Method and system for recognizing internet fraud behavior
A technology for identifying networks and behaviors, applied in the field of network security, can solve problems such as national and personal losses, and achieve the effect of rapid identification, convenient early warning and prevention of network fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
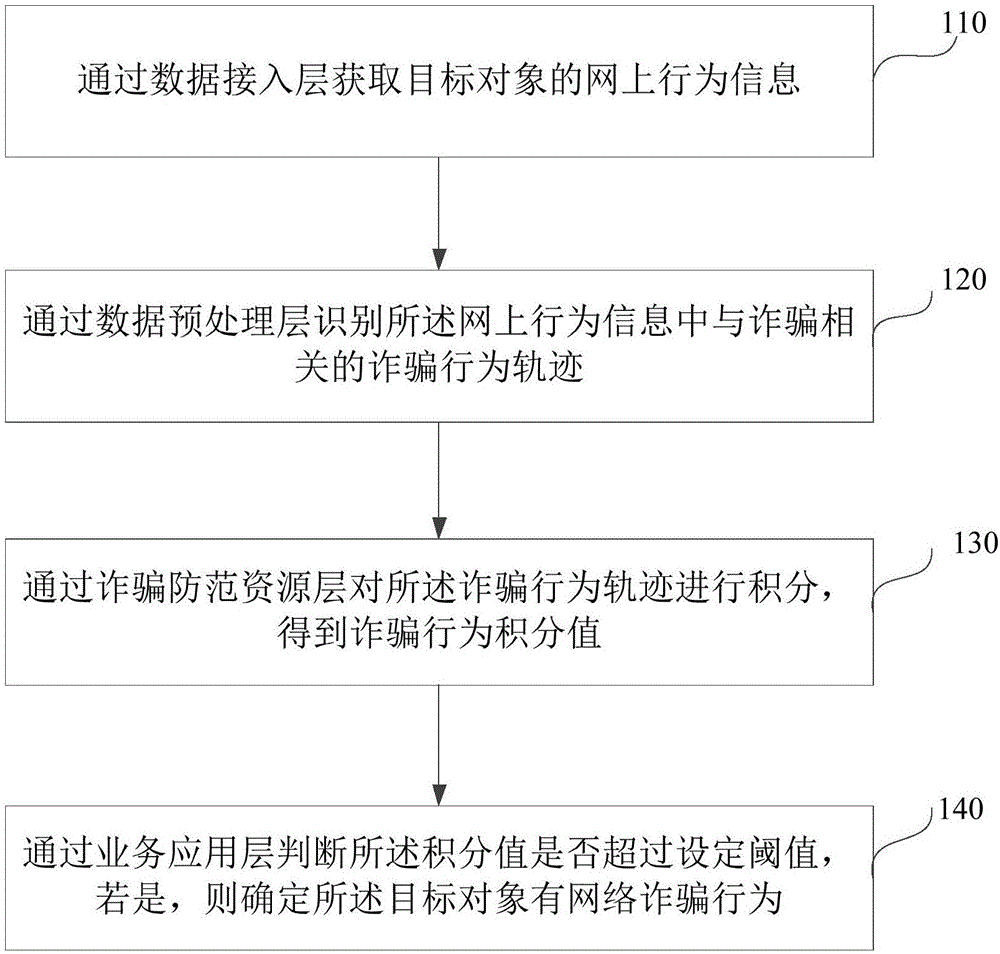
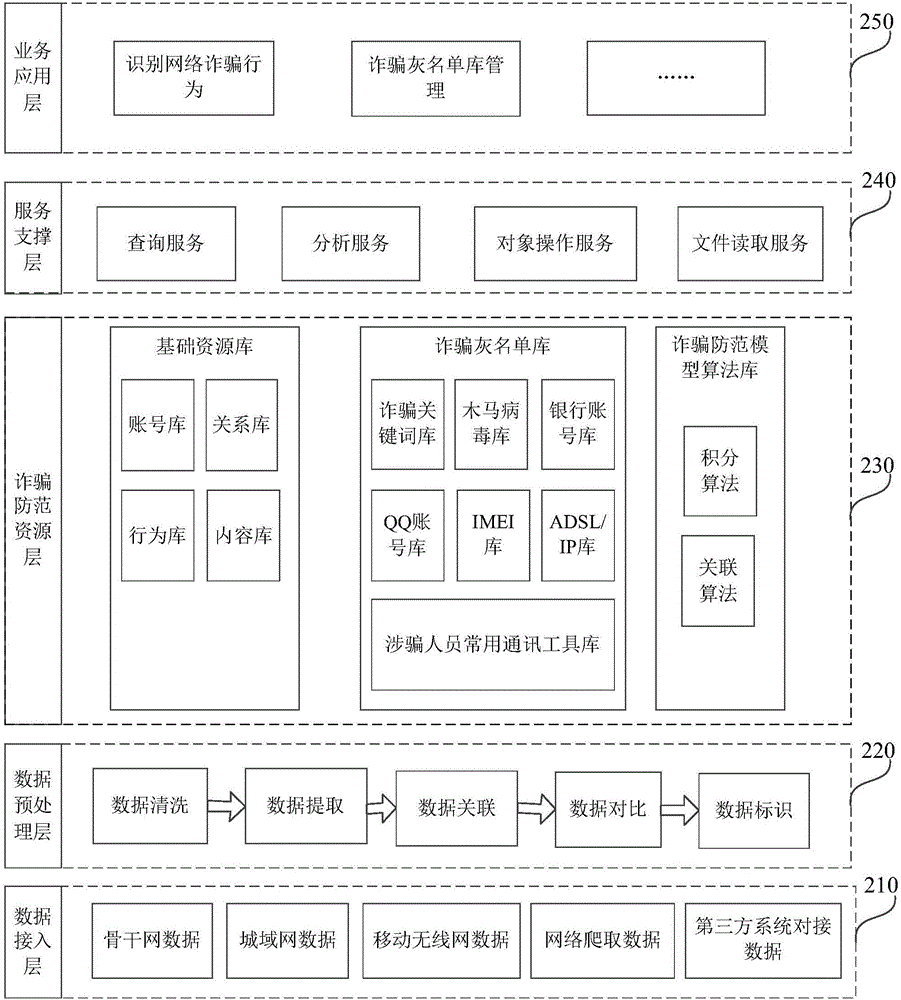
[0053] figure 1 It is a flow chart of a method for identifying network fraud provided by Embodiment 1 of the present invention. This method is applicable to the detection and prevention of network fraud by public departments, and can be executed by a system for identifying network fraud. The system can be realized by hardware and / or software, the system architecture such as figure 2 As shown, the system includes a five-layer structure, specifically: the data access layer 210, which is used to collect all data information interacted through the telecommunications network, mainly including backbone network data, metropolitan area network data, mobile wireless network data, and network Crawling data, third-party system docking data, etc.; data preprocessing layer 220, used to perform preprocessing operations such as cleaning, extraction, association, comparison, and identification of data accessed by the data access layer 210, wherein data cleaning is for The raw data accessed ...
Embodiment 2
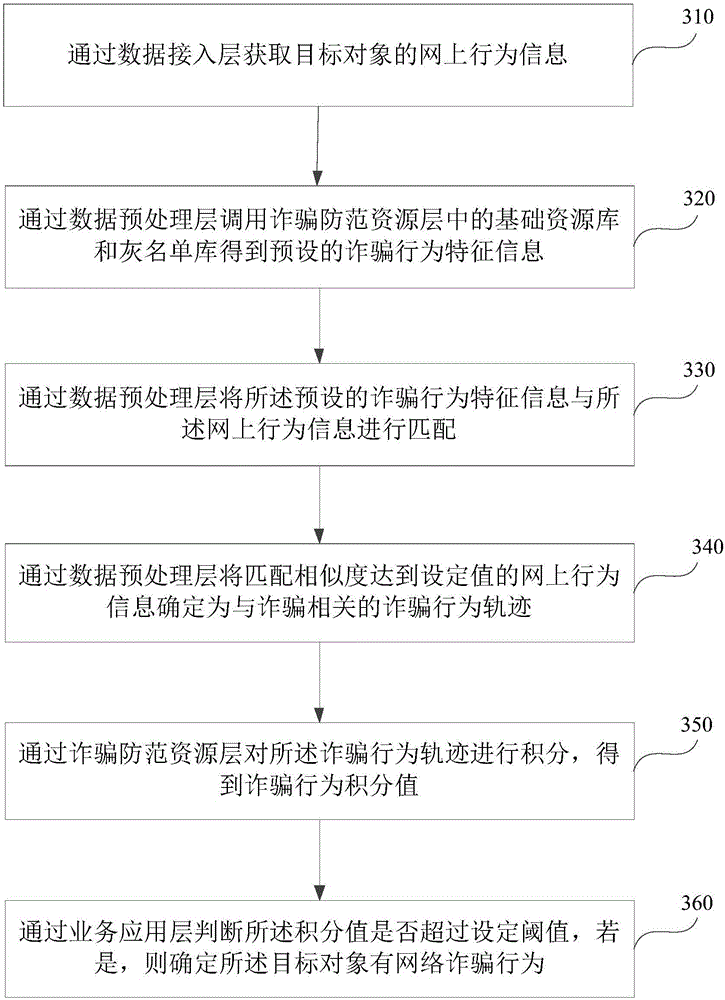
[0073] image 3 It is a schematic flowchart of a method for identifying online fraud provided by Embodiment 2 of the present invention. On the basis of Embodiment 1, this embodiment has been further optimized. The benefit of optimization is that it can accurately identify the online behavior information related to Fraud-related fraudulent behavior trajectories. For details, see image 3 As shown, the method specifically includes the following:
[0074] Step 310, acquiring the online behavior information of the target object through the data access layer.
[0075]Further, in order to improve the accuracy of identifying the trajectory of fraudulent behavior, after obtaining the online behavior information of the target object through the data access layer, it may also include:
[0076] The data of the online behavior information is preprocessed through the data preprocessing layer to facilitate the identification of fraudulent behavior tracks related to fraud in the online be...
Embodiment 3
[0087] Figure 5 A schematic structural diagram of a system for identifying network fraud provided by Embodiment 3 of the present invention, the system includes:
[0088] Data acquisition module 510, trajectory identification module 520, points calculation module 530 and fraudulent behavior identification module 540; wherein, data acquisition module 510 is configured in the data access layer for obtaining online behavior information of the target object; trajectory identification module 520, Configured in the data preprocessing layer, used to identify the fraudulent behavior trajectory related to fraud in the online behavior information; the integral calculation module 530, configured in the fraud prevention business layer, used to integrate the fraudulent behavior trajectory to obtain the fraudulent behavior Integral value; fraudulent behavior identification module 540, configured in the business application layer, is used to judge whether the integral value exceeds a set thr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com