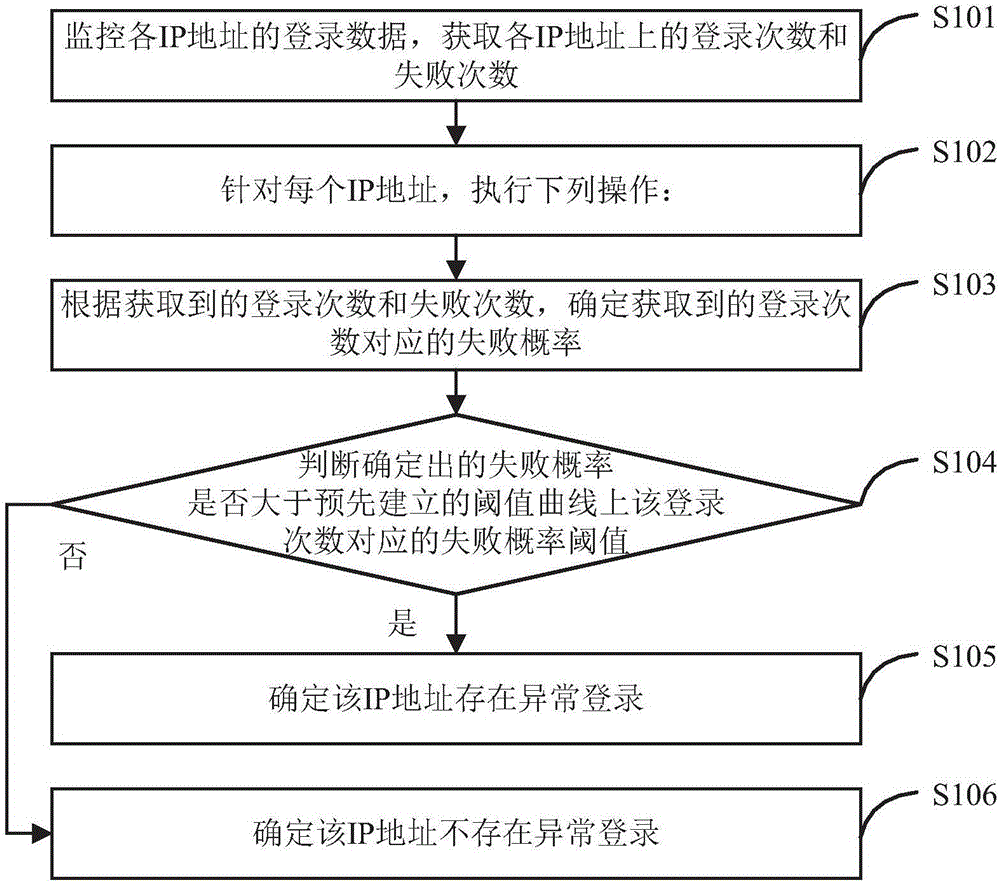
[0053] The implementation method of account hacking defense provided by Embodiment 1 of the present invention, its flow is as follows figure 1 shown, including the following steps:
[0054] Step S101: Monitor the login data of each IP address, and obtain the login times and failure times of each IP address.
[0055] By monitoring the login data of each IP address, and counting the number of login times and failure times, it is possible to monitor whether the login behavior is abnormal. The reasons for the login failure may include the user does not exist, the password is wrong, and remote login, etc.
[0056] The number of failures can also be the number of exceptions, and the login exceptions can include login failures and login successes but exceptions.
[0057] Step S102: For each IP address, perform the following operations:
[0058] Step S103: According to the obtained number of logins and the number of failures, determine the probability of failure corresponding to th...
Embodiment 2
[0070] The implementation method of account hacking defense provided by Embodiment 2 of the present invention, its process is as follows image 3 shown, including the following steps:
[0071] Step S301: Obtain the login log of the system.
[0072] The login logs of the system can come from various login behaviors of the user through the terminal device, and the login logs within a certain period of time or a certain number of login logs can be obtained.
[0073] Step S302: Establish a threshold curve representing the corresponding relationship between the number of login times and the failure probability threshold according to the login log.
[0074] When establishing the threshold curve, first determine several eigenvalues, and then fit the threshold curve according to the eigenvalues. Specifically, according to the obtained login log, determine the characteristic value of establishing the threshold curve; wherein, the characteristic value includes the characteristic value...
Embodiment 3
[0085] Embodiment 3 of the present invention provides an implementation process for establishing the threshold curve of the above-mentioned method for implementing defense against hacking, and its flow is as follows Figure 4 shown, including the following steps:
[0086] Step S401: Obtain the login log of the system.
[0087] Step S402: According to the obtained login log, determine the characteristic value of establishing the threshold curve. Wherein, the eigenvalues include the eigenvalues of the login times and the corresponding eigenvalues of the failure probability.
[0088] The characteristic value for establishing the threshold curve can be determined according to the login log, and the update can be dynamically adjusted when the login log is updated.
[0089] The process of determining the eigenvalues involves:
[0090] Count the number of failed logins and logins for each IP address in the login logs obtained;
[0091] Sort according to the number of fail...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com