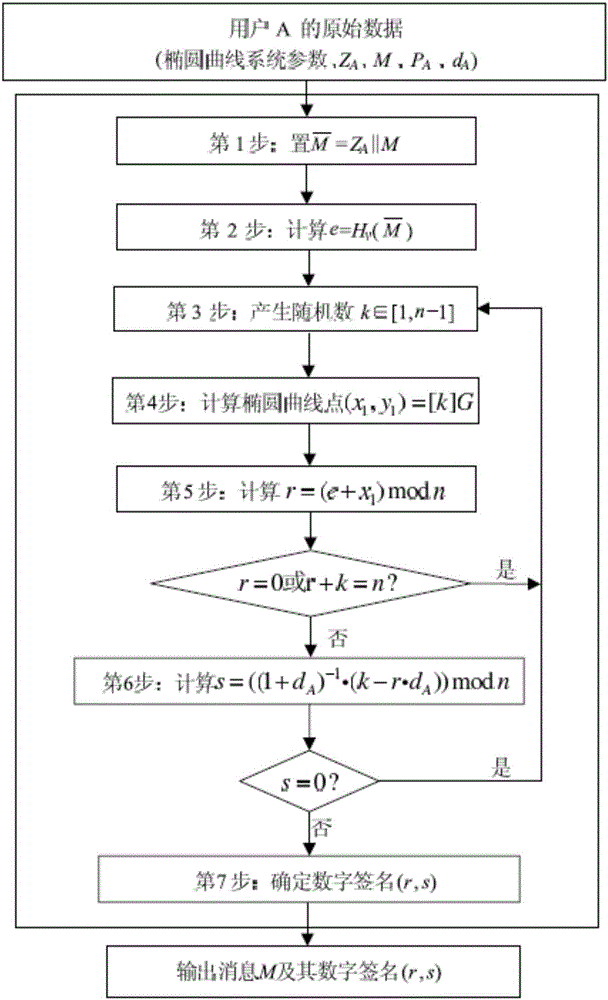
SM2 signature used large-number modular exponentiation inversion power dissipation measurement method and system thereof
A detection method and technology of power consumption, applied in the field of computer security, can solve problems such as narrow applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
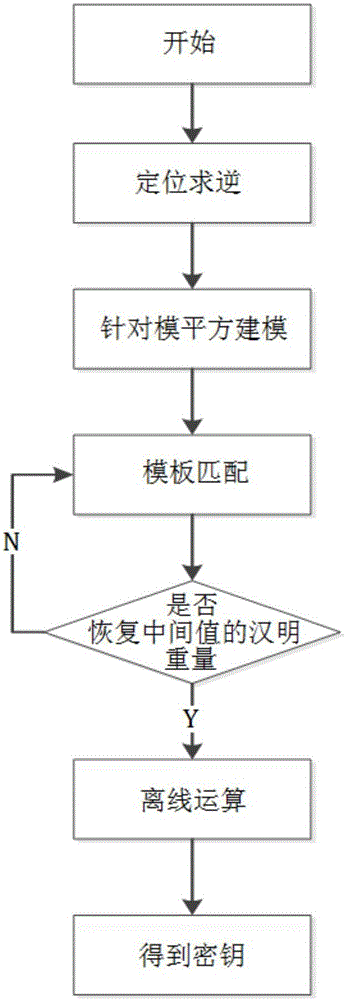
[0027] Such as figure 2 As shown, this embodiment includes the following steps:
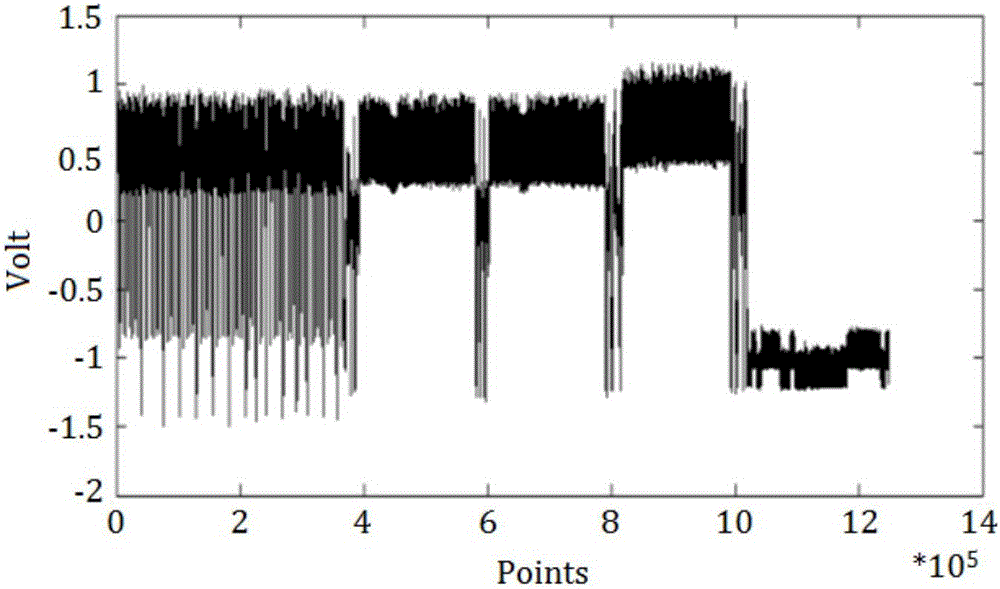
[0028] Step 1. Randomly input the key, execute the SM2 signature cyclically and locate the large number inversion stage, use the modular exponentiation algorithm to collect the power consumption curve, and calculate the intermediate value information of the modular square operation.
[0029] The intermediate value information of the modular square operation refers to: the single-byte Hamming weight of all intermediate results in the first modular square of the modular exponentiation algorithm.
[0030] Since the first modular squaring operation always has a direct relationship with the key, restoring the value can directly restore the key, so the intermediate value in the first modular squaring operation is selected.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com