GTP tunnel communication system and method
A technology of tunnel and corresponding relationship, which is applied in the field of wireless communication based on GTP tunnel, which can solve the hidden dangers of communication data security, etc., and achieve the effect of enhancing security and information complexity, improving security, and enhancing reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
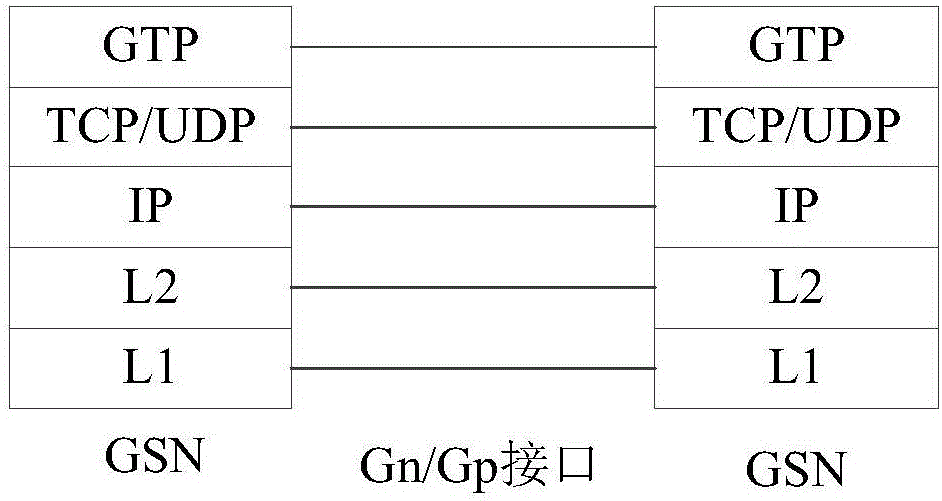
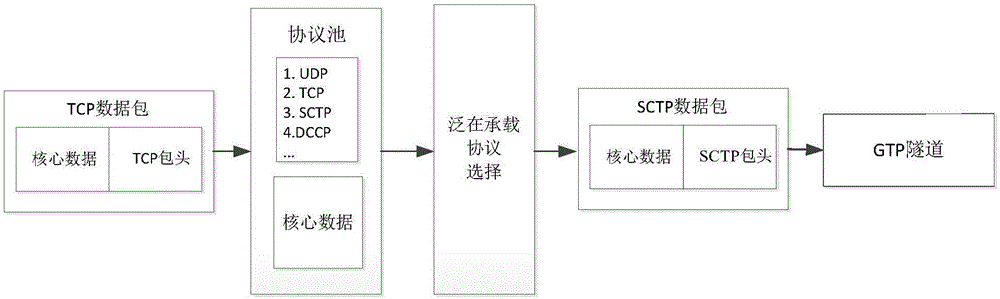
[0035] As mentioned above, there are increasingly higher requirements for the confidentiality of user data in the current communication field, and the GTP tunnel transmission protocol, as a transmission node between the access network and the core network, needs to improve the security of the protocol. The following will pass figure 1 and figure 2 The solution of using the GPRS tunneling protocol for communication in the prior art will be introduced.
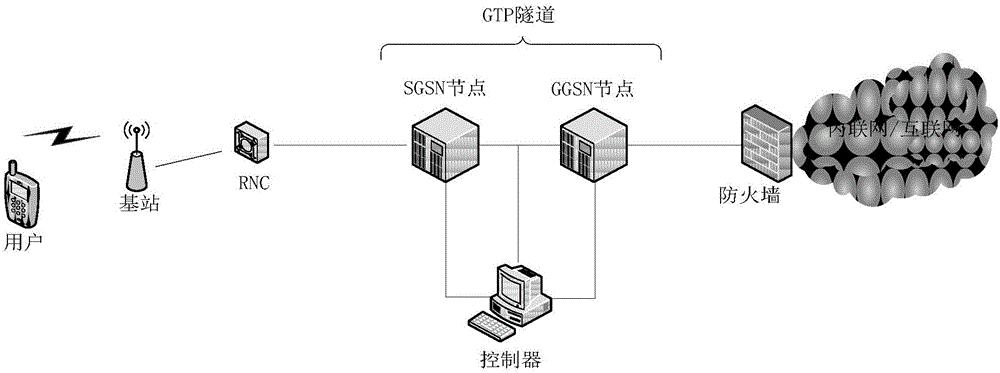
[0036] figure 1 A scene diagram of a GTP tunnel transmitting data in a protocol stack in the prior art is shown. exist figure 1 In the shown scenario, the user sends data to the base station (eNode B), and the base station sends the data to the communication core network including the radio network controller (RNC), and sends the data to the GTP tunnel through the RNC. The GTP Tunnel iden...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com