Peripheral device, authorized device, peripheral device management method and system
A technology for authorized equipment and peripheral management, applied in connection management, wireless communication, electrical components, etc., can solve problems such as inability to use, complicated use process, and no installation, and achieve the effect of reducing dependencies and steps.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, so that those skilled in the art can better understand the present invention and implement it, but the examples given are not intended to limit the present invention.
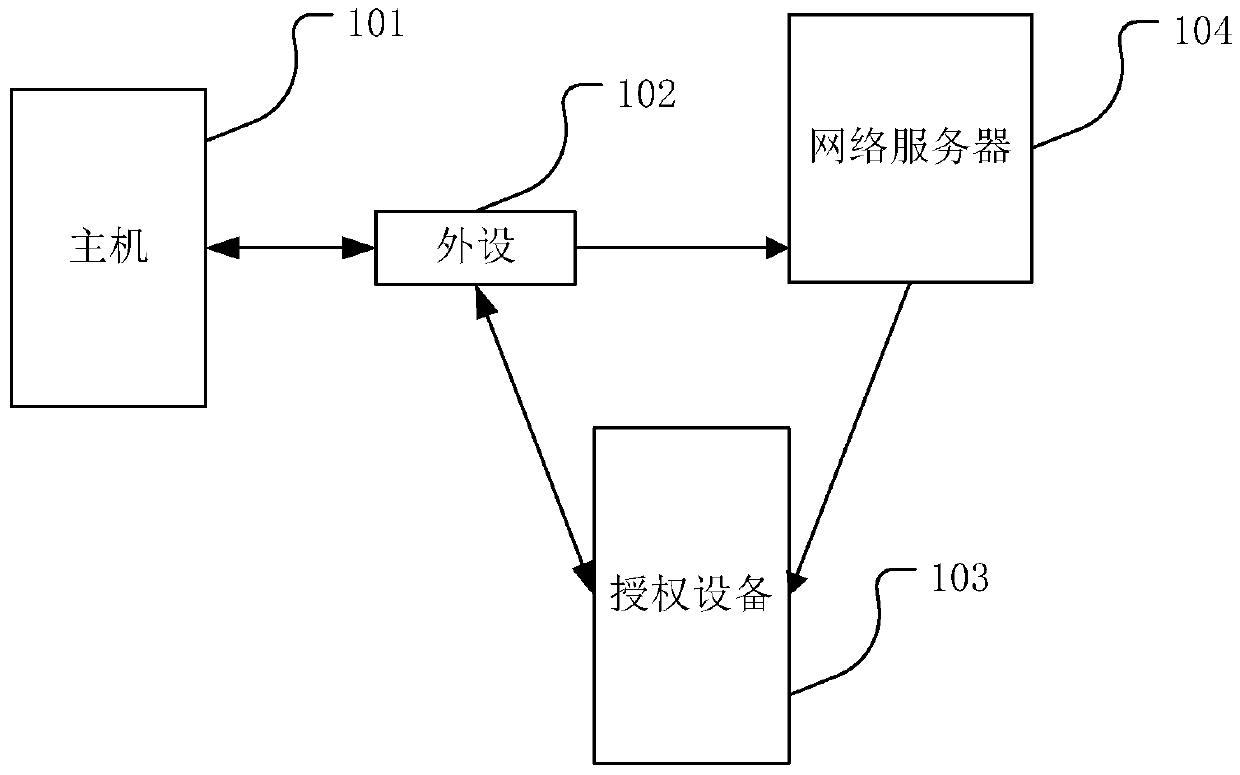
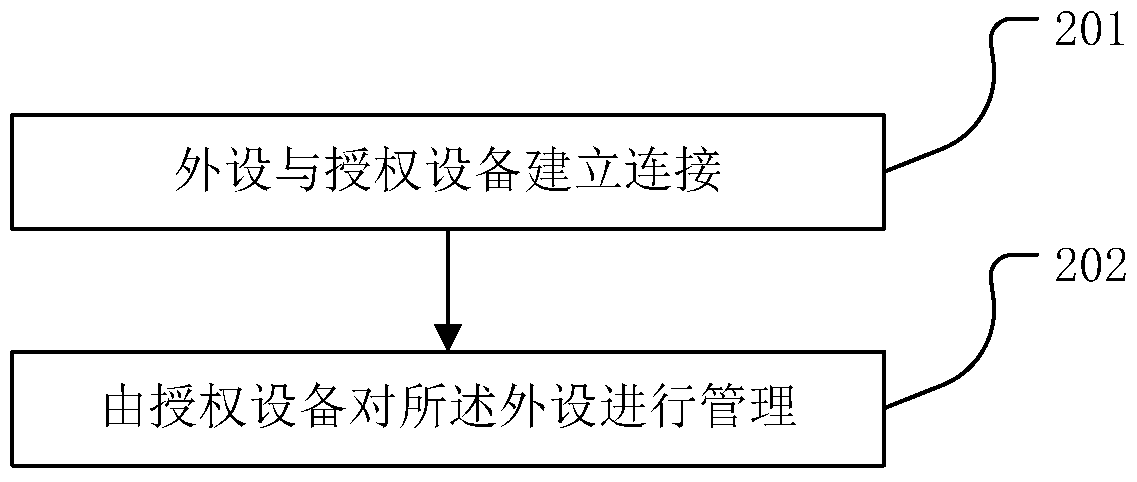
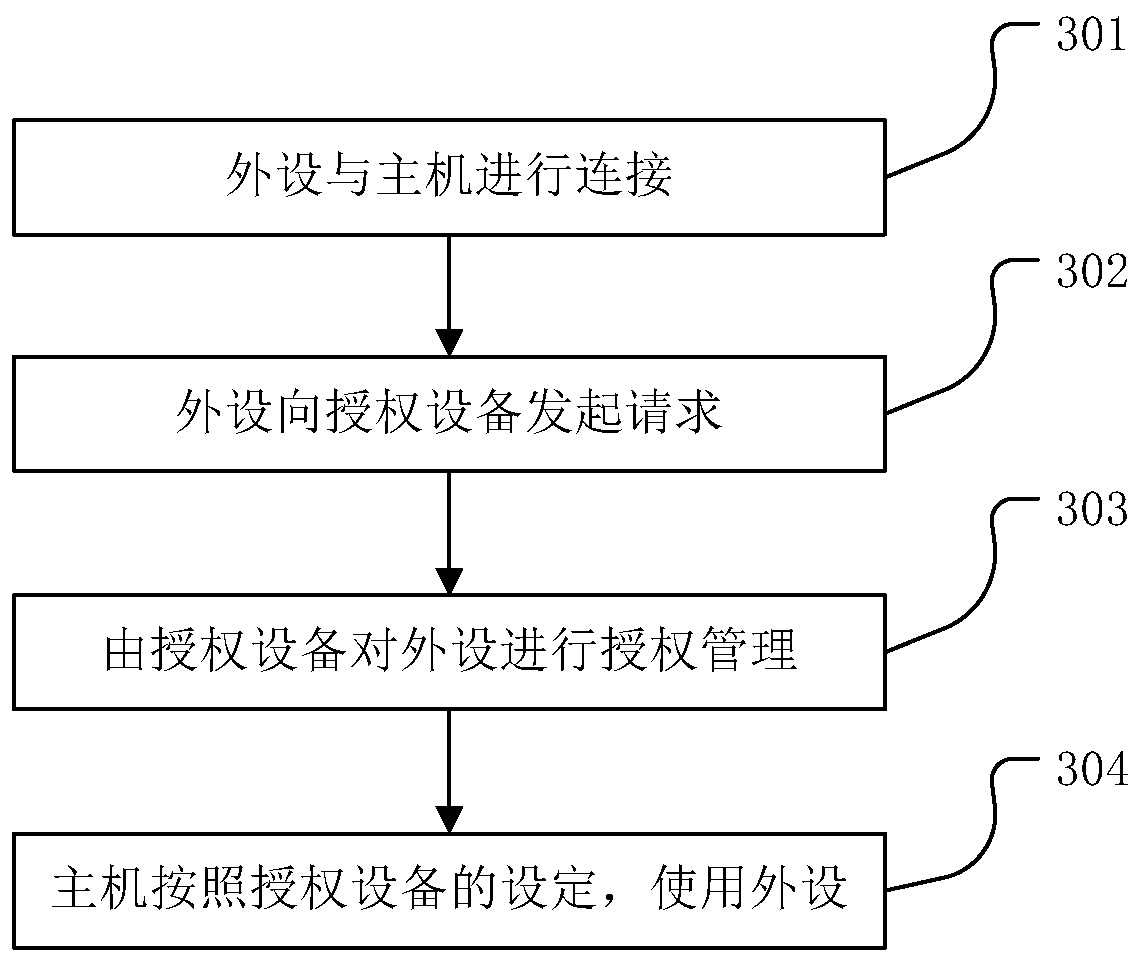
[0046] The core idea of the present invention is that, by adding special-purpose software or a combination of software and hardware for authorization on peripherals, and through various communication means (including but not limited to analog communication or data communication, such as cellular mobile network, Wifi, USB data connection) , Bluetooth, NFC, code generation, barcode or two-dimensional code scanning, photoelectric communication, etc.) for communication between software programs, through authorized devices (including but not limited to mobile phones, tablets, laptops, smart watches, etc.) to complete Device management such as device authorization, access control, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com